Threats Without Borders - Issue 227
Cybercrime Investigation Newsletter, week ending March 23, 2025
Over the past week, I’ve spent much time explaining how attackers acquire the personal information to target a specific person in a social engineering attack. The questions usually center around how they knew a social security number or called a personal cell phone number.
People believe these are deeply guarded secrets, but the information is actually relatively easy to find. In fact, at this point, you must accept that your personal information is available somewhere on the internet.
Do you use AT&T? In 2024, the company announced that it had lost the names, addresses, dates of birth, email addresses, Social Security numbers, and, of course, cell phone numbers of over 51,226,382 customers.
How about the National Public Data breach? In 2024, the data aggregation service announced that an unknown entity had gained access to their systems and stolen the personal data of over 170 million people in the United States and Canada. This data included names, addresses, email addresses, social security numbers, and, once again, cell phone numbers numbers.
Ever heard of MOAB?
In January 2024, cybersecurity researchers uncovered what soon became known as the "Mother of All Breaches" (MOAB). This unprecedented collection contained roughly 26 billion records spread across 12 terabytes of data, making it the largest known compilation of breached information ever discovered.
The MOAB wasn't a traditional breach where hackers targeted a single organization. The database was a carefully assembled collection of data from many previous breaches. Security researcher Bob Dyachenko of Security Discovery uncovered this massive treasure chest on an unsecured ElasticSearch instance.
This digital repository housed user credentials from nearly every major platform, such as LinkedIn, Twitter/X, Adobe, Dropbox, Telegram, and many others. What particularly raised concerns about MOAB was its size and thoroughness. The database contained usernames, email addresses, passwords, and, in some instances, additional personal information like MMN (mother’s maiden name).
While Leak-Lookup took responsibility for owning the hacked server hosting the dataset, it isn’t known who collected the massive dataset.
Or what about Loan Depot, Evolve Bank and Trust, or Infosys? They all suffered data breaches in 2024 and lost their customers' personal data.
Or even Advanced Auto Parts? Yes, the bad guys probably know what car you drive to.
Another question I’m often asked is, “Should I subscribe to an identity theft monitoring service to watch the dark web for my data?”
I’ll save you the suspense. It’s there.
Whether you should pay a company to tell you that depends on whether they can adequately answer this question: “I assume my personal information is already for sale on some criminal marketplace. What are you going to do to remove it?”
According to the Federal Trade Commission (FTC), consumers reported losing more than $12.5 billion to fraud in 2024, a 25% increase from the previous year. This surge is not due to an increase in fraud reports but rather a higher percentage of people reporting losses, with 38% of those who reported a fraud saying they lost money in 2024, up from 27% in 2023.
Unsurprisingly, email was the most common method by which consumers reported being contacted by scammers, followed by phone calls in second place and text messages in third.
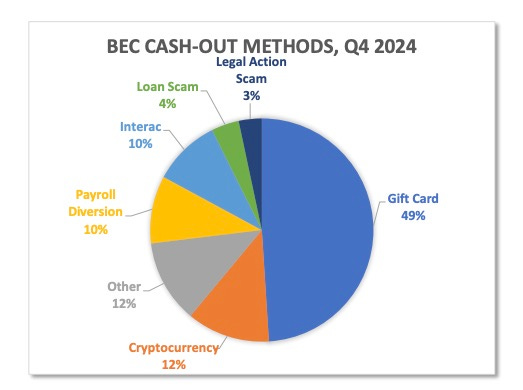
The Anti-Phishing Work Group (APWG) released the Phishing Trends Report for 4Q 2024, and as expected, phishing is a booming business. Much to the chagrin of crypto-crime "experts," I often refer to gift cards as “the currency of cybercrime." This report appears to support that claim, as nearly half (49%) of all Business Email Compromise cash-outs in the fourth quarter occurred through gift cards.
