Threats Without Borders - Issue 231
Cybercrime Investigation Newsletter, week ending April 20, 2025
Matt, do you have any suggestions for how we should respond to local businesses that report a ransomware attack to us? We recently had a construction company report an attack to us, and the only thing we could offer was to contact the local FBI office. Is there anything else we should do?
Well, you weren’t wrong. As a municipal police department, many times your only option is to facilitate communication with a federal partner.
But let’s get one thing clear, and this is something most law enforcement officers fail to accept, or even understand:
The incident remediation and system restoration is not the responsibility of law enforcement- local, state, or federal. Period. End of story.
Your job is to investigate the criminal act, not repair the damage done to a private party's property. As much as you want to assist, and even if you are capable of helping – don’t! You are only opening your agency and yourself up to liability.
Hopefully, by the time you get called, they have already contacted their IT services provider and insurance company, and the incident response process is already underway. However, it’s not uncommon for small businesses to become completely overwhelmed and do the only thing they know to do when things go wrong…call 911.
So what can you do?
Stop the bleed: Ensure the owner takes action to mitigate the infection. Again, you should not go hands-on with their network, but ensure they have taken steps to disconnect their hardware from the Internet. Honestly, once they become aware of the infection, it’s too late, but as a general rule, get the systems offline as soon as possible.
If you are the first responder on the scene, take a picture of the monitor screens or the ransomware note displayed so that future responders will know which ransomware group they are dealing with and how to contact them.
Don’t allow the business owners or employees to attempt communication with the ransomware group, and for goodness' sake, don’t try to do it yourself. A trained professional must handle these communications. Negotiation for a reduced ransom is crucial, particularly in a case with data exfiltration, and you don’t want to enrage the extortionist or give them leverage.
Contact the insurance company. If they have cyber insurance, this might be the only phone call you need to make. Most insurance companies have a workflow that initiates and coordinates the response of legal entities and incident responders.
If they don’t have an insurance policy, direct them to contact a ransomware incident response firm. You should not recommend a company by name, as this will only expose you to liability if things go wrong. I usually suggest they perform an Internet search for a local or regional firm, such as “Cyber and Ransomware Incident Response in Pennsylvania.” Most quality firms will have an ‘immediate response’ or ‘are you under attack’ phone number listed at the top of their website. Unfortunately, it’s not the time to inquire about costs or ask for references; that should have been done before the house caught fire.
Contact the local FBI field office. It’s unlikely that a special agent will respond, but they track the incidents, and they may be able to assist or offer guidance. The Bureau has recently improved its efforts to help victims and even break the encryption schemes used by some ransomware strains. Also, assist them in filing a report with the Internet Crime Complaint Center at IC3.gov.
And the most important thing you can do is be supportive. Communicate to the victims that they didn’t deserve any of this. A little empathy goes a long way.
The News…
Shocker, cops are using AI to be more effective. Of course, certain groups in America don’t want effective law enforcement. Several police departments are using an AI-powered technology to collect intelligence on criminal suspects, radicalized activists, and human traffickers. Developed by Massive Blue, a New York-based company, the tool creates lifelike virtual agents that infiltrate and engage criminal networks across various channels. The technology uses AI-generated images and text to create social media profiles that can interact with suspects over text, Discord, and other messaging services. Opponents of the tool have raised concerns about its potential to violate protesters' First Amendment rights and the lack of transparency surrounding its use and effectiveness. https://www.wired.com/story/massive-blue-overwatch-ai-personas-police-suspects/
Phishing emails impersonating the U.S. Department of Homeland Security (DHS) have increased, exploiting recent immigration policy changes and confusion surrounding I-9 regulations. These emails, detected by INKY, target businesses and individuals, using topics like executive orders and unclaimed funds. https://www.inky.com/en/blog/fresh-phish-targeted-dhs-impersonations-spike-amid-u.s.-deportation-surge
Researchers have discovered a new tactic used by a cybercrime group to attack big-box retailers and other companies. They use stolen credentials to enroll their own virtual machines into a company's cloud domain, allowing their cybercrime infrastructure to appear as a legitimate part of the company's network. Once inside, the attackers create a Windows virtual machine, connect it to the organization's domain, and use it to obtain gift card codes and other sensitive information. https://therecord.media/atlas-lion-gift-card-cybercrime-hiding-virtual-machines
The Lackawanna County District Attorney’s Office (PA) and the University of Scranton entered into an agreement to create an internship program. The students will work with the agency's digital forensic investigators. https://www.thetimes-tribune.com/2025/04/16/university-of-scranton-das-office-in-new-cybercrime-partnership/
Beaufort County Sheriff’s Office (SC) reports a surge in mail thefts, with over a dozen checks stolen and cashed since early March. The agency attributes the rise to criminals targeting mailboxes, including blue postal boxes. Of course. https://www.wjcl.com/article/beaufort-county-mail-theft-check-fraud/64505680
Reader Mail
Last week (Issue 230) I asked the question, “What is your one thing?”. What is the one thing you see non-security people do daily that makes you cringe the hardest?
