Threats Without Borders - Issue 182
Cybercrime Investigation Newsletter, week ending May 12, 2024
I recently assisted a colleague in investigating a suspicious website, and we found some useful information in the robots.txt file.
Don’t forget to look at this resource during your investigations!
Web crawlers from Google, Bing, and DuckDuckGo are automated robots that search the internet for information, catalog it, and index it for future use.
The robots.txt page is typically the first page a web crawler visits to obtain the permissions set by the site owners. Cloudflare describes this file as a "Code of Conduct" sign posted on the wall of a gym, bar, or community center. The sign itself cannot enforce any rules, but well-behaved visitors will follow them, while misbehaving ones are likely to break them and face the consequences such as being banned.
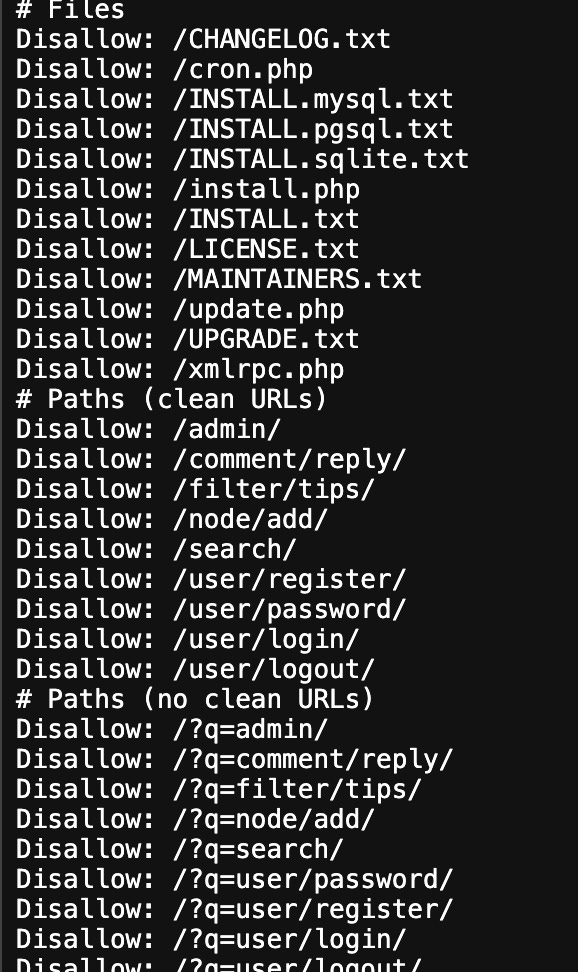
Many web designers choose to include a robot.txt page on their website, which reveals their established rules. If a page is marked "disallow," the site owners don't want the content to be cached by search engines and want to protect it. These pages are often excluded from site menus as well. It's important to pay attention to these pages when conducting investigations.
To access the robot.txt file, append the main website URL with “/robot.txt” after the root domain. For example, CNN's robots.txt page is at https://www.cnn.com/robots.txt, and Fox News's is at https://www.foxnews.com/robots.txt. This works on almost all root domains.
Take a look at the robots.txt file of the United Nations website at https://www.un.org/robots.txt. It lists which pages are allowed to be crawled and which are off-limits.
