Threats Without Borders - Issue 226
Cybercrime Investigation Newsletter, week ending March 16, 2025
Discussions about BIN attacks have been buzzing in forums and email lists. While I’m uncertain if all the fraud linked to BIN attacks truly falls under that category, it's clear that some incidents certainly do.
This topic has garnered so much attention and interest that Cybereason made it a focal point of this week's discussion on their blog.
https://www.cybereason.com/blog/identifying-and-preventing-bin-attacks
First, Matt, what is a BIN attack?
Attackers utilize mathematical algorithms to exploit Bank Identification Numbers (BINs), which are the first six to eight digits of a credit card number. Carders leverage mathematical algorithms, including the Luhn algorithm, to generate thousands of potential card numbers by appending random digits to the BIN. To test the validity of these generated numbers, they deploy automated bots to execute small, low-value transactions, typically ranging from $1 to $20, on vulnerable e-commerce platforms.
That’s why you see that $1 charge on a statement before the flood of high-dollar unauthorized transactions.
Ok, What’s the Luhn algorithm?
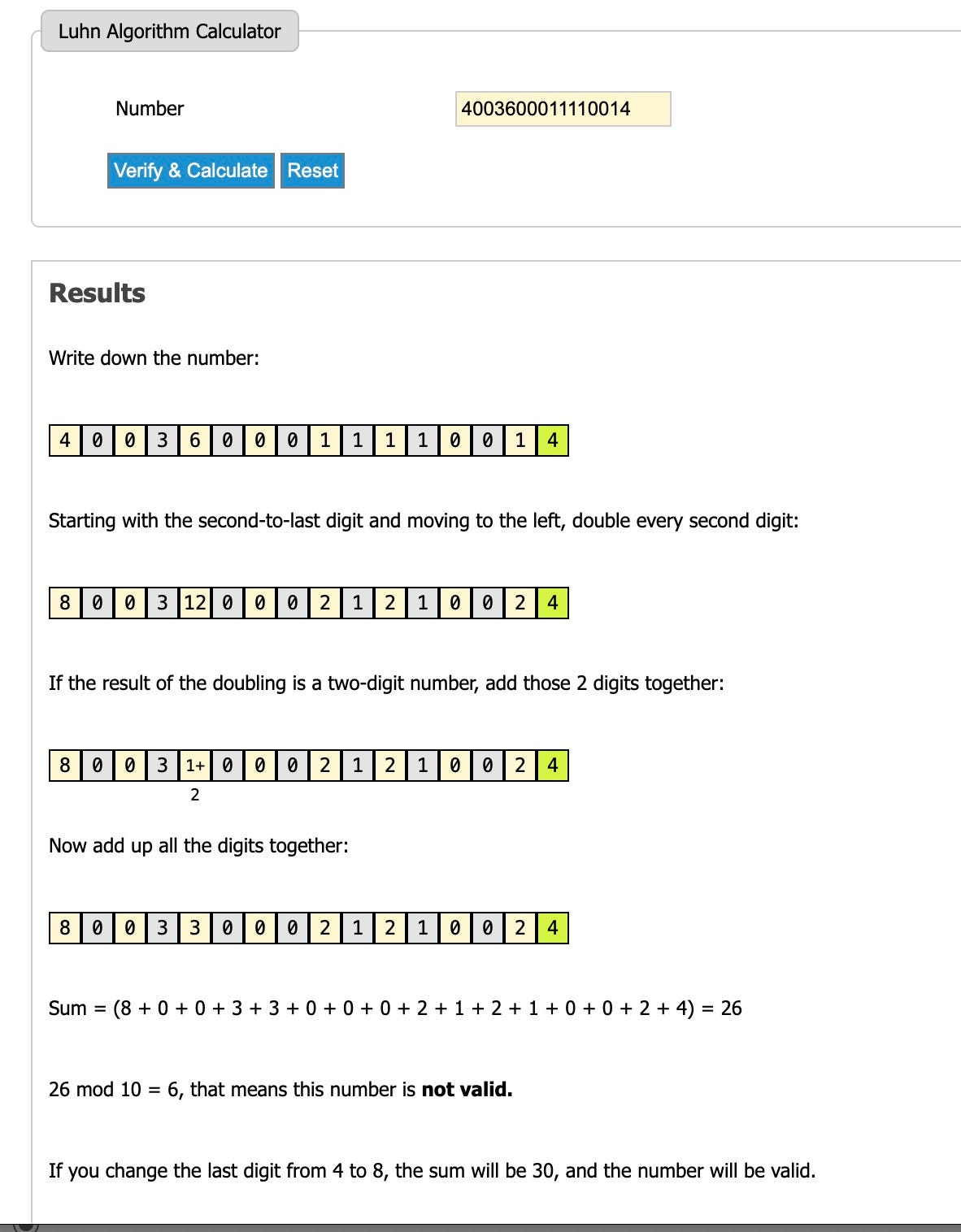
Created by IBM engineer Hans Peter Luhn in 1954, the Luhn algorithm, or modulus 10 algorithm, serves as a mathematical checksum intended to verify identification numbers like credit cards, IMEI codes, and government IDs. Its primary purpose is to detect simple errors like typos rather than to provide security. The algorithm follows a straightforward process: starting from the second-to-last digit, every other digit is doubled while moving left. The digits of these products are summed, and the undoubled digits are added to this total. If the final sum ends in zero, the number is deemed valid.
