Threats Without Borders - Issue 222
Cybercrime Investigation Newsletter, week ending February 16, 2025
We’re still in the thick of prediction season, and the experts are laying out their forecasts for the future trends in cybersecurity and cybercrime
Most of them, if not all, incorporate a significant element of Artificial Intelligence (AI), whether it be Generative AI or Machine Learning. In fact, the inclusion is so widespread that you might think SkyNet is alive. Just kidding, it is
Regardless, I can’t help but believe that the emphasis on AI is merely a new content landscape for many of these writers. It fulfills the need to be trendy and cutting-edge, pushing the boundaries to create the impression that they are ahead of the curve and preeminent.
AI is real, and the bad guys are incorporating certain features into their attacks. However, it’s not (yet) what most of us encounter in our daily cybersecurity and fraud-fighting activities.
Because the old ways still work just fine.
Examining the “Top Routinely Exploited Vulnerabilities” list published by CISA, you’ll find CVE-2021-44228 Apache Log4Shell and CVE-2020-1472 Microsoft Netlogon. You’ll also find CVE-2021-27860 FatPipe Warp and CVE-2019-0708 Microsoft Remote Desktop Services.
The Common Vulnerability and Exposure number (CVE) is a unique identifier that catalogs publicly known software vulnerabilities. Within the CVE number, you’ll find the year the notice was released. What do you notice in the CVEs that I noted above? 2020, 2021, 2019. This list was published by CISA in 2024, and now it’s 2025.
How about CVE-2018-13379 FortinetOS SSL VPN? Yeah, 2018!
These exploitable flaws were patched four, five, six years ago, yet they are still being regularly abused because users (and organizations) are simply not good at security. To quote one of my favorite sayings, “they just don’t know, don’t show, or just don’t care about what happens in the hood." Thank you, Doughboy,
This reflects what is occurring in CyFi crime. Sure, AI is being utilized, but for the most part, it’s the same old, same old. Why invest the time, effort, and money in new technologies when the tools you already have work so well?
