Threats Without Borders - Issue 228
Cybercrime Investigation Newsletter, week ending March 30, 2025
Over the past few years, "Dwell Time" has become part of the American lexicon. In the context of infectious disease, the term refers to the amount of time a disinfectant must remain wet on a surface to effectively disinfect it. The faster a disinfectant solution kills pathogens and sanitizes a surface, the more effective it is. The Covid-19 pandemic turned many of us into experts in disinfectants.
The concept of dwell time is also significant in information and computer network security. Dwell time measures the duration a threat actor remains active, unnoticed, within a network. It tracks the time from a breach to its detection. Clearly, the longer an adversary exists in the environment, the more time they have to steal data and damage systems. The ultimate goal of every security team is to minimize adversary dwell time to the shortest duration possible. A dwell time of zero is ideal.
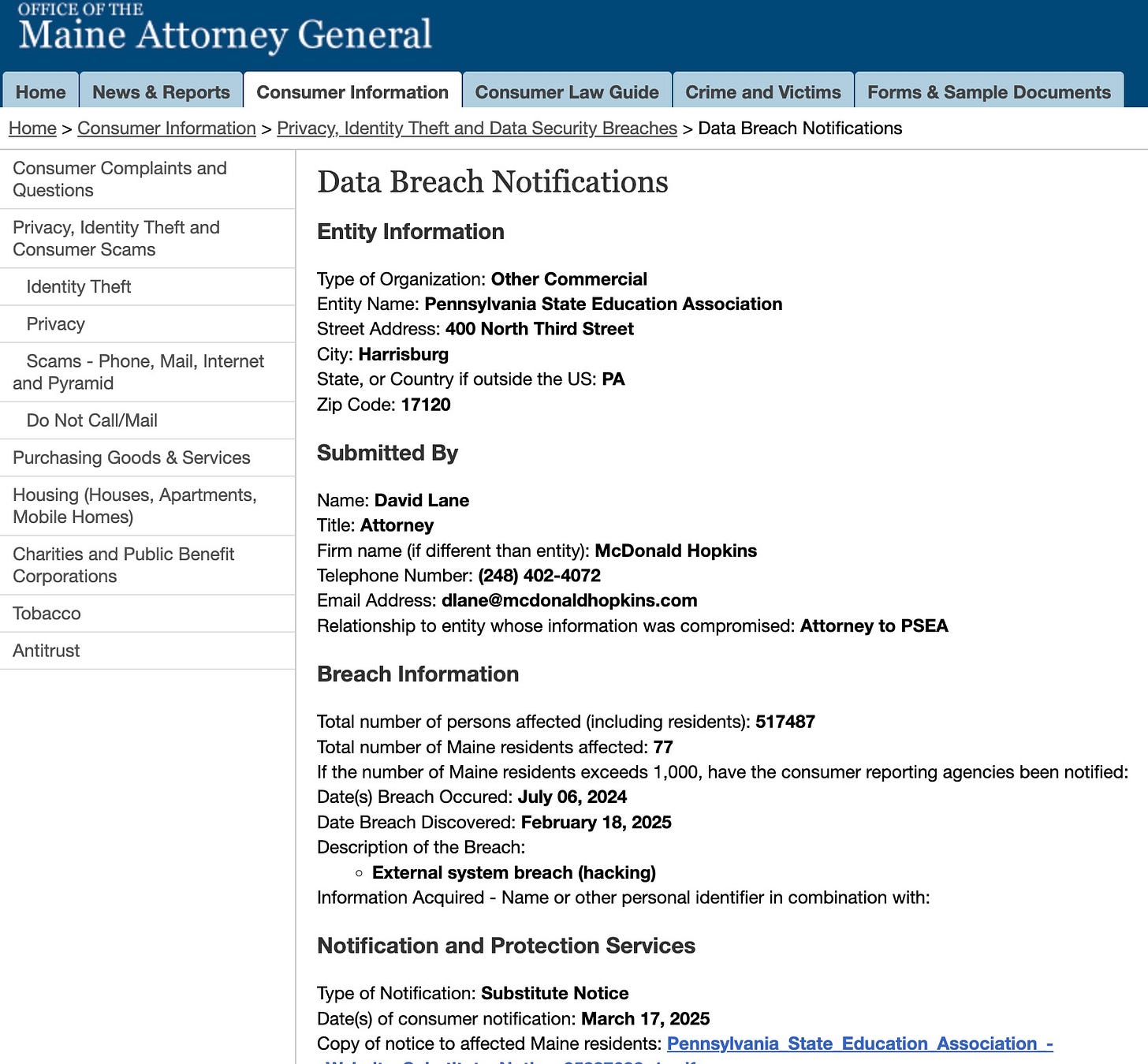
Last week, I linked to a news article about a database breach at the Pennsylvania State Education Association. PSEA is the public sector union for most education professionals in the state. They claim to represent over 187,000 education professionals actively. In acknowledging the breach, the organization admitted the breach resulted in the loss of “Date of Birth, Driver’s License or State ID, Social Security Number, Account Number, Account PIN, Security Code, Password and Routing Number, Payment Card Number, Payment Card PIN and Payment Card Expiration Date, Passport Number, Taxpayer ID Number, Username and Password, Health Insurance Information and Medical Information.” That’s pretty much everything.