Credit card numbers are structured with three key components. The first six to eight digits comprise the Bank Identification Number (BIN), identifying the issuing bank. This is followed by the account number, a unique sequence assigned by the bank, and the check digit created by the Luhn algorithm to validate the entire number. Credit card issuers generate these numbers by assigning a BIN and an account number, then applying the Luhn formula to determine the check digit before combining these components into a Luhn-valid credit card number.
Every credit card combines three elements:
BIN (Bank Identification Number): First 6-8 digits identifying the issuer.
Account number: Unique 9-12 digit sequence assigned by the bank.
Check digit: Final digit calculated via Luhn algorithm to validate the entire number.
For example 4003 6000 1111 0014
Applying the Luhn algorithm to check the validity of a number:
Starting from the second-to-last digit, double every other digit moving left.
Sum the digits of these products (e.g., 12 becomes 1+2=3).
Add all undoubled digits to this total.
If the final sum ends in 0, the number is valid.
And NO, don’t ask me to do that without using a validator tool – there are plenty online.
While this system is effective for validation, its public availability makes it vulnerable to carder exploitation. They easily generate valid card numbers by starting with BINs, randomly generating account numbers, and computing the check digit using the Luhn formula. This method allows them to produce thousands of mathematically valid card numbers. They further test these numbers using automated bots on low-security websites, attempting small transactions to determine which cards are active. Once valid numbers are identified, criminals combine them with brute-forced expiration dates, fabricated CVV codes, and stolen personal data to create fully functional counterfeit cards.
More Skimmers
A skimmer was found on a POS terminal at a Harrisburg, PA, market. Some good-hearted citizens returned and conducted their investigation, only to find another.