Paper check fraud abusing digital banking is booming. Social engineering attacks through the telephone are as easy as ever. And getting someone to click a link or open an attachment in an email is like stealing from a baby.
But Matt, they’re using AI to write the phishing emails and AI voice cloning to make the phone calls. I don’t know about that. I review dozens of phishing emails per week sent into my organization and they look like the same emails we were receiving pre-AI. And playing around with AI voice cloning is fun, but calling the account payable clerk or Grandma from a spoofed VOIP line and adding in some stress still works fine.
I think the most significant threat might be the abuse of AI tools that replace human workers.
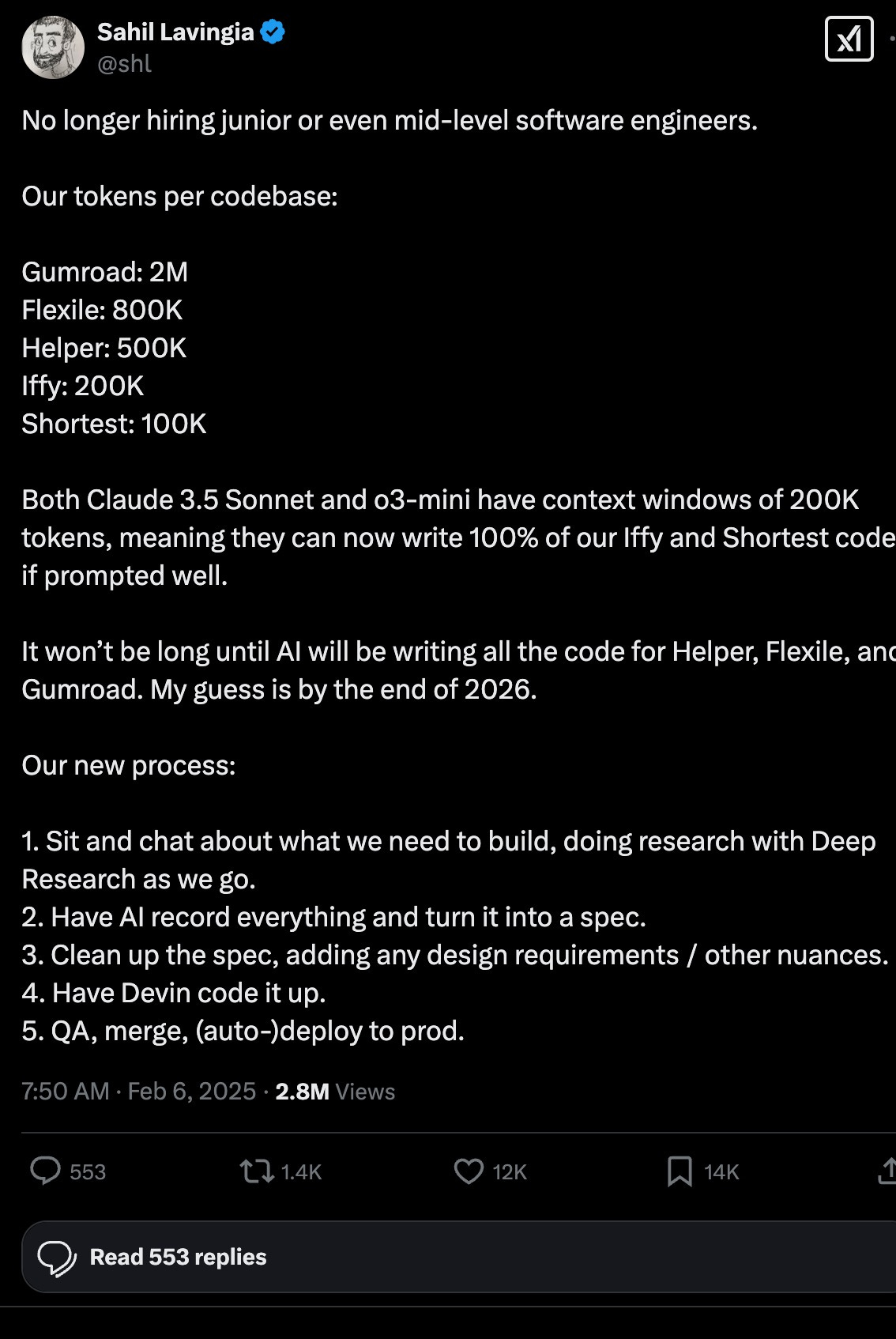
And I am fully aware of the power of AI. Here is Sahil Lavingia, the CEO of Gumroad, explaining that he’s no longer hiring entry level and junior software engineers because AI does it better.
(Side note: If your child is paying thousands of dollars to a college to learn software development or coding - have them transfer to a trade school ASAP)
I encourage you to examine your organization’s current risk landscape to pinpoint where you incur the most significant losses. I would wager that AI plays no role and probably never will.
Welcome New Subscribers
The newsletter was recently mentioned in a thread on Reddit. Thank you, u/dark-mark, for the shout-out. For first-time readers, the Reddit thread described the newsletter's content as “cybersecurity threat intelligence." If you’re here for strict threat intelligence, you might be disappointed. The newsletter focuses more on cyber and financial crime, or as I call it, CyFi Crime. However, there is some threat intelligence. And snark. And sometimes, just outright nonsense.
But it’s all at no cost to you and completely free of advertisements. Of course, sometimes you get what you pay for.
Welcome aboard, I couldn’t be happier that you’re giving us a try.
