Threats Without Borders - Issue 232
Cybercrime Investigation Newsletter, week ending April 27, 2025
Tim Otis, Director of Incident Response for Checkpoint, delivered the closing keynote for the BSides Harrisburg conference on Friday. During the Q/A portion, he said something so intuitive, so accurate, that it needs to be amplified. And he said it completely aside, not as a point of his talk.
While AI may become essential to cyber investigations, it will never replace the process because it can’t replace the “detective brain”.
Detective Brain. I’ve never heard it referred to that way, but it’s the best description I’ve encountered for that innate quality of curiosity and persistence that good investigators possess to recognize a lead and follow it, no matter where it takes them.
The ability to notice something is out of the usual, formulate a hypothesis, and then test it ad nauseam until proven or disproven. And then repeat.
AI accepts what it’s told. Good investigators never accept what is told on the face, and only believe the information after confirming it for themselves.
Good investigators go down the rabbit hole until they have hit bedrock or run out of oxygen.
Good investigators recognize signs of deception and attack it until the truth is revealed.
Criminal investigations, addressing traditional crime or cyber, rely on human skills and emotions that a machine can’t yet replicate or replace.
Curiosity, Interest, Persistence, Empathy, Sympathy, Anger, Rage, Vigilance, Grief, Disapproval, Disgust, Patience, Pessimism, Pride, Vengeance!
Maybe someday machines can replace these human emotions and channel them into the investigative process, but I don’t think it will be anytime soon.
All the reports!
Someone must organize these groups and create a schedule for their product distributions over time. Three of the most anticipated industry reports were published within the past week.
Internet Crime Complaint Center (IC3) - 2024 Internet Crime Report https://www.ic3.gov/AnnualReport/Reports/2024_IC3Report.pdf