Read the full report: https://docs.apwg.org/reports/apwg_trends_report_q4_2024.pdf
The News…
Speaking of organizations losing your personal information through a data breach…are you a teacher in Pennsylvania? The Pennsylvania State Education Association (PSEA) announced a security incident affecting 517,487 persons. The organization acknowledged the following information was obtained: “Date of Birth, Driver’s License or State ID, Social Security Number, Account Number, Account PIN, Security Code, Password and Routing Number, Payment Card Number, Payment Card PIN and Payment Card Expiration Date, Passport Number, Taxpayer ID Number, Username and Password, Health Insurance Information and Medical Information”. Ah… yeah, just about everything about you! https://www.psea.org/pages-without-a-home/notice-of-data-security-incident/
And the data breach notification report PSEA filed with the Maine Attorney General. https://www.maine.gov/agviewer/content/ag/985235c7-cb95-4be2-8792-a1252b4f8318/e44266ce-8099-4d3c-8635-2c5cdb41f24a.html
Reddit users are being targeted by a group pushing info-stealer malware. https://www.malwarebytes.com/blog/scams/2025/03/amos-and-lumma-stealers-actively-spread-to-reddit-users
Spycloud published its 2025 Identity Exposure Report. I’ll revisit this once I have more time to digest it - it’s a really thorough and well-written report. Great graphics, too. https://engage.spycloud.com/rs/713-WIP-737/images/spycloud-2025-identity-exposure-report.pdf
I hold two SANS/GIAC certifications, and I’ve let another expire, so I’m not a hater. However, the organization is becoming increasingly difficult to defend. In fact, after their most recent price increase, I’ve stopped trying. This write-up offers a fantastically detailed account of how the author lost money trying to apply for a SANS scholarship. Yet, another really bad look for the organization. https://infosecwriteups.com/how-i-wasted-537-on-the-sans-paller-scholarship-without-even-being-considered-as-a-valid-6b5d4a9ef552
Michigan State University starts a cybercrime training program for law enforcement. https://msutoday.msu.edu/news/2025/msu-center-trains-law-enforcement-on-cybercrime-threats-first-of-its-kind-in-the-country
Bloomberg explains what led to TD Bank being hit with $3.1 billion in fines from U.S. auditors for becoming “the most convenient” bank for money laundering. https://www.bloomberg.com/news/features/2025-03-18/the-criminal-money-laundering-scams-that-cost-td-bank-billions
Basics
The Cyber Kill Chain is a concept developed by Lockheed Martin that helps in understanding how cyberattacks occur. It breaks down a cyberattack into a series of steps, making it easier for security professionals to identify and address threats. The main steps include: 1) Reconnaissance 2) Weaponization 3) Delivery 4) Exploitation 5) Installation 6) Command and Control (C2) and 7) Actions on Objectives. Some experts also mention an additional step, Monetization, which involves the attacker attempting to profit from the attack. By understanding the Cyber Kill Chain, organizations can better prepare for and respond to cyberattacks by applying specific security measures at each stage. Security teams use this model to detect and thwart various cyber threats, safeguarding sensitive information and valuable assets. Understanding how each stage of an attack functions helps defenders enhance their security, disrupt the attackers, and reduce the likelihood and costs associated with security incidents.
Cool Job
Senior Manager of Insider Threats - Lionbridge. https://career4.successfactors.com/sfcareer/jobreqcareer?jobId=56487&company=lionbridgeP
Financial Crimes Manager - Fifth Third Bank. https://fifththird.wd5.myworkdayjobs.com/en-US/53careers/details/Financial-Crimes-Manager_R57393
Cool Tool
Kali 2025.1 has been released. https://www.kali.org/blog/kali-linux-2025-1-release/
Search the deep web: https://biznar.com/biznar/desktop/en/search.html
DFIR
Sara Edwards discusses how to use Apple Intelligence in your forensic investigations. https://github.com/mac4n6/Presentations/blob/master/Using%20Apple%20Intelligence%20%5BAI%5D%20Data%20in%20Investigations/UsingAppleIntelligenceDataInInvestigations.pdf
Irrelevant
Smuggling eggs…more people have been caught sneaking eggs into the country this year than fentanyl. https://www.ctvnews.ca/world/article/us-border-officials-have-caught-more-people-with-eggs-than-fentanyl-this-year/
Sign Off
This week's issue was written on a new 15-inch Apple MacBook Air with the M4 chip. While I can’t say that I notice a performance difference compared to my previous M1 Air, the jump to a 15-inch screen is a significant improvement. And yes, fingerprints show on the midnight black finish.
Thank you for reading another issue of the newsletter and we’ll see you next Tuesday.
Matt
“IF YOU DO NOT ASK QUESTIONS, YOU WILL NEVER KNOW THE ANSWERS.”
Published every Tuesday, Threats Without Borders offers original commentary and educational pieces related to cybercrime investigations and information security topics. We also summarize and comment on news articles concerning active threat intelligence for the financial industry. The newsletter interests everyone tasked with cybersecurity or involved in preventing or investigating technology-enabled fraud, theft, or money laundering.
Legal: I am not compensated by any entity for writing this newsletter. Obviously, anything written in this space is my own nonsensical opinions and doesn’t represent the official viewpoint of my employer or any associated organization. Blame me, not them.