The News
Google's Threat Intelligence Team released a report, “Cybercrime: A Multifaceted National Security Threat," highlighting the significant risk cybercrime poses to national security, with financially motivated attacks surpassing state-sponsored hacking in 2024. These attacks severely disrupt critical infrastructure, healthcare, and the economy. The report emphasizes the necessity of international cooperation among law enforcement and intelligence agencies to combat cybercrime effectively and suggests implementing education and resilience strategies as systemic solutions. https://services.google.com/fh/files/misc/cybercrime-multifaceted-national-security-threat.pdf
Huntress goes deep on cyber-insurance. https://www.huntress.com/blog/cyber-insurance-trends
The Pennsylvania Turnpike Commission is warning drivers about new versions of the smishing scam, which involves fraudulent text messages demanding payment for unpaid tolls. This is nothing new and not limited to the toll roads in just Pennsylvania. But why do the bad guys keep going back to it…because it works. https://www.pennlive.com/news/2025/02/pa-turnpike-warns-drivers-of-new-forms-of-smishing-scam.html
Kasada claims to have infiltrated twenty-two credential stuffing groups. Credential stuffing has matured into a sophisticated industry, presenting significant challenges to traditional security measures. This article examines the advanced tactics used by credential stuffing groups and underscores the necessity for a proactive approach to countering account takeover attacks. https://www.kasada.io/lessons-learned-infiltrating-credential-stuffing-crews/
Financially motivated hackers increasingly work alongside nation-state hackers, who use cybercrime groups to hide their espionage activities. This cooperation has become more evident in recent years, with researchers observing a rise in the sharing of malware between cybercrime groups and governments, including Russia, China, and Iran. https://arstechnica.com/security/2025/02/financially-motivated-hackers-are-helping-their-espionage-counterparts-and-vice-versa/
Bushido Token examines BitLaunch, a UK-based hosting provider, and its involvement in enabling cybercriminal activities, especially ransomware attacks. It is claimed that BitLaunch's "anonymous Bitcoin VPS" service is exploited by cybercriminals to host command-and-control (C2) servers, which they use to carry out ransomware attacks. https://blog.bushidotoken.net/2025/02/investigating-anonymous-vps-services.html
The Dutch police have dismantled the ZServers/XHost bulletproof hosting operation, seizing 127 servers used by the platform. The seized servers, located in Amsterdam, hosted hacking tools from Lockbit and Conti ransomware and were used to launder money and distribute malware. While no arrests were made, the administrators faced sanctions through asset freezes and travel bans. For what that’s worth. https://www.bleepingcomputer.com/news/legal/dutch-police-seizes-127-xhost-servers-dismantles-bulletproof-hoster/
A Las Vegas business owner has been indicted for defrauding investors by misrepresenting his company, Profit Connect, as a profitable cryptocurrency mining and verification business. The man is accused of using investor funds for personal expenses and to make fraudulent repayments, resulting in an estimated $24 million loss for over 400 investors. https://www.justice.gov/usao-nv/pr/owner-las-vegas-company-indicted-24-million-cryptocurrency-ponzi-scheme
DFIR
The increasing necessity of mobile forensics in solving crimes. https://www.police1.com/police-products/investigation/investigative-software/the-increasing-necessity-of-mobile-forensics-in-solving-crimes
Cool Job
Head of Corporate Security - New York Life. https://careers.newyorklife.com/careers/job/26986731
Cool Tool
Reverse image search tool - https://copyseeker.net/
Hack your Kindle. https://kindlemodding.org/jailbreaking/WinterBreak/
Reader Mail
I see what you did with the baseball diagram. Funny. - Jen
I can only assume she picked up on the standing out in left field reference (Issue 221). Thanks for noticing, Jen. I believed it was clever of me.
Irrelevant
Kevin Kelly provides tips for better travel that he’s collected over the past 25 years. https://kk.org/thetechnium/50-years-of-travel-tips/
Sign Off
The Ringelmann Effect best describes the inefficiency of our government: Members of a group become lazier as the size of their group increases based on the assumption that “someone else is probably taking care of that.”
Thank you for reading another issue. I never take for granted that someone clicks on the newsletter and spends a few minutes engaging with my writing. There is an immense demand for your attention, and I appreciate that I have earned some of it.
Matt
Published every Tuesday, Threats Without Borders offers original commentary and educational pieces related to cybercrime investigations and information security topics. We also summarize and comment on news articles concerning active threat intelligence for the financial industry. The newsletter interests everyone tasked with cybersecurity or involved in preventing or investigating technology-enabled fraud, theft, or money laundering.
Legal: I am not compensated by any entity for writing this newsletter. Obviously, anything written in this space is my own nonsensical opinions and doesn’t represent the official viewpoint of my employer or any associated organization. Blame me, not them.