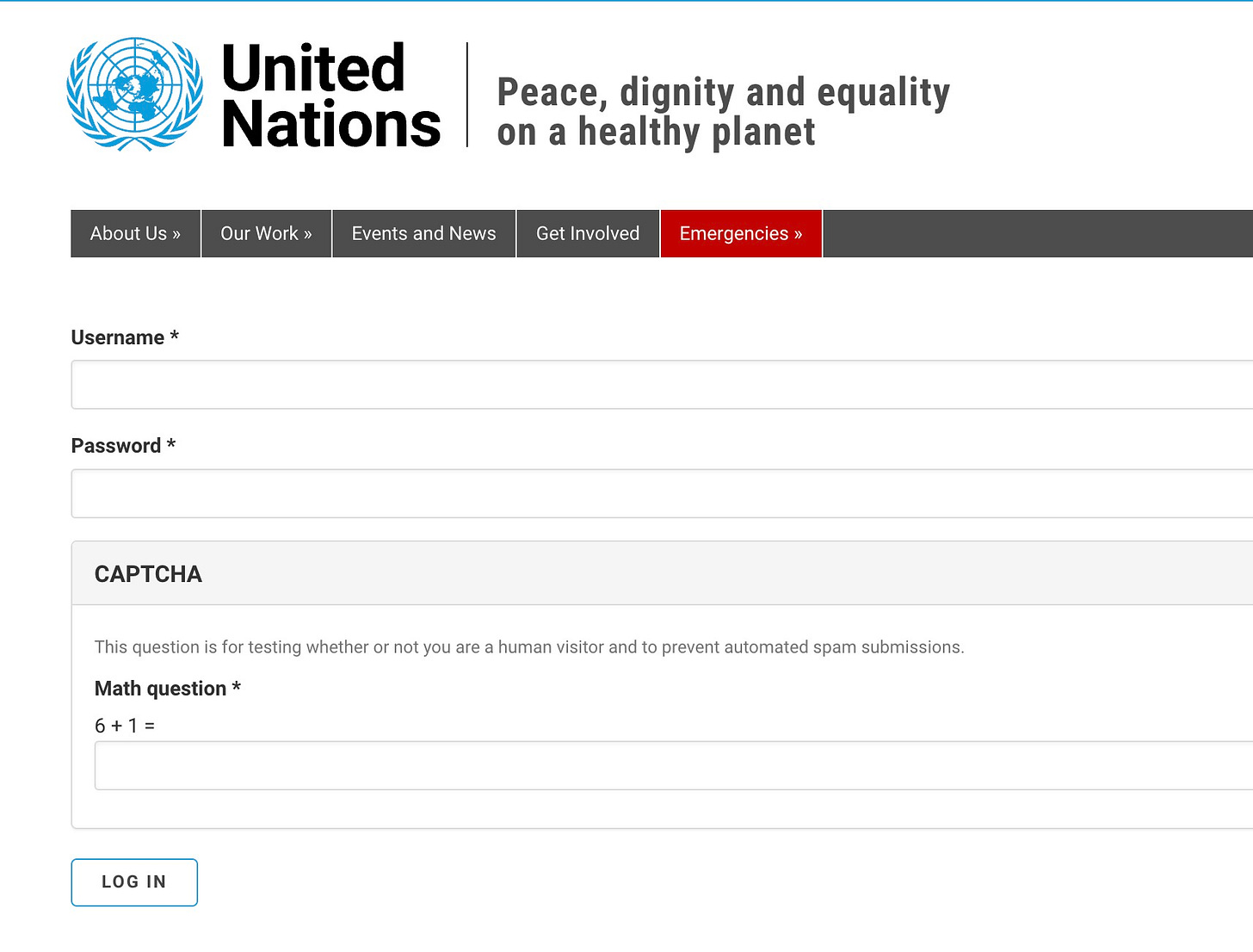
One of the pages marked off-limits for crawlers is /user/login, and no link is available on the live page. However, you can access it by manually entering the URL un.org/user/login. This login page is intended for users with special privileges to access various resources within the website. They want to obscure this login page, which is not readily visible on the website.
The robots.txt page can also provide information on where the website's sitemap is located. Knowing the sitemap's location can be helpful during investigations as it can help you discover additional pages not listed on the site's menus. Sitemaps are typically written in XML and easily display in your web browser. For example, https://www.cnn.com/sitemaps/cnn/index.xml.