Google Mandiant - M-Trends 2025 https://services.google.com/fh/files/misc/m-trends-2025-en.pdf
Verizon Data Breach Investigations Report https://www.verizon.com/business/resources/T231/reports/2025-dbir-data-breach-investigations-report.pdf
I encourage you to take the time to read each of these reports. I will publish some nuggets from each over the next few weeks.
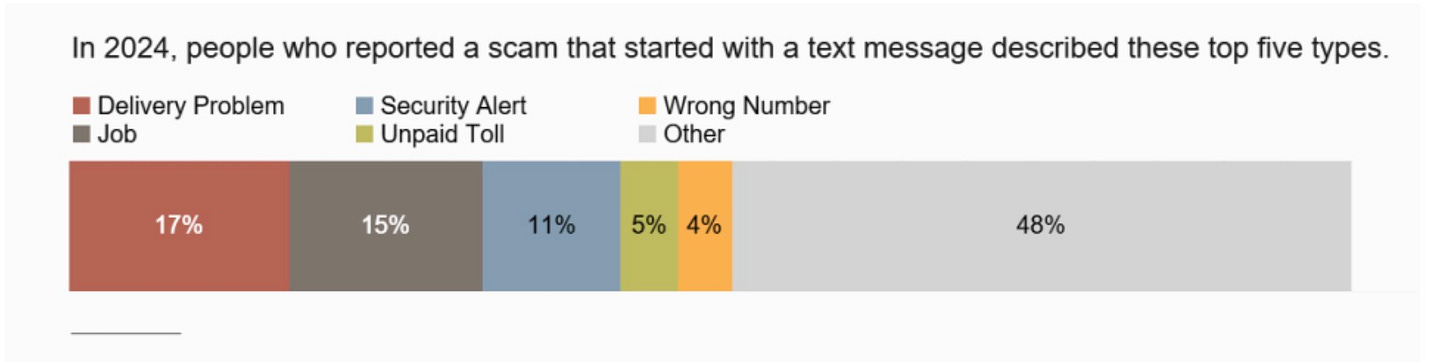
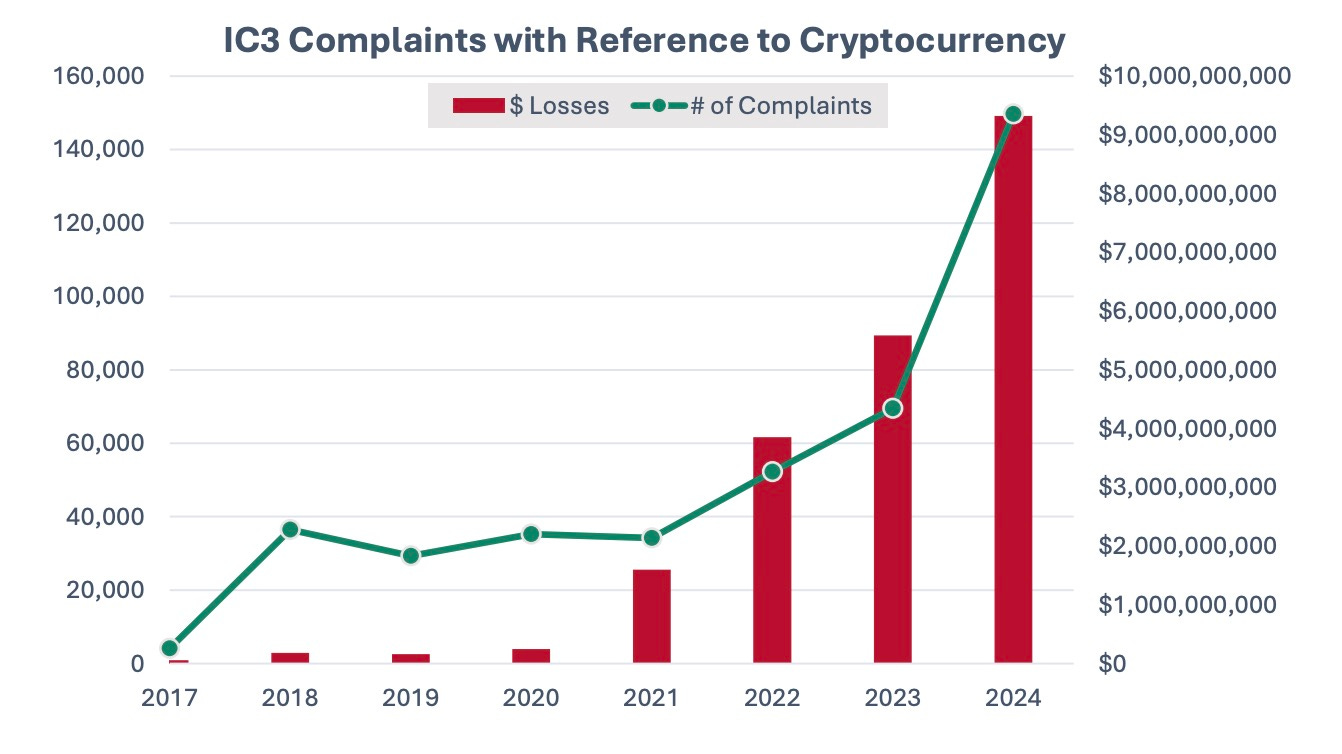
Speaking of the Internet Crime Report, one of the key insights is the breakdown of the top ways funds are lost in fraud, or how attackers convert victims' money into their own. By dollar amount, cryptocurrency dwarfs gift cards, but I don’t think that’s truly representative of the extent of gift cards' involvement in cybercrime. Most conversions through gift cards involve relatively low dollar amounts- typically a few hundred or maybe a thousand dollars- while Big Company X is paying their 800K ransomware payment through crypto. Victims are less likely to report low-dollar losses. Additionally, victimized legal companies usually have reporting requirements set by law or compliance standards. John, who lost $200 in a Facebook Market Place scam, does not
However, we can’t ignore this trend.
66% increase in losses, and the largest victim group is those over the age of 60. I can’t help but think there is a direct correlation between this increase in losses through cryptocurrency and the increased prevalence of Bitcoin ATM machines. In the past, it was a huge hurdle to get older people to convert their cash into crypto; now it’s as easy as giving them the address of their local crypto-ATM machine. It’s almost zero friction.
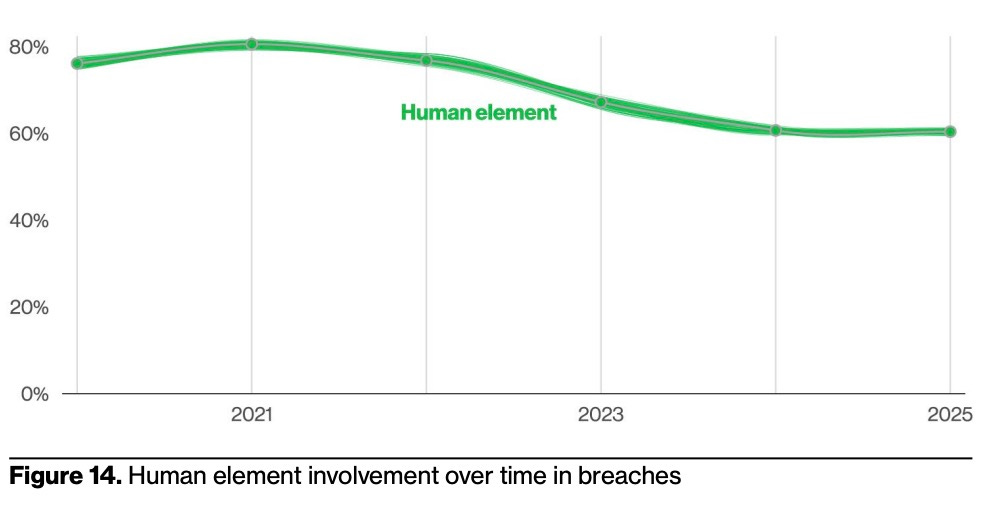
For some good news, the Verizon report indicates that awareness training is having a positive effect, as human responsibility for breaches has decreased to 60% from the 80% it was a few years ago.