CREDIT: Channel 5 Ratchet News. https://www.facebook.com/groups/2256850741115859/
The News…
Group-IB analyzes the ongoing issue of SIM swapping fraud. This enduring threat enables cybercriminals to circumvent security measures, gaining access to a victim's phone number and resulting in substantial financial loss and personal data breaches. Typically, attackers gather sensitive details via phishing sites or social engineering and then submit a SIM swap request with the cellular provider. Once they take control, they can capture SMS-based two-factor authentication (2FA) codes and perform unauthorized transactions. https://www.group-ib.com/blog/the-evolution-of-sim-swapping-fraud-how-fraudsters-bypass-security-layers/
Unit 42 researchers discovered a campaign distributing thousands of fraudulent cryptocurrency investment platforms through websites and mobile applications. The threat actors systematically create and promote these scams, impersonating well-known brands and organizations to lure victims. https://unit42.paloaltonetworks.com/fraud-crypto-platforms-campaign/
The FTC dropped its case against MGM Resorts International regarding the company’s handling of personal data stolen in a 2023 ransomware attack. The FTC initially sought information about MGM’s compliance with data protection laws but withdrew its request after the Trump administration took office. This dismissal resolves the legal controversy surrounding the attack, which crippled MGM’s digital systems and caused widespread disruptions. https://therecord.media/trump-admin-ends-ftc-ransomware-case
Citibank is hiring IT staff to reduce its reliance on external contractors. This is a double-edged sword right here! https://www.reuters.com/business/finance/citigroup-plans-slash-it-contractors-hire-staff-improve-controls-2025-03-13/
The file encryption used by the Akira ransomware variant can be broken in a few hours by a system equipped with about 16 RTX 4090 GPUs. That’s around $65,000 in computing power. For some, paying the ransom might be a less expensive option. I kid, I kid. https://www.tomshardware.com/tech-industry/cyber-security/akira-ransomware-cracked-with-rtx-4090-new-exploit-to-brute-force-encryption-attack
Check fraud is soaring in Florida, much of it being facilitated through the postal service. Frank Albergo receives considerable space in this article to criticize USPS leadership for limiting the functionality of the postal service police . https://www.wctv.tv/2025/03/12/its-dangerous-situation-rates-check-fraud-soar-florida-leaders-search-solutions/
A deep dive into analyzing electronic signatures on PDF documents. https://hackerfactor.com/blog/index.php?/archives/1061-Sign-Here.html
