Threats Without Borders - Issue 204
Cybercrime Investigation Newsletter, Week ending October 13, 2024
At both work and home, I have noticed a huge increase in TOAD attacks—Telephone Oriented Attack Delivery—also known as Callback Phishing. This attack usually starts with a phishing email that appears to be from a reputable company. The email alerts the recipient of a potential issue and instructs them to call a specific phone number provided in the email, of course.
An attacker, trained in social engineering, answers the phone call and tricks the victim into providing their account credentials or installing remote access software to gain control of the computer.
This is an excellent example of a callback phishing message that I use in my classes to teach how to identify the warning signs of a TOAD phishing attack:
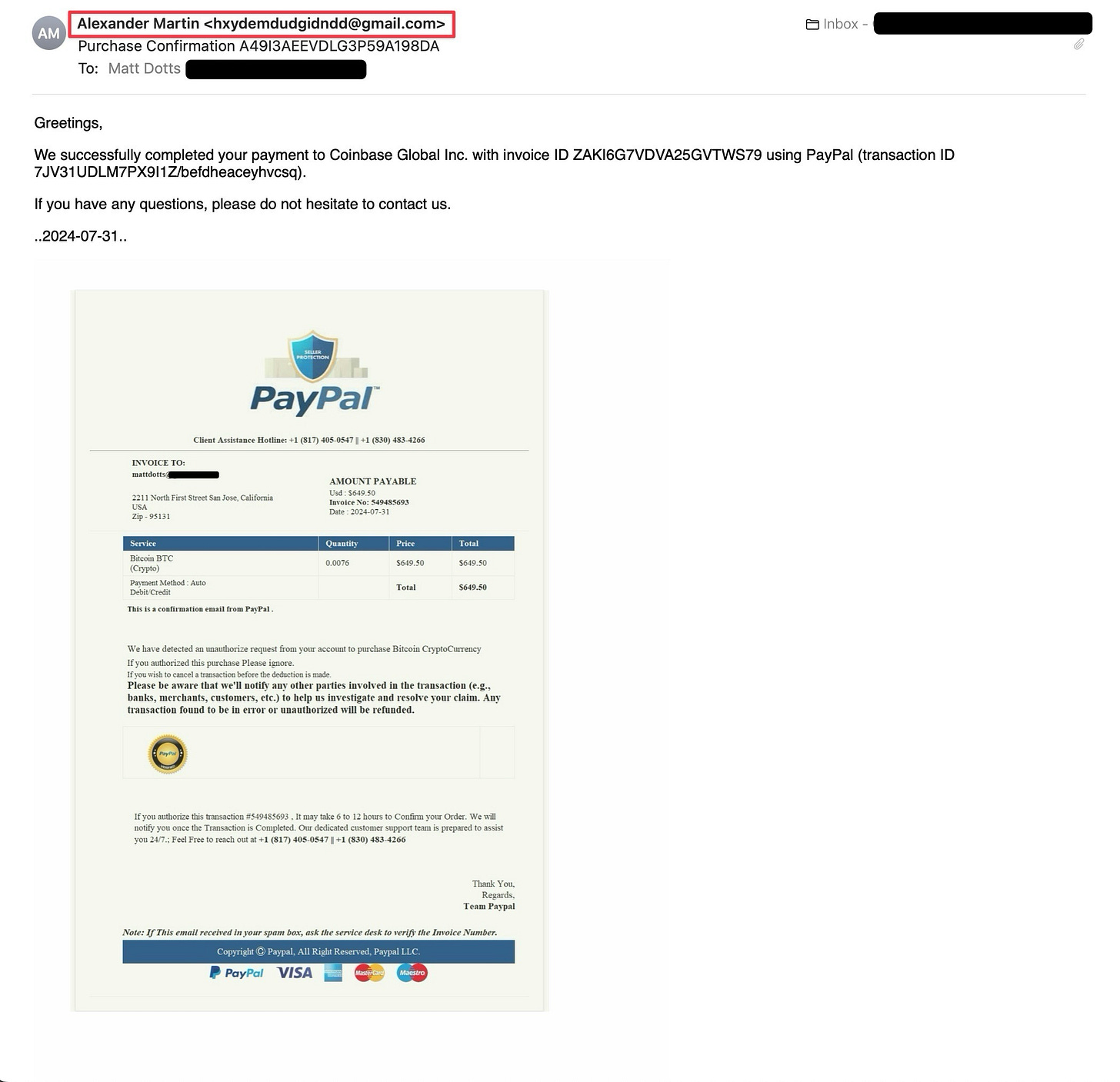
On the face of it, it's PayPal confirming a payment transfer for a purchase of Bitcoin from Coinbase. But wait, why would PayPal send me an invoice from someone's personal Gmail account? And even more concerning, who would select that jumbled string of characters for an email address? Can you imagine trying to type that out every time you need to provide an email address?