I also linked to the report filed with the Attorney General of Maine. The organization was required to file the report because the breach affected residents of Maine (former PSEA members or retirees). In this report, PSEA declared the breach affected not only 77 residents of Maine, but 517,487 people in total.
A half a million people. That is huge. Figuratively and literally.
But even more concerning, the notice declares the investigation found the breach initially occurred on July 6, 2024. The organization became aware of the breach on February 18, 2025.
Holy dwell time Batman. If Siri’s math is correct, the attackers were in the network for 227 days.
In their 2024 M Trends report, Mandiant asserted that the global median dwell time has reached its lowest point in over a decade, with organizations detecting intrusions within a median of 10 days. That’s a significant increase; but are organizations improving their security? Not really.
Dwell times end in two ways: the organization either recognizes the intrusion through its own efforts and responds, or it learns about the intrusions from an external source and takes action. This external source can be the attackers themselves or an interested third party, such as a security vendor or a law enforcement agency like the FBI.
Why would the attackers let the victim organization know they are infected? Again, there are two options. First, they have exfiltrated all the data or accomplished some other goal and no longer need to remain in the network. Secondly, they must run something extremely noisy that cannot go unnoticed. Sometimes, as in the case of ransomware, this is by design.
Average dwell time has decreased because attackers are more efficient in exfiltrating data and launching their payloads, rather than organizations improving their security measures.
Yet, some attackers still play a long game and desire to live within an infected network as long as possible to continuously collect newly added data.
I have no knowledge of the PSEA attack mechanics or the incident response beyond what has been publicly disclosed. However, if it is accurate to say that the network was infected for 227 days, it’s safe to conclude that the attackers stole everything… from everyone.
If you or a family member are or were a member of the PSEA, you need to go into serious identity theft incident response mode.
For the rest of us, this is a timely and regrettable reminder that we need to work harder to achieve a dwell time of zero!
