Threats Without Borders - Issue 171
Cybercrime Investigation Newsletter, Week ending February 25, 2024
I recently heard a cybersecurity personality explain why he didn’t like the term “cybercrime”. “It may be a new way to do it, but it’s still just crime”, he said. He also reiterated his preference for calling it "security" instead of "cybersecurity".
Yeah, yeah, I get it and I agree to a point. It is still crime, and we are just doing security. But there is so much more to it that it’s injustice to be so minimally flippant.
Consider a Distributed Denial of Service Attack on a website or Internet Service. Sure, at the end of the day, it’s just criminal mischief, or terrorism, or extortion. The classic crimes we all know and love.
But think about what is behind that attack. The attackers had to amass a large number of computer devices, creating a botnet. Consider the effort to infect thousands, or hundreds of thousands, of computer devices and maintain control of them. They use advanced software to launch the attack and control the digital army, which sends millions of packets per second to the target. The attacker must establish and communicate with the victim organization to relay instructions and demands. In most cases, they must also facilitate a financial transaction system to monetize the effort. And all while leaving no traces of their identity to maintain complete anonymity.
That’s a completely different ballgame than the 1930s mobster walking into a butcher shop and saying, “Nice shop you have here; sure would be a shame if you had a fire.” Suddenly, the butcher finds himself making a little extra payment each month for “Fire Protection Service”.
Extortion is extortion, and a crime is a crime, but crime delivered through Internet technology is surely different.
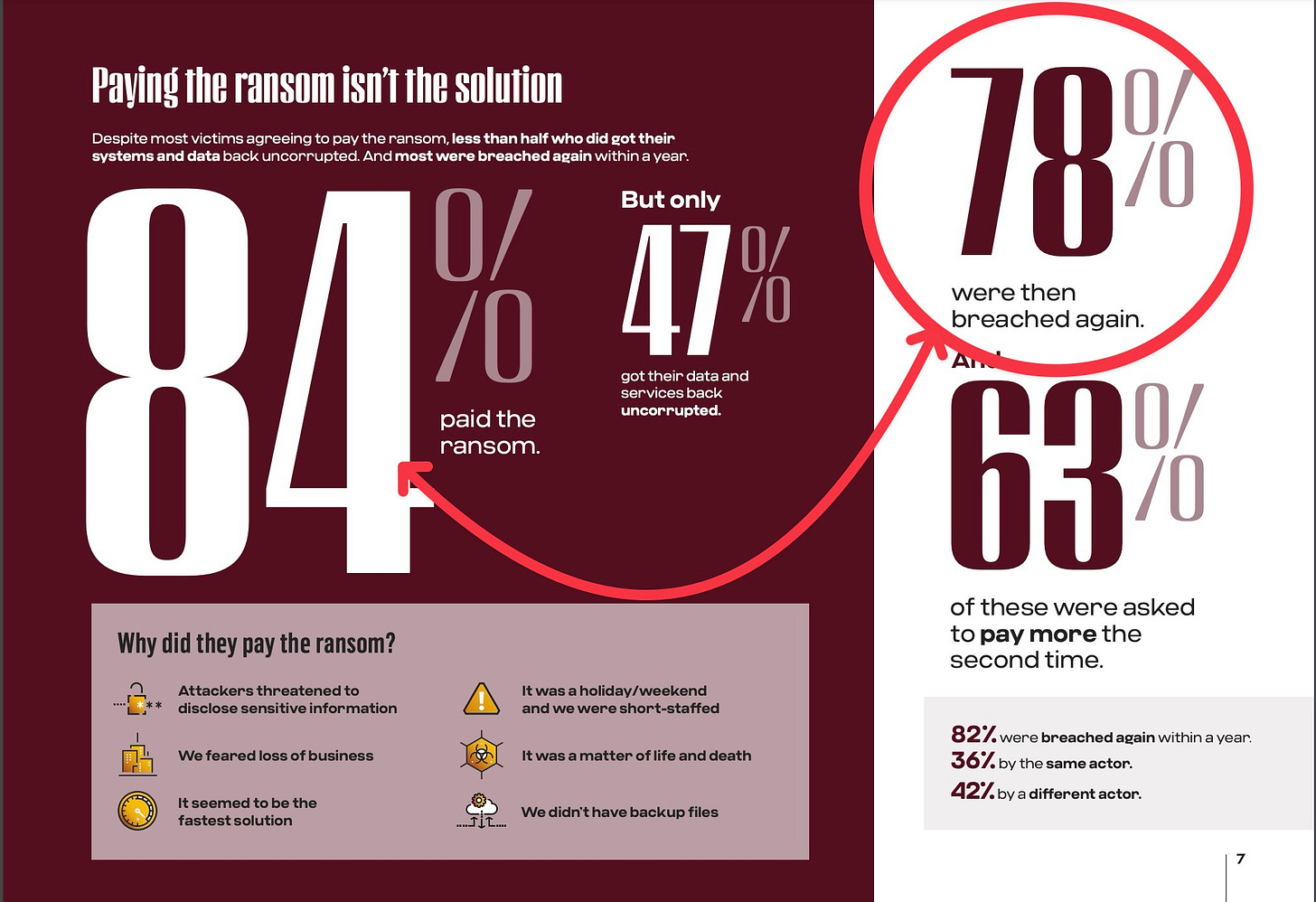
Cybereason released a report titled “Ransomware: The True Cost to Business, 2024,” which is based on a survey of 1,008 IT professionals whose organization had been breached “at least” once over the past year. The report is well-written and effectively displays the data. The one statistic that has me scratching my head is highlighted in this graphic:
No, my concern isn’t the statistic that 84% of those infected with ransomware submitted to the extortion. Nor is that only 47% of them could recover their data. It’s that 78% of the 84% (the ones that paid) were breached again within a year. 78% suffered a reinfection!