For additional information about the robots.txt page, check out https://www.robotstxt.org/robotstxt.html
Some News
The Linux Foundation estimates that 70-90% of all software comprises some element of open-source code. This article won’t leave you feeling good about that. https://gizmodo.com/open-source-cybersecurity-is-a-ticking-time-bomb-1848790421
Dell Computers has confirmed that a data breach resulted in the loss of information for 49 million customers. They have emphasized that the stolen information did not include any payment or financial information. However, the compromised data included customers' names, physical addresses, Dell hardware and order information, as well as service tags, item descriptions, order dates, and related warranty information. Well, I guess I just got another year of credit monitoring. https://www.pcworld.com/article/2328519/dell-data-breach-includes-your-id-and-detailed-hardware-info.html
Late Update - Dell hacker claims they had access to the network for three weeks!!! https://www.itpro.com/security/data-breaches/dell-hacker-claims-they-had-access-to-systems-for-nearly-three-weeks
Just a reminder that ALL network access needs to be cut before the soon-to-be terminated employee gets that call from HR. This company terminated an IT contractor before they could cut off his access to their network. The contractor used his company-issued laptop to download confidential and proprietary information from the company's network, including architectural maps, trade secrets, and lists of potential vulnerabilities. He then threatened to publicly disclose this sensitive information unless the company agreed to pay him up to $1.5 million as a settlement for his claims of employment discrimination. https://www.justice.gov/usao-sdny/media/1350231/dl
Introducing Google Threat Intelligence - https://cloud.google.com/blog/products/identity-security/introducing-google-threat-intelligence-actionable-threat-intelligence-at-google-scale-at-rsa
Make sure you're sending that cryptocurrency to the correct address. Especially if you’re sending 70 MILLION DOLLARS! https://www.businessinsider.com/bitcoin-trader-loses-millions-address-poisoning-scam-crypto-eth-finance-2024-5
Canary Tokens are a fantastic - and free - way to signal you have a threat within your network. Think of them as an alarmed jar of chocolate chip cookies on the counter. The cookie monster can’t walk by the jar without taking a cookie. Or, as explained in this how-to, “canary tokens work by generating alerts when they are triggered. They are designed to look like enticing targets for attackers, such as documents, URLs, email addresses, or other digital assets. When an attacker interacts with or accesses a canary token, it triggers an alert, providing defenders with valuable information about potential threats” https://dfir.ch/posts/canarytokens/
Cool Job
Senior Manager of Information Security - Jack Henry. https://careers.jackhenry.com/job/united-states/senior-manager-of-information-security/42859/64992985968
Chief of Computer Forensics - U.S. Department of Justice. https://www.usajobs.gov/job/790447600
Cool Tool
For Mac users - https://sindresorhus.com/camera-preview
Irrelevant
Climate activist - “No more gas vehicles, we have to transition to electric cars NOW”. Same climate activists - “Let’s destroy this factory that makes electric vehicles because they cut down trees to build it”. https://www.cnbc.com/2024/05/10/climate-protesters-try-to-break-into-tesla-germany-factory-police.html
Training Event
ACAMS - Delaware Chapter: “Across the Cryptoverse - Tracing Crypto”. May 20, 2024 from 6-8PM, Live in Wilmington. https://www.acams.org/en/chapters/united-states-northeast/acams-delaware-chapter-may-2024-event-across-the-crypto-verse-part-ii-tracing-crypto
Late Breaking News
The U.S. Securities and Exchange Commission has proposed new rules that require registered investment advisers (RIAs) and exempt reporting advisers (ERAs) to collect certain personal details from their customers in order to comply with anti-money laundering regulations. https://www.yahoo.com/news/us-financial-regulators-propose-anti-165057212.html
Thanks for reading another issue, and a special welcome to our new subscribers! I am fully aware of your valuable time, and it’s humbling that you spent a few minutes here.
See you next Tuesday!
Matt
“YOU CAN’T BE A GENIUS AT SOMETHING WITHOUT BEING A BIT OF A MORON AT SOMETHING ELSE.” - just being a moron at everything is OK too.
Published every Tuesday, Threats Without Borders offers original commentary and educational pieces related to cybercrime investigations and information security topics. We also summarize and comment on news articles concerning active threat intelligence for the financial industry. The newsletter interests everyone tasked with cybersecurity or involved in preventing or investigating technology-enabled fraud, theft, or money laundering.
Legal: I am not compensated by any entity for writing this newsletter. Obviously, anything written in this space is my own nonsensical opinions and doesn’t represent the official viewpoint of my employer or any associated organization. Blame me, not them.