The News…
Hudson Rock examines the state of Info Stealer malware. https://www.infostealers.com/article/private-stealing-the-future-infostealers-power-cybercrime-in-2025/
The race begins to see which DFIR organization will develop the first tool to exploit Windows Recall, which Microsoft is making public nearly a year after its announcement. Recall takes continuous screenshots of user activity, saving them in a searchable database, and has major security and privacy implications. Microsoft claims to have added security protections, automated content filtering, and made Recall an opt-in feature that can be completely removed. The feature is only available on Copilot+ PCs, which require a neural processing unit (NPU) that supports over 40 trillion operations per second. https://arstechnica.com/gadgets/2025/04/microsoft-rolls-windows-recall-out-to-the-public-nearly-a-year-after-announcing-it/
Canadians like drugs too! The SOCRadar blog examines the We The North marketplace, a Canada-focused dark web marketplace launched in 2021, which offers illegal goods and services, particularly drugs. It has both clear web and TOR addresses. https://socradar.io/dark-web-market-wethenorth-market/
A former Disney employee was sentenced to three years in federal prison for computer intrusions against his former employer. He hacked into the systems to manipulate allergen information, altered menu details, and launched denial-of-service attacks. https://www.wptv.com/news/state/fired-disney-employee-gets-3-years-in-prison-for-hacking-and-changing-menus
This article is from February, but I just read it. Russian threat actors have been targeting Microsoft 365 accounts using highly tailored spear-phishing campaigns. These attacks utilize social engineering to deceive users into entering a Device Code Authentication workflow. This enables attackers to gain long-term access to user accounts, even if multi-factor authentication (MFA) is enabled. The attacks often commence with fake invitations to secure chat applications like Element, which trick users into clicking links that redirect to the Microsoft Device Code authentication page. https://www.volexity.com/blog/2025/02/13/multiple-russian-threat-actors-targeting-microsoft-device-code-authentication/
DFIR
The ForensicFossil blog explains how to use open source tools to find evidence of persistence within an infected system. https://forensicfossil.com/2025/04/detecting-persistence-with-open-source-tools
Reader Mail
Oh, are we hating on cyber guy too? How about the CISSP who can’t write his name without ending it CISSP, on every single email or form. You’re just approving my travel expense, accounting doesn’t care you passed a test! CV in KC
Cool Job
Chief Information Security Officer - Major League Soccer. https://careers-mlssoccer.icims.com/jobs/2132/chief-information-security-officer/job
Cyber Intelligence Senior Associate - JPMorganChase https://jpmc.fa.oraclecloud.com/hcmUI/CandidateExperience/en/sites/CX_1001/job/210615004
Cool Tool
Explore the blockchain (15 free searches per day) https://lite.crystalintelligence.com/
Irrelevant
For your tech-loving mother. https://www.theverge.com/tech/647527/best-mothers-day-gift-ideas-2025-mom-tech-gadgets
Events
The Layer 8 Conference is dedicated to social engineering and intelligence gathering investigation skills. It will be held on June 14, 2025, in Boston, MA. Fifty-dollar tickets include lunch. https://layer8conference.com/
The Keystone Connection Conference brings together the Delaware Valley chapter and the Pittsburgh Metro chapters of the International Association of Financial Crime Investigators for its yearly training event. This year in State College, Pennsylvania! https://keystonekonnection.com/
Sign Off
At my (real job), I have been tasked with creating a monthly newsletter to provide fraud and financial crime prevention information to our customers. I mentioned that I already do this every week and questioned whether we could sign everyone up for a subscription to "Threats Without Borders.”?
I have attended numerous conferences over the years, so I know the difference between a good event and a shit show. The BSides Harrisburg conference has grown into one of the best conferences in the nation. It is organized and well-run, and they do an excellent job of mixing up the speakers, including seasoned professionals and first-timers at the podium. I was the Emcee of the Track 1 room and had a student deliver one of the best talks I heard all day, definitely the best student presentations I’ve heard in a really long time. Well done, Carolina. Messiah University should be proud!
Thanks for reading this weeks issue. See you next Tuesday!
Matt
Published every Tuesday, Threats Without Borders offers original commentary and educational pieces related to cybercrime investigations and information security topics. We also summarize and comment on news articles concerning active threat intelligence for the financial industry. The newsletter interests everyone tasked with cybersecurity or involved in preventing or investigating technology-enabled fraud, theft, or money laundering.
Legal: I am not compensated by any entity for writing this newsletter. Obviously, anything written in this space is my own nonsensical opinions and doesn’t represent the official viewpoint of my employer or any associated organization. Blame me, not them.
cybersecurity cyficrime aml financial fraud investigation cybercrime osint