What causes this? Are the incident responders not effectively remediating the infection, and are they missing persistence mechanisms? Are they not patching and updating the vulnerabilities? Are organizations failing to properly train employees, resulting in repeated social engineering attacks?
That’s a shocking and sad finding.
https://www.cybereason.com/hubfs/dam/collateral/ebooks/Ransomware-True-Cost-2024-eBook.pdf
Some News…
Hopefully, you didn’t need to fill a drug prescription over the past week! UnitedHealthcare, the largest healthcare company in the U.S., has been dealing with a cyberattack that took down its prescription processing business, Change Healthcare. I saw in a news broadcast that Change processes the prescription orders for 1/3 of all patients in the United States. The suspected “nation-state” attack has left pharmacies nationwide unable to refill prescriptions. Many have resorted to record-keeping the old-fashioned way - with pen and paper and hoping to file the insurance claims when the system returns online. https://www.cnbc.com/2024/02/24/unitedhealth-subsidiary-change-healthcare-down-for-a-fourth-day-following-cyberattack.html
Federal regulators: “Hmm…does Cash App leave the door open for money launderers and terrorists?”. Whistleblower: “Yes!”. https://www.nbcnews.com/business/personal-finance/whistleblowers-cash-app-leaves-door-open-money-laundering-terror-rcna138958
As expected, within days of the “international law enforcement takedown” of the Lockbit ransomware group, they’re back. And more defiant than ever. The self-proclaimed leader of the groups released a statement, “All FBI actions are aimed at destroying the reputation of my affiliate program, my demoralization, they want me to leave and quit my job, they want to scare me because they can not find and eliminate me, I can not be stopped, you can not even hope, as long as I am alive I will continue to do pentest with postpaid.” It’s interesting to see that he refers to his work as a “pentest,” thereby conflating his criminal extortion tactic with legitimate security work. https://www.bankinfosecurity.com/ransomware-operation-lockbit-reestablishes-dark-web-leak-site-a-24442
Troy Hunt takes FedEx to task for their very phishy text messages. What goes through the minds of the legal and marketing department heads when one of the most well-known and respected cybersecurity personalities writes an entire post decrying your product? https://www.troyhunt.com/thanks-fedex-this-is-why-we-keep-getting-phished/
The Unit 42 Group from PaloAlto Networks released their 2024 Incident Response Report, and it’s a must-read. If you don’t have time to consume all 66 pages, at least read pages 21-27 where they deep dive into ransomware. https://www.paloaltonetworks.com/content/dam/pan/en_US/assets/pdf/reports/2024-unit42-incident-response-report.pdf
I want to be snarky, but I might be flying in a Spirit Airlines plane in the future. So, I’ll leave this without comment: Spirit Airlines employee sentenced for running a $260K scam. https://www.pennlive.com/news/2024/02/ex-pa-airline-worker-nets-prison-time-for-260k-plus-flight-changing-scam.html
The Federal Trade Commission has fined antivirus provider Avast 16.5 million dollars after it was determined the company was unlawfully selling user data. The user must ask: Was the prevention more damaging than the potential disease? https://www.ftc.gov/news-events/news/press-releases/2024/02/ftc-order-will-ban-avast-selling-browsing-data-advertising-purposes-require-it-pay-165-million-over
Cool Job
Head of Fraud - Northwest Bank. https://recruiting.ultipro.com/NOR1002NWSAV/JobBoard/bf8580a6-c177-4bd6-9c3d-ccd66f56cb4b/OpportunityDetail?opportunityId=03e3ee6a-3a34-409e-a9f6-3b548c1e39a4
Cool Tool
A slightly more sophisticated Urban Dictionary - Untranslatable. https://untranslatable.co/
Irrelevant
15 different burger recipes. Try them all. https://www.seriouseats.com/hamburger-recipes-7814305
Thanks for opening this week’s newsletter and making it this far down the page. I appreciate you giving me a few minutes of your day! Sharing the newsletter with your colleagues is always appreciated.
See you next Tuesday!
Matt
“NO ONE CAN MAKE YOU FEEL INFERIOR WITHOUT YOUR CONSENT.” - I must have my consent printed on my jacket.
Published every Tuesday, Threats Without Borders offers original commentary and educational pieces related to cybercrime investigations and information security topics. We also summarize and comment on news articles concerning active threat intelligence for the financial industry. The newsletter interests everyone tasked with cybersecurity or involved in preventing or investigating technology-enabled fraud, theft, or money laundering.
Legal: I am not compensated by any entity for writing this newsletter. Obviously, anything written in this space is my own nonsensical opinion and doesn’t represent the official viewpoint of my employer or any associated organization. Blame me, not them.