The News…
A former University of Michigan football coach has been indicted on multiple counts of unauthorized use of a computer and aggravated identity theft. The man illegally accessed athlete databases, obtaining personal information and medical data of over 150,000 athletes. He then accessed social media, email, and cloud storage accounts of more than 3,300 persons, downloading intimate photographs and videos. https://www.justice.gov/usao-edmi/pr/former-university-michigan-football-quarterbacks-coach-and-co-offensive-coordinator
Well, it was guaranteed passive income for the scammers. The Federal Trade Commission (FTC) has temporarily halted a business opportunity scheme called Click Profit, which has taken millions from consumers by falsely promising them large profits through online sales. The FTC alleges that Click Profit and its owners deceived consumers by claiming guaranteed passive income through AI technology and exclusive brand partnerships and that few consumers see returns on their investments, with many losing tens of thousands of dollars. https://www.ftc.gov/news-events/news/press-releases/2025/03/ftc-acts-stop-click-profit-online-business-opportunity-has-cost-consumers-least-14-million
Some financial controls, please. A borough in Pennsylvania was victimized by a phishing scam in 2024, resulting in the loss of $65,000. The scam involved fraudulent emails from a company claiming to be a consulting firm the borough had hired to address a parking lot issue. The scammers tricked the borough into sending a wire transfer, which was deposited into the bank account of a woman in Indiana who refused to cooperate with the investigation and has not been charged. https://www.yorkdispatch.com/story/news/crime/2025/03/25/how-red-lion-borough-lost-65000-to-a-phishing-scam-and-how-you-can-protect-yourself/82651456007/
Google has patched a zero-day exploit facilitating one-click phishing attacks on Chrome users. https://www.darkreading.com/cyberattacks-data-breaches/google-patches-chrome-zero-day-exploited-apt
A phishing kit, dubbed “Morphing Meerkat,” utilizes DNS MX records to serve tailored login pages, spoofing over 100 brands dynamically. The kit, likely from a phishing-as-a-service platform, exploits open redirects and compromised domains for credential distribution. https://blogs.infoblox.com/threat-intelligence/a-phishing-tale-of-doh-and-dns-mx-abuse/
Using a technique called “Fun Tuning,” attackers are now using AI to manipulate AI. https://bgr.com/tech/hackers-are-now-using-ai-to-break-ai-and-its-working/
Orin Kerr has a new book titled “The Digital Fourth Amendment” where he attempts to answer the question: “What are the legal rules for collecting all of this digital evidence?” https://reason.com/volokh/2025/03/26/the-idea-of-my-new-book-the-digital-fourth-amendment-and-why-it-matters/
DFIR
Doug Metz tackles the stress of being a DFIR practitioner and gives some tips to find Zen. https://bakerstreetforensics.com/2025/03/25/zen-the-art-of-digital-forensics/
Reader Mail
Matt, your newsletter this week was spot on. My organization has been dealing with a slew of account takeovers, and my managers didn't seem satisfied with my explanation of how the attackers got the information so easily. Your writing was a good backup to what I've been saying. - Kim
Glad to have helped, Kim. BTW, do you know the definition of an expert? Someone 60 miles from home with a PowerPoint slide show. Rarely are you recognized as an expert in your own workplace. It’s a human tendency to overlook what’s right in front of us and give extra weight to something foreign.
(See issue 227 for reference)
Cool Job
Senior Financial Crime Investigator - Major Crimes and Emerging Threats, Virginia Attorney Generals Office. https://www.jobs.virginia.gov/jobs/senior-financial-investigator-major-crimes-and-emerging-threats-richmond-virginia-united-states
Cool Tool
Advanced Reddit search operator - https://www.redective.com/
Remember GeoCities pages? Bring on the nostalgia. https://geocities.live/
Irrelevant
What’s the average case of beer cost in your state? Someone figured it out. https://www.visualcapitalist.com/mapped-how-much-a-24-pack-of-beer-costs-in-each-u-s-state/
Sign Off
First thing first, welcome new subscribers. I’m so happy you’re giving the newsletter a chance. I realize there is immense competition for your time, and I don’t take that you're giving me a few minutes for granted.
Second, the greatest game began its regular season this week. We fans of the Pittsburgh Pirates live by the saying, “don’t expect too much, and you won’t be let down. " It’s still great to watch the game, even if your team hasn’t been to the World Series since you were in kindergarten.
See you next Tuesday.
Matt
“April 1. This is the day upon which we are reminded of what we are on the other three hundred and sixty-four.” - Mark Twain
Published every Tuesday, Threats Without Borders offers original commentary and educational pieces related to cybercrime investigations and information security topics. We also summarize and comment on news articles concerning active threat intelligence for the financial industry. The newsletter interests everyone tasked with cybersecurity or involved in preventing or investigating technology-enabled fraud, theft, or money laundering.
Legal: I am not compensated by any entity for writing this newsletter. Obviously, anything written in this space is my own nonsensical opinions and doesn’t represent the official viewpoint of my employer or any associated organization. Blame me, not them.
cybersecurity cybercrime cyficrime aml fraud investigations financial crime