Let’s dig deeper into the attached invoice and uncover all the red flags:
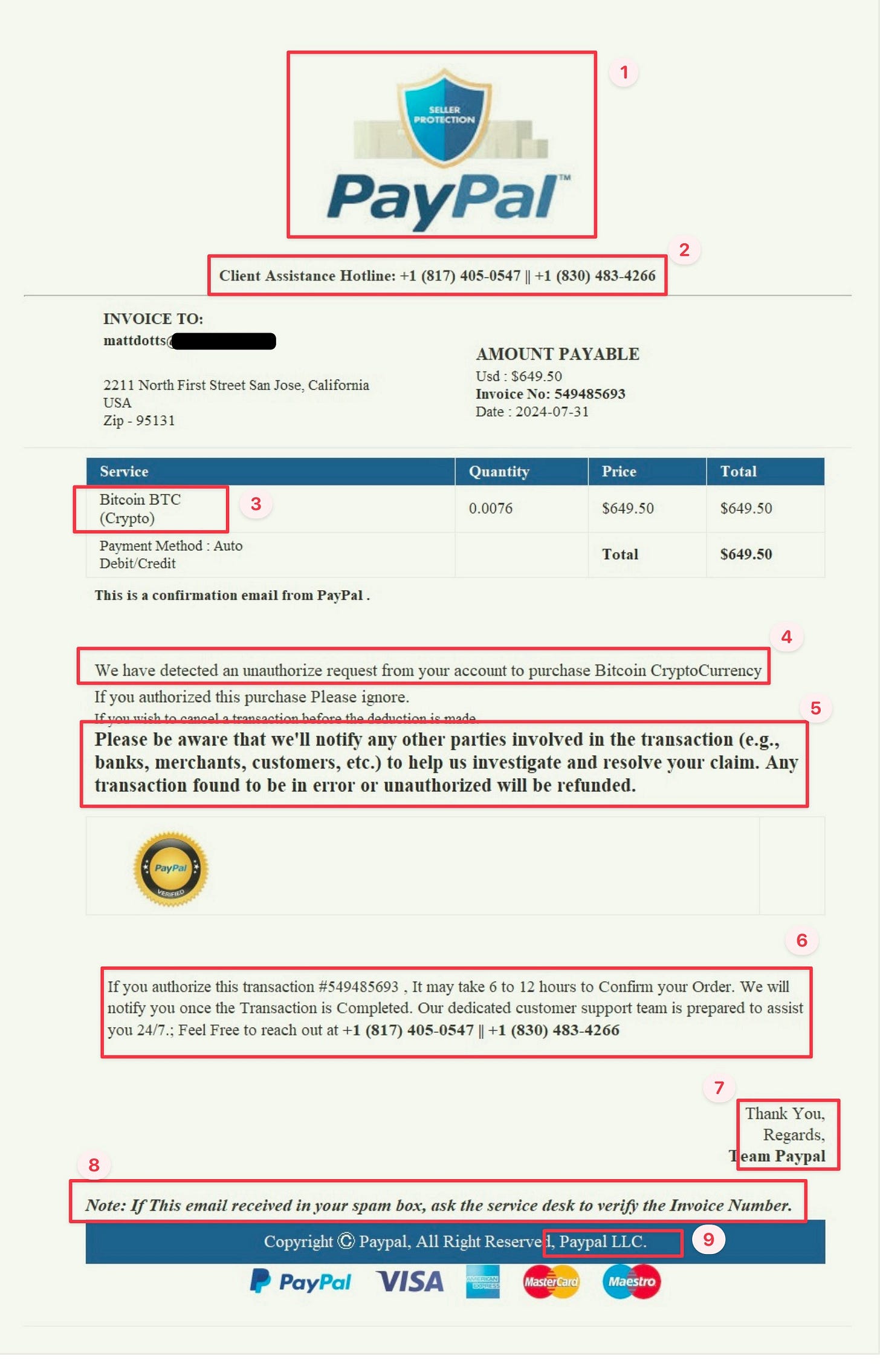
That’s a really poor PayPal logo.
They provide not just one assistance phone number but two! Most organizations do everything they can to keep customers off the phone lines and push them into chat-based support. It almost seems as if they want you to call!
How does PayPal know what was precisely purchased? Does Coinbase share that? Shouldn’t it just list the merchant and dollar amount?
This is a big one! The original message in the email body says, “We successfully completed your payment transfer,” but here, they claim to have “detected an unauthorized request.” OK, which is it? If you know it’s unauthorized, why would you complete it?
Dealing with fraudulent purchases can be a time-consuming and frustrating process that requires multiple phone calls to all of the involved parties. This language is the “hook” essentially saying, “Call us, and we’ll take care of everything”.
Now they set up a sense of urgency - you only have 6-12 hours to cancel it. Again, they invite you to call and provide two phone numbers.
Double closing salutations of Thank You, and Regards. They also misspell their name as Paypal, not PayPal.
Provides reassurance should your email provider correctly send it to the spam box. Spoiler Alert - they will validate any number you give them.
Again, the wrong name and also refers to the business as an LLC. PayPal is a billion-dollar, multi-national corporation that is not registered as an LLC.
The email is cleverly designed to trick the recipient into believing their account has been used to purchase cryptocurrency, and they have only 6-12 hours to cancel the purchase and repair their account.
