Threats Without Borders - Issue 218
Cybercrime Investigation Newsletter, week ending January 19, 2025
The introduction of the EMV chip solved the counterfeit credit card crisis, right? Re-encoding the magnetic stripes of blank cards was no longer an option since the payment terminals required validation from the chip. And the bad guys can’t recreate the chip, right?
Once again, they run around the end. Chip card? That is no problem; they just bypass the requirement for a chip.
There have been many ways that criminals have forced payment terminals to revert to the magnetic stripe for authorization validation. The most infamous method was the “push/pull” technique, where you insert the card into the chip reader and quickly pull it out before the EMV chip and terminal can sync. Do this three times quickly, and it will trick the terminal into believing the chip is faulty, leading it to default back to the magstripe.
Many others have had some degree of success, but they all involve some degree of suspicious activity that may draw the attention of an interested retail clerk.
But what if we could tell the terminal to authenticate using the magnetic stripe from the beginning? Just swipe the card, finish the transaction, and walk away as usual—just like in the good ol’ days days!
I recently attended a webinar on card fraud trends hosted by the Delaware Valley Chapter of the IAFCI. The presenter was Jay Dubina, Senior Manager and Fraud System Administrator for a large International payment processor. One of the trends discussed in the excellent presentations was Service Code Manipulation.
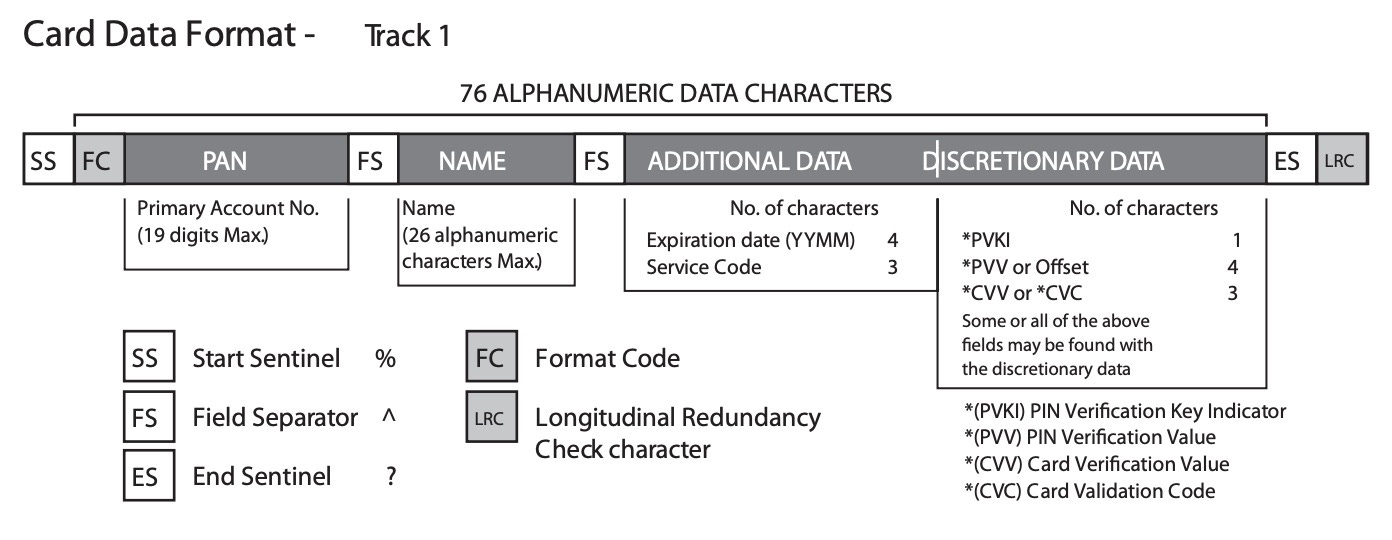
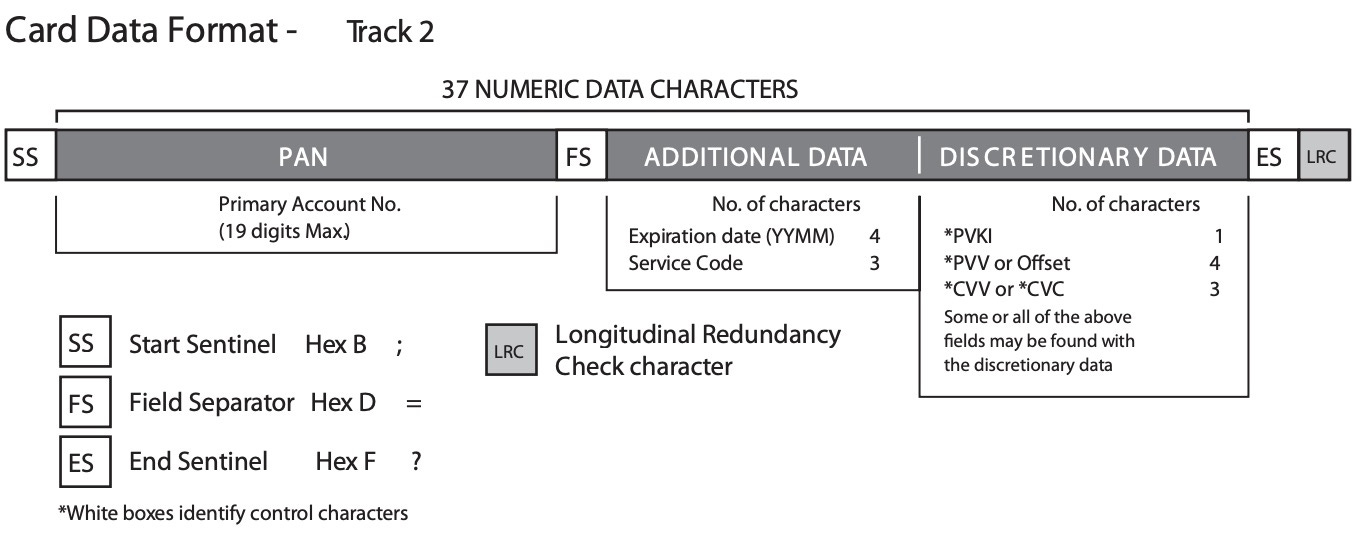
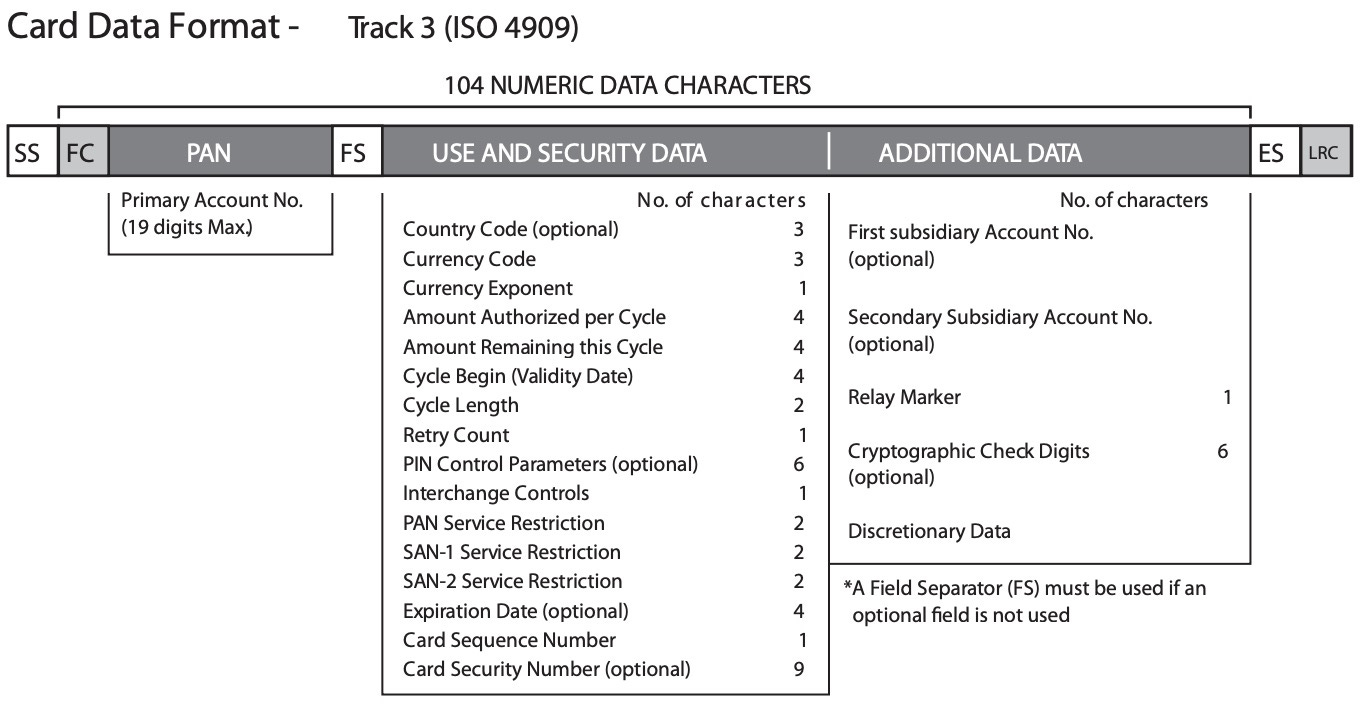
The magnetic strip on a credit card contains encoded information and instructions required by the payment terminal to process the transaction. This information is divided into three tracks and includes data such as the cardholder's name, card numbers, expiration date, and any discretionary data that the card issuer may include
More information on track data here - https://www.magtek.com/content/documentationfiles/d99800004.pdf
Included in this information, in Track 2, is the Service Code. This three-digit code tells the merchant’s payment terminal how the card should be presented and how it can be accepted. Essentially, it can be accepted as an EMV chip card or as a magnetic swipe card.
Purchasing stolen credit card accounts online or via Telegram is simple. Re-encoding the track data onto a blank card or gift card is straightforward. Convincing the merchant terminal to accept a swipe instead of an EMV chip is the main obstacle to overcome.
Service Code Manipulation is the answer.
Savvy criminals modify the service code in the track data to make the card seem like a magstripe card instead of a chip card. Thus, the 201 service code changes to a 121 code.
More information on Service Codes at https://pcijourney.com/what-is-a-payment-card-service-code/
Now, the terminal at your local self-checkout register happily accepts that card swipe.
Other than a computer and an MSR reader/writer, no extra tools are required to commit this fraud; just a bit of knowledge on how to read the track data and then make alterations in a text editor before encoding the blank magstripe.
Is this simple technique consistently successful? No, but it works sufficiently well to be on the radar of the major card processors.
At least until all issued cards are contactless.
Fraud techniques are like lousy fashion trends, they always come back around.