Amazon is eliminating a feature that allows Echo users to process Alexa requests locally, preventing voice recordings from being sent to Amazon's cloud. Starting on March 28, all Echo users will have to send their voice recordings to Amazon's cloud, which will be processed and potentially used for Amazon's new Alexa+ subscription service. https://arstechnica.com/gadgets/2025/03/everything-you-say-to-your-echo-will-be-sent-to-amazon-starting-on-march-28/
DFIR
SalvationData predicts some DFIR trends that will occur in 2025. https://www.salvationdata.com/knowledge/key-trends-in-digital-forensics-for-2025/
Investigating attacks facilitated through AnyDesk. https://www.thedfirspot.com/post/anydesk-investigating-threat-actors-favorite-tool
Skills
I’m often by young job seekers, “What can I do that will give me a leg up on other job candidates?” One of my suggestions is running a home lab. How do you get experience securing a network if you don’t have a job securing a network? Run your own. The No Logs, No Breach blog published a good home lab primer. https://nologs-nobreach.com/2025/03/10/infosec-homelab-2025-edition/
Cool Tool
Autopsy 4.22 has been released. https://www.autopsy.com/autopsy-4-22-0-bitlocker-support-cyber-triage-sidecar-library-updates/
Unfurl parses out every aspect of a web URL and displays it in a visual graph so you know what is going to happen when you click the link: https://dfir.blog/unfurl/
Cool Job
Fraud Strategy - Senior Manager, Hard Rock Digital. https://www.hardrockdigital.com/#job-2032823
Irrelevant
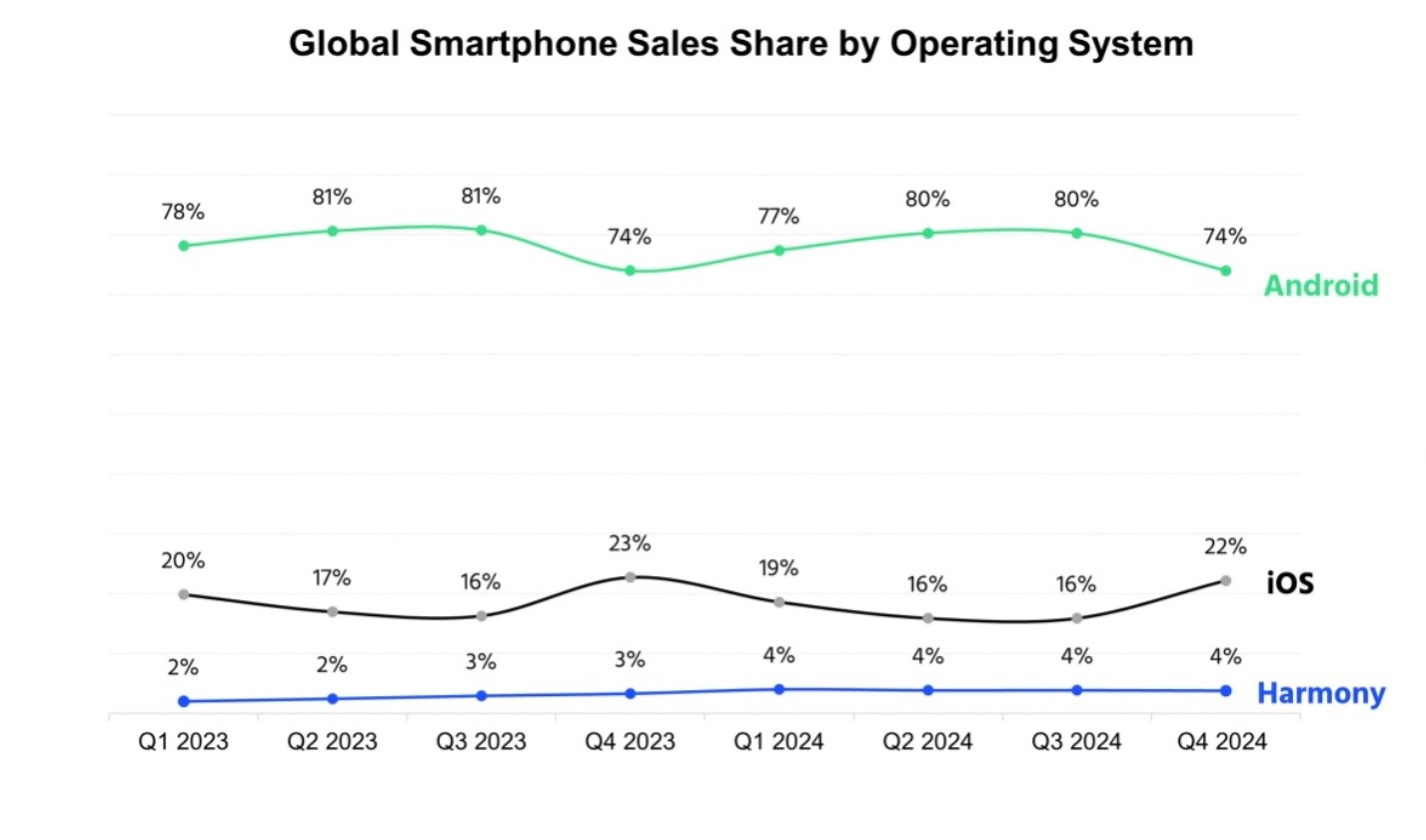
Everyone you know may have an Apple iPhone, but Android rules the world. This new report by Counterpoint Research reveals that Android dominates smartphone OS usage, followed by iOS and HarmonyOS. Harmony OS?
Sign Off
The final speaking lineup for the BSides Harrisburg conference has been released, and it looks to be another fantastic show. The venue has changed along with the ticket price, but you get lunch included this year. Check it out, and come on out; it’s one of the best cybersecurity conferences you’ll find for less than 50 bucks.
Oh, and your humble editor will be the MC of the Track A room, so make sure to come up and say Hi!
See you next Tuesday!
Matt
Published every Tuesday, Threats Without Borders offers original commentary and educational pieces related to cybercrime investigations and information security topics. We also summarize and comment on news articles concerning active threat intelligence for the financial industry. The newsletter interests everyone tasked with cybersecurity or involved in preventing or investigating technology-enabled fraud, theft, or money laundering.
Legal: I am not compensated by any entity for writing this newsletter. Obviously, anything written in this space is my own nonsensical opinions and doesn’t represent the official viewpoint of my employer or any associated organization. Blame me, not them.