Threats Without Borders - Issue 216
Cybercrime Investigation Newsletter, week ending January 5, 2025
Welcome, new subscribers. We are currently in a series exploring the value of web domains to our investigations.
Web domains are overseen by the Internet Corporation for Assigned Names and Numbers (ICANN), a nonprofit organization that coordinates and maintains the global domain name system. You acquire a domain through a domain registrar. Some popular options include GoDaddy, Domains.com, and Namecheap, although there are many others. Several website hosting services, including Squarespace, WordPress, and Wix, also function as registrars.
Buying a domain is as easy as picking a registrar, selecting an available domain, and finishing the registration and payment process.
WHOIS (pronounced "who is") is a protocol for querying databases that store information about registered domain names. This information is crucial for domain management, cybersecurity, and legal purposes.
The data obtained from WHOIS resources typically includes information about the domain registrant (owner), as well as administrative and technical contacts, domain registration and expiration dates, and name servers. This information serves several purposes, including verifying domain ownership, facilitating communication between domain owners and others, and helping to resolve technical issues.
WHOIS used to be a gold mine of information; however, privacy concerns have led to the development of WHOIS protection services, which mask personal information from public view while maintaining the integrity of the registration data. Data protection rules like GDPR in Europe and the California Consumer Privacy Act (CCPA) here in the states have sealed the most valuable information. Still, there is information that is critical in cyber investigations.
Important…ICANN is transitioning away from WHOIS to a more modern protocol called RDAP – Registration Data Access Protocol. This change will happen sometime in 2025. You can learn more about RDAP at https://docs.domaintools.com/rdap-faq.
But for now, WHOIS is still vital to us.
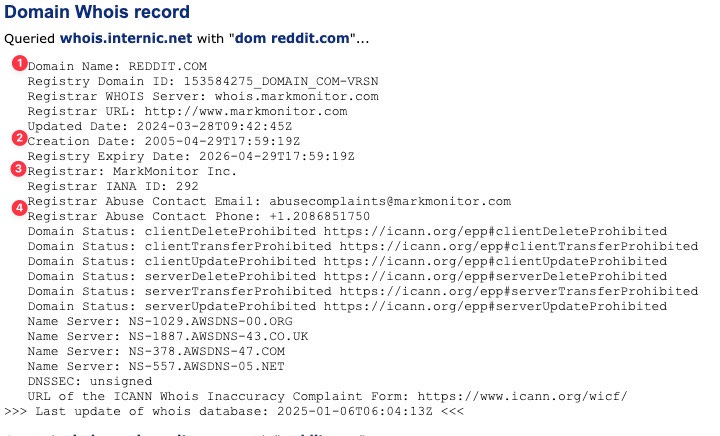
1- The domain name
2 - Dates are essential for investigations. For instance, if a company boasts on its website that it has been in operation for 25 years yet only registered the domain two weeks prior, that’s a red flag.
3—The official Registrar. File court orders against this company when you need non-public DNS-related information, such as the domain owner's identification!
4 - The abuse contact is where you can report fraud events using the domain and request the DNS records be pulled.
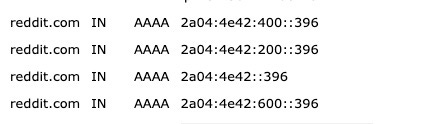
WHOIS also provides the IP addresses associated with the domain.
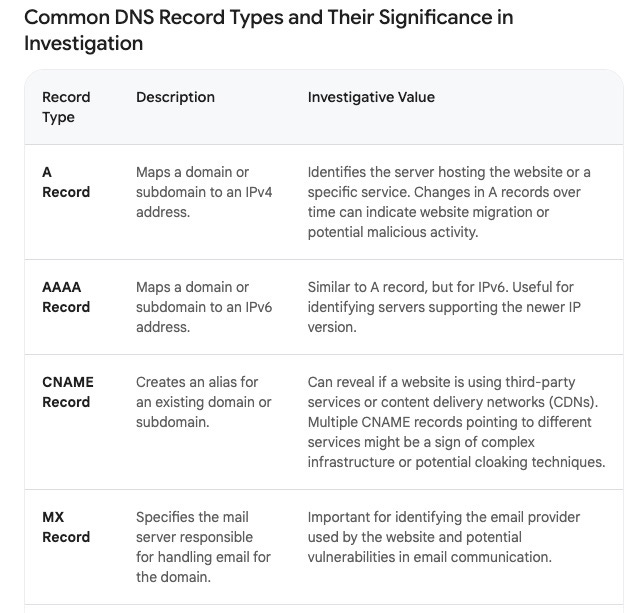
Here is a key that explains the different DNS Record Types you might see in the data:
There are literally dozens of services to look up WHOIS information, but two that I like are the MXtoolbox https://mxtoolbox.com/whois.aspx and Domain Dossier by Central Ops https://centralops.net/co/
The News…
I recently considered purchasing a vehicle through Carvana. A research organization claims the car company is an “accounting grift for the ages,” and suggests its house of cards will soon collapse. They put together a compelling case. https://hindenburgresearch.com/carvana/
A teller has been caught stealing 81K dollars from dormant bank accounts in a case close to home for my DABS subscribers. I’ve seen cases like this before where an insider abuses inactive accounts. “In the course of his theft, Chatt specifically targeted dormant accounts, meaning accounts with no activity for an extended period of time. Between December 2023 and November 2024, Chatt created emergency debit cards on-site that he used to withdraw from the accounts he accessed.” Organizations should monitor accounts for sudden activity after being dormant for a set time. The security team must review any account touched after being inactive for (X months). https://finance.yahoo.com/news/former-delaware-bank-teller-accused-115500858.html
Hackers who attacked Rhode Island's RIBridges system, which manages various state benefits programs, have released stolen files to the dark web after their ransom demands were unmet. While the exact scope of the released data is still being determined, officials assume that all data within the RIBridges system has been compromised. The RIBridges system serves over 300,000 Rhode Islanders annually and manages benefits programs that account for over 40% of the state's budget. https://statescoop.com/rhode-island-benefits-system-cyberattack-files-dark-web/