When customers give their account information and online banking credentials to fraudsters…….ugh!!!!!! As you know Matt, banks would never ask for that information. - Mike
Enjoyed reading your article. The one thing that would make me cringe is users repeating the same mistake over and over. As the old saying goes - "Fool me once, shame on you. Fool me twice, shame on me" - Chuck
Easy one. Paying for a third-party anti-virus. Even worse, turning off Defender to pay for another AV. - KB
Let’s turn this around on us. How about the one thing security people do that makes me cringe? Absolutely, wearing a hat or shirt that says “HACKER”. It might as well say D-Bag. -Eric
Strong take, Eric. If I get any unsubscribes this week, we’ll know who wears Hacker gear on the weekends.
Will the real IC3 please stand up.
The FBI warned that scammers are impersonating the Internet Crime Complaint Center (IC3). The agency claimed to have received over 100 reports of IC3 impersonations. Victims are invited to report the scam to the IC3. Of course, make sure you're calling the real IC3 and not an IC3 impersonator.
https://www.ic3.gov/PSA/2025/PSA250418
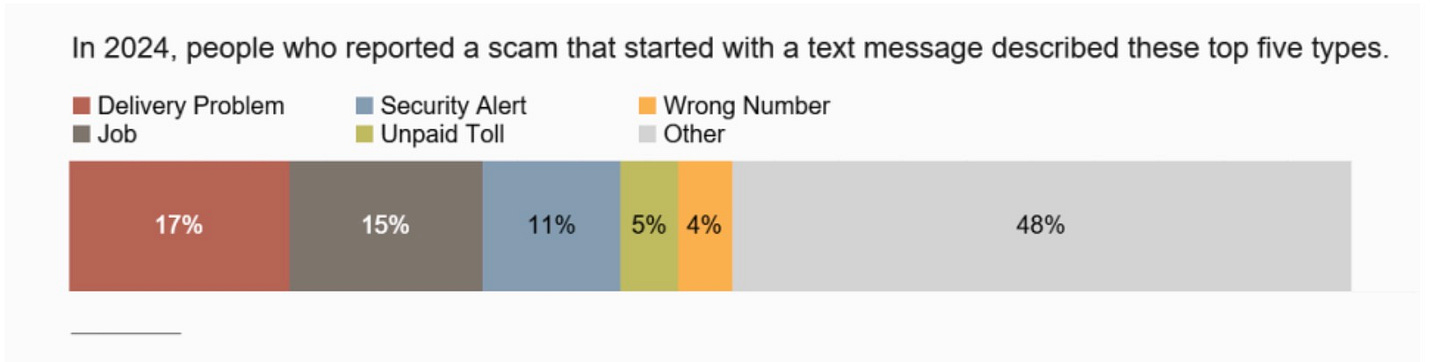
Text Scams
The Federal Trade Commission released a report detailing the top five text-based scams reported to the agency in 2024. The top five are:
Package delivery notifications
Job opportunities
Fraud alerts
Unpaid roadway tolls
Misdirected “wrong number” texts
https://www.ftc.gov/news-events/data-visualizations/data-spotlight/2025/04/top-text-scams-2024
DFIR
Kevin Pagano discusses the storeuser.db database of iOS devices, which contains details on app installs and purchases from the App Store. https://www.stark4n6.com/2025/04/tracking-ios-app-installs-and-purchase.html
Cool Tool
What was that? Go Back! Slow it down. This tool allows you to watch YouTube videos in slow motion and even frame by frame. http://www.watchframebyframe.com/
Cool Job
Global Investigator - National Security, TRM Labs. https://job-boards.greenhouse.io/embed/job_app?for=trmlabs&token=5495185004
Irrelevant
They did a study to see if swearing during strenuous physical activity makes you stronger. Hell yeah, it does! Swear more to increase your grip strength by 9% and plank time by 12%. https://www.frontiersin.org/journals/psychology/articles/10.3389/fpsyg.2024.1445175/full
Sign Off
Thank you for sticking around another week. As always, feel free to send comments, suggestions, or hate to matt[at]threatswithoutborders.com.
See you next Tuesday.
Matt
“IF YOU COULD ERASE ALL THE MISTAKES OF YOUR PAST, YOU WOULD ALSO ERASE ALL THE WISDOM OF YOUR PRESENT.”
Published every Tuesday, Threats Without Borders offers original commentary and educational pieces related to cybercrime investigations and information security topics. We also summarize and comment on news articles concerning active threat intelligence for the financial industry. The newsletter interests everyone tasked with cybersecurity or involved in preventing or investigating technology-enabled fraud, theft, or money laundering.
Legal: I am not compensated by any entity for writing this newsletter. Obviously, anything written in this space is my own nonsensical opinions and doesn’t represent the official viewpoint of my employer or any associated organization. Blame me, not them.
cyficrime cybersecurity cybercrime aml investigations osint financial fraud