The News…
A good rule of thumb is to take the damage estimate given by the breached company and multiply it by three, or even ten. PowerSchool has disclosed that its recent data breach is far worse than initially thought. This incident affected the education technology company, leading to the unauthorized access and theft of all student and teacher data from various institutions, including historical records. The breach involved compromised credentials, unauthorized access to the PowerSchool Student Information System (SIS), and the extraction of sensitive information such as names, addresses, Social Security numbers, and medical records. https://www.techradar.com/pro/security/powerschool-breach-worse-than-thought-company-says-all-student-and-teacher-data-accessed
The SEC has charged Robinhood with violating several provisions of securities laws, which has led to a total penalty of $45 million. The firm did not meet various regulatory obligations, such as timely filing suspicious activity reports, safeguarding customers against identity theft, and ensuring secure systems. Additionally, Robinhood failed to properly uphold electronic communications and brokerage data as required by federal securities laws. Specifically, Robinhood Securities breached Reg SHO regulations concerning stock lending and fractional share trading. https://www.sec.gov/newsroom/press-releases/2025-5
Generally, I side with the bank in disputes, but this one goofed up. A Mississippi attorney is upset that BankPlus cashed altered stolen checks despite his warnings that they were fraudulent. “We were on the phone with BankPlus the lady that works there the teller, and we said the checks are no good. Don’t honor it,” said Reeves. “And the lady said that the forger was there in her car, and I said, ‘Why don’t you call the police? She’s there in front of you,' and they didn’t do it. They let her go and gave her the money.” He is calling for banks to be more vigilant and prosecute those involved in such crimes. Of course. https://www.wlbt.com/2025/01/15/bank-cashes-altered-stolen-checks-despite-objections-account-holder/
Windows 10 reaches its end-of-life on October 14, 2025. You can still use it after that date, but not securely, as Microsoft will no longer provide support, and apps, including Microsoft 365, will no longer receive updates. Honestly, why haven’t you already updated to Windows 11? I know, enterprise. Just get it done. https://support.microsoft.com/en-us/office/what-windows-end-of-support-means-for-office-and-microsoft-365-34e28be4-1e4f-4928-b210-3f45d8215595
The FBI issued a Public Service Announcement to warn the public that scammers exploit mass casualty events and disasters, such as the New Year's Day terrorist attack in New Orleans and the ongoing wildfires in Los Angeles, to commit fraud by soliciting fake charitable donations to support victims or their families. https://www.ic3.gov/PSA/2025/PSA250116
A new study indicates that AI-powered spear phishing is becoming increasingly effective, with AI models now capable of creating personalized phishing emails that deceive more than 50% of targets. This presents a significant cybersecurity threat, as AI-assisted phishing campaigns are more efficient and cost-effective than traditional methods. Even more concerning is that the study found the protections integrated into the AI models to prevent their use by cybercriminals do not work. “Current safety guardrails fail to reliably prevent models from conducting reconnaissance or generating phishing emails”. https://arxiv.org/pdf/2412.00586
Is Broken Windows Theory still relevant or has it been debunked? Gladwell says it’s proven to be counterproductive. John McMillan says its effectiveness speaks for itself. https://www.city-journal.org/article/broken-windows-policing-crime-malcolm-gladwell
Cool Job
Director, Anti-Money Laundering - Walgreens, https://jobs.walgreens.com/en/job/-/-/1242/74921449008
Cool Tool
Is that crypto-wallet linked to fraud? Also - report crypto-wallets linked to fraud. https://verifiwallet.com/
Criminals will use the same profile image across multiple fake accounts. This tool researches profile pictures. https://profileimageintel.com/
Heroes
These pilots of f’n heroes. https://www.latimes.com/california/story/2024-09-03/hot-dirty-dangerous-aerial-firefighting-a-labor-of-love
Irrelevant
A recent study found that 1 in 5 online job postings, or between 18% and 22% of advertised jobs, are fake or never filled. This phenomenon, known as "ghost jobs," has been growing and leads to frustration for job seekers. Companies post these jobs to make themselves appear as if they are growing or to gather applicants' information, which can then be used for data harvesting. How about someone create a job website that validates the ads as an actual open position? https://gizmodo.com/1-in-5-online-job-postings-are-either-fake-or-never-filled-study-finds-2000549706
Sign Off
I want to complain about the cold in Pennsylvania, but it’s cold everywhere, even in some places where it shouldn’t be. Enjoy the snow, Dallas.
Thanks for reading another issue of the newsletter.
Matt
Published every Tuesday, Threats Without Borders offers original commentary and educational pieces related to cybercrime investigations and information security topics. We also summarize and comment on news articles concerning active threat intelligence for the financial industry. The newsletter interests everyone tasked with cybersecurity or involved in preventing or investigating technology-enabled fraud, theft, or money laundering.
Legal: I am not compensated by any entity for writing this newsletter. Obviously, anything written in this space is my own nonsensical opinions and doesn’t represent the official viewpoint of my employer or any associated organization. Blame me, not them.