The quickest and easiest way to rectify the problem is to call the provided phone numbers.
But calling the phone numbers only results in the caller being socially engineered into providing their PayPal credentials to the attacker or in the installation of remote desktop software onto their computer.
A loss in either case.
The News…
It’s nice to be reminded that good men and women are still with the FBI doing outstanding work in the cyber and financial crime realm. I can’t say enough about how awesome this investigation is. The investigators created a market-traded cryptocurrency to take down a group of market manipulators known as “Wash Traders”. From the news release: “This investigation, the first of its kind, identified numerous fraudsters in the cryptocurrency industry. Wash trading has long been outlawed in the financial markets, and cryptocurrency is no exception. These are cases where an innovative technology – cryptocurrency – met a century old scheme – the pump and dump”. Fantastic work and kudos to all involved! https://www.justice.gov/usao-ma/pr/eighteen-individuals-and-entities-charged-international-operation-targeting-widespread
It’s terrible that this needs to be said. Still, the Federal Trade Commission (FTC), Department of Justice (DOJ), and Consumer Financial Protection Bureau (CFPB) are warning consumers about potential scams and price gouging in the wake of hurricanes Helene and Milton. https://www.ftc.gov/news-events/news/press-releases/2024/10/ftc-doj-cfpb-warn-consumers-about-potential-scams-price-gouging-wake-hurricanes-other-natural
The United Nations Office of Drugs and Crime has published a new report documenting the adoption of technology by organized crime groups to conduct cyber-enabled fraud in Southeast Asia. You can easily replace “Southeast Asia” with any other geographic location. Unsurprisingly, the report is not kind to Telegram. https://www.unodc.org/roseap/uploads/documents/Publications/2024/TOC_Convergence_Report_2024.pdf
TD Bank has been hit with a 3 BILLION dollar fine for laundering money for drug cartels. https://www.cnn.com/2024/10/10/investing/td-bank-settlement-money-laundering/index.html
In collaboration with the Global Anti-Scam Alliance (GASA) and the DNS Research Federation (DNSRF), Google has launched the Global Signal Exchange (GSE) to tackle online scams and fraud, aiming to serve as a worldwide hub for these issues. As part of the GSE pilot, Google has shared over 100,000 URLs related to fraudulent online shops and intends to include data from other relevant product areas. The company also claims that its Cross-Account Protection tool, which fosters cooperation among platforms to combat abuse, is safeguarding 3.2 billion users. https://blog.google/technology/safety-security/the-new-global-signal-exchange-will-help-fight-scams-and-fraud/
Education Sector - Look!
SROs and those working in cyber within an educational organization know all too well about the lengths students will go to bypass security restrictions.
This new website “unblocker” service makes it almost too easy for students to bypass network filters; it even masks traffic to appear as if it’s educational resources like math tutoring websites.
Cool Tool
“Busy Status Bar is a productivity multi-tool device with an LED pixel screen. Displays a personal busy message. Built-in Pomodoro timer and Apps. Fully customizable, open-source, and hacker-friendly.” https://busy.bar/
RevEye - reverse image search from the browser. https://chromewebstore.google.com/detail/reveye-reverse-image-sear/keaaclcjhehbbapnphnmpiklalfhelgf
Cool Job
Vulnerability Threat Management Associate - National Football League. https://job-boards.greenhouse.io/nflcareers/jobs/4137720008?gh_src=384ee6888us
Irrelevant
Stop ignoring your high performers - or lose them to an organization that doesn’t.
In every organization, high performers are the driving force behind innovation, productivity, and excellence. They consistently exceed expectations, push boundaries, and inspire those around them. Yet, despite their critical importance to an organization’s mission and bottom line, high performers, who are generally 400% more productive than an average employee (and as high as 800% more productive in highly complex occupations, such as software developers), are often overlooked. Instead, managers focus on under-performers who demand immediate intervention. This unbalanced attention is costly, leading to disengagement, frustration, and ultimately, the loss of top talent.
https://hbr.org/2024/10/stop-ignoring-your-high-performers
Instead of watching your sports team lose…
Practice your OSINT skills with the 2024 Cybersecurity Awareness Month Challenge from Huntress. https://huntress.ctf.games/
Sign Off
The Substack smartphone application is a great way to consume newsletters on the platform. Best of all, you’re not reliant on an email provider to ensure the newsletters are delivered.
Thanks for hanging around another week. See you next Tuesday!
Matt
“TRYING TO BE SOMEONE ELSE IS THE WASTE OF THE PERSON YOU ARE.”
Published every Tuesday, Threats Without Borders offers original commentary and educational pieces related to cybercrime investigations and information security topics. We also summarize and comment on news articles concerning active threat intelligence for the financial industry. The newsletter interests everyone tasked with cybersecurity or involved in preventing or investigating technology-enabled fraud, theft, or money laundering.
Legal: I am not compensated by any entity for writing this newsletter. Obviously, anything written in this space are my own nonsensical opinions and doesn’t represent the official viewpoint of my employer or any associated organization. Blame me, not them.
cybercrime fraud cyber investigations cyficrime aml osint cybe financial crime