There is no honor amongst thieves. Crypto scammers target other scammers by using a multi-signature wallet to trick them into sending their stablecoins to a wallet controlled by the scammers. The scammers are impersonating beginners who share access to their crypto wallets, tricking equally naive thieves who become the victims. https://www.coindesk.com/markets/2024/12/30/crypto-scammers-are-now-stealing-from-other-crypto-thieves
Dan Goodin argues that passkeys, an alternative to passwords, have failed to live up to their promise of "usable security" due to their complex and varying implementations across different browsers, operating systems, and password managers. Goodin claims the FIDO2 specification and WebAuthn predecessor underpinning passkeys are elegant but have been undone by the diverse ecosystem, resulting in competing workflows and capabilities that often force users to choose the vendor's preferred passkey option. Passkeys are challenging to sync across different platforms, with many software engineers criticizing the approach. Furthermore, passkey implementations can lock users into specific platforms, preventing seamless syncing across devices and making it more complicated than it should be for users to manage their passkeys. https://arstechnica.com/security/2024/12/passkey-technology-is-elegant-but-its-most-definitely-not-usable-security/
The Federal Trade Commission (FTC) has filed a lawsuit against online cash advance firm Dave Inc., alleging that the company uses deceptive marketing practices to charge consumers undisclosed fees and "tips" without their consent. https://www.ftc.gov/news-events/news/press-releases/2024/12/ftc-refers-case-against-online-cash-advance-firm-dave-inc-department-justice
Minnesota has created a new state agency to tackle fraud and financial crime. https://www.msn.com/en-us/politics/government/minnesota-governor-tim-walz-signs-executive-order-establishing-state-agency-to-detect-fraud-and-financial-crimes/ar-AA1wV4Dg
The CFP (Call for Presentations) is open for the 2025 Layer 8 Conference. The conference is a one-day event focused on social engineering and OSINT. Boston is nice in June. https://layer8conference.com/layer-8-conference-2025/
Cool Tool
I sat down and accomplished a long-overdue task this week. Since 2021, I’ve maintained a StartMe page that catalogs various investigative and OSINT resources I use. It had been a while since I cleaned it up, but I removed all the dead links and added some new resources. Pin the URL to your favorites bar for quick access during your investigations. https://start.me/p/jjo29z/matt-s-osint-page
Cool Job
Lead Financial Crime Investigator - AML, KeyBank. https://keybank.wd5.myworkdayjobs.com/External_Career_Site/job/Remote-United-States/Lead-Financial-Crimes-Investigator---Anti-Money-Laundering_R-29795
DFIR
A nifty trick to (maybe) bypass Bitlocker encryption on Windows 11 devices. https://noinitrd.github.io/Memory-Dump-UEFI/
Lionel Notari shares some insights learned while examining logs from Apple’s watchOS. https://www.ios-unifiedlogs.com/post/watchos-unified-logs-introduction-and-calls
Irrelevant
Those who have spent time employed by a law enforcement agency know all too well about the Peter Principle. There is some truth to the idea that workers are promoted to their level of incompetence. However, in law enforcement agencies, the unfortunate reality is that incompetent employees are never removed. As a result, they linger on, undermining the efficiency and morale of the agency until they retire. https://www.cbc.ca/news/canada/british-columbia/peter-principle-vancouver-history-1.7415994
Irrelevant
Sign Off
The Recruiting Heroes LLC blog published “Ten things I wished I knew before leaving law enforcement” about the transition from government to corporate. Yep, it’s pretty much spot on, and I suggest that anyone from LE who’s considering the transition read it. Also, don’t be shy about reaching out to someone who has transitioned for advice. https://recruitingheroesllc.com/blog/f/ten-things-i-wish-i-did-before-leaving-law-enforcement
As always, thank you for giving the newsletter a few minutes of your time, and I hope you found enough value to return next week.
Matt
“YOU CAN NEVER BE OVERDRESSED OR OVEREDUCATED.” -OSCAR WILDE
Published every Tuesday, Threats Without Borders offers original commentary and educational pieces related to cybercrime investigations and information security topics. We also summarize and comment on news articles concerning active threat intelligence for the financial industry. The newsletter interests everyone tasked with cybersecurity or involved in preventing or investigating technology-enabled fraud, theft, or money laundering.
Legal: I am not compensated by any entity for writing this newsletter. Obviously, anything written in this space is my own nonsensical opinions and doesn’t represent the official viewpoint of my employer or any associated organization. Blame me, not them.
cybercrime cybersecurity investigations cyficrime aml financial crime osint