Threats Without Borders - Issue 233
Cybercrime Investigation Newsletter, week ending May 4, 2025
So, this guy in New Jersey gets socially engineered and allows the bad guys access to his cryptocurrency wallet. Ouch! The attackers promptly transferred out 521 Bitcoin worth over 40 MILLION dollars at the time. Double Ouch!
He hires a crypto-forensic firm to investigate, and they trace all the bitcoin transactions through the public blockchain. He has now filed a lawsuit against the cryptocurrency exchange services hosting the dirty wallets, demanding that they freeze them. The judge agreed, granting a preliminary injunction requiring that the wallets be frozen pending further consideration.
The lawsuit masterfully lays out the social engineering attack. In fact, it almost serves a how-to for other scammers to follow.
Reading the lawsuit will be well worth your time; it is educational. https://storage.courtlistener.com/recap/gov.uscourts.njd.564066/gov.uscourts.njd.564066.1.0_1.pdf
The Q1 2025 Email Threat Research Report from Sublime Security is loaded with tons of information, which makes it pretty tough to take it all in at once. It’s filled with important data and insights that are key for anyone wanting to keep up with the changing world of email threats. A must-read for sure!
Earlier this year, I raised some hackles when I challenged the popular notion that criminals are extensively using AI to commit cyber fraud. It’s not that they’re not using it; it’s that the old ways of fraud still work so well that many haven’t needed to expand their toolbox to include AI. At least, I hadn’t seen anything other than anecdotal examples of the shift.
Well, this report provides data showing a shift to AI for creating unique phishing emails. Ninety percent of the malicious emails observed by Sublime in Q1 exhibited signs of customization aimed at creating messages unique to their targets. Additionally, the emails indicated the use of AI to facilitate these customizations.
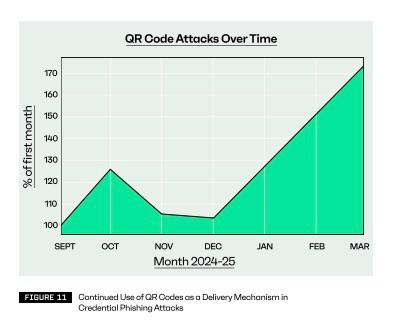
The report also emphasizes the growing prevalence of QR codes in phishing emails, with data indicating a 40-60% rise since Q4 2024. Be sure to bring this to the attention of your marketing and communications teams, as they appreciate being informed about the risks associated with QR codes. Just make sure they’re not holding sharp objects when you do it.
Read the full report:
Over the past week, you couldn’t swing a dead cat without hitting a cybersecurity blogger or newsletter writer blathering about the Internet Crime Report or the Verizon Data Breach Investigations Report. And I love these reports also. But, rather than focus on the high-level points like most, I enjoy digging into the text and finding the nuggets.
And I found this gem in the Verizon DBIR.
Who causes more damage when breached, large organizations or small ones? You might say, large organizations, of course. They always have more data to lose. Nope. Just because an organization is small by employee count and qualifies for the tag of Small and Medium Business (SMB) doesn’t mean they don’t control an immense amount of data.
A reasonable question might be “Ok, so SMBs may be vulnerable, but surely the impact of a breach of an SMB is, by nature, considerably less than for a large organization, right?” Wrong. May we direct your attention to the calamitous fiasco of the National Public Data breach that occurred in 2024. The company, which aggregated data for use in background checks, was breached, and 2.9 billion records were put up for sale (including Social Security numbers, dates of birth and addresses) on the dark web containing information of citizens of the U.S., Canada and the U.K. This was good news to the threat actors and vendors offering credit monitoring services. But this breach illustrates perfectly the type of outsized damage that an organization with literally a handful of employees can cause to the data victims affected.
2025 Verizon DBIR, Page 87.
The News
Matt O’Neill published this hot take on the BioCatch blog, and although I don’t completely agree with him, I appreciate his effort to move the ball forward. The United States does have a fragmented law enforcement response to financial crime, and we absolutely need to coordinate a stronger national response. This includes designating an agency to lead the effort. I step back when he calls for the U.S. Secret Service to take the lead, not because I have beef with The Service, but because their agents regularly get pulled from investigative duties for protection duties. You can’t have case agents being pulled from active investigations to stand guard at the U.N. or babysit some foreign head of state coming to the country on summer vacation. Not to mention, what happens every four years. I’ll be on board if they straighten that problem out. Regardless, the piece is worth reading. https://www.biocatch.com/blog/who-is-leading-fight-against-scams
Darktrace gives examples of threat actors using new methods to bypass security, including Attackers in the Middle (AitM) phishing kits and legitimate services like Milanote. The article provides strong support for why user awareness education is crucial for defense. https://www.darktrace.com/blog/mfa-under-attack-aitm-phishing-kits-abusing-legitimate-services
Adam Goss at Kraven Security explains how to create a cyber threat intelligence process for your organization. https://kravensecurity.com/intelligence-collection-plan/
The “Chainalysis 2025 Crypto Crime Report* highlights how organized crime groups have adapted to the rise of cryptocurrency, using it for crimes such as drug smuggling, human trafficking, and intellectual property theft. Despite their increasing use of crypto, these groups often lack the technical expertise to conceal their financial dealings effectively, making it easier for investigators to trace their operations. The report suggests that although traditional organized crime networks have turned to crypto for its speed and perceived anonymity, they often expose their financial dealings, enabling law enforcement to detect and disrupt their activities. https://www.chainalysis.com/blog/organized-crime-crypto/
Sentinel One wants us to know that they aren’t only battling against the U.S. Government; as one of the largest cybersecurity service providers, they are also targeted daily by actual adversaries like China and North Korea. https://www.sentinelone.com/labs/top-tier-target-what-it-takes-to-defend-a-cybersecurity-company-from-todays-adversaries/
Epic finally prevails over Apple, allowing developers to direct you outside of the Apple Store for external purchases. https://www.theverge.com/news/660025/apple-changes-app-store-rules-to-allow-external-purchases
Employee monitoring software always seems like a good idea at the time. They say we’re going to catch employees who are slacking off and wasting company time. But what happens when the software company loses all the information it collected from your employees, including screenshots showing sensitive company and customer information? Oh, we never thought about that, they say. https://gizmodo.com/an-employee-surveillance-company-leaked-over-21-million-screenshots-online-2000593880
Particularity….PLEASE
A 24-year-old was caught with a 14-year-old runaway. The minor informed the police that they were in love and had, in fact, engaged in sexual relations on multiple occasions. The adult was arrested and his cell phone was seized.
Weeks later, an investigator obtains a search warrant to search his phone. The officer used cookie-cutter language of:
All call information, including voice mail messages, all outgoing and incoming calls, missed calls, recent calls, call logs, text messages, including incoming and outgoing messages, multimedia messages, including incoming and outgoing, IMEI numbers, serial number and any other numbers used to identify cell phones as well as any other information within said phone that may be deemed evidence that a crime has been or is about to be committed.
Y’all will be shocked; child sexual assault material was found on the device. The guy gets federally indicted and promptly moves to suppress the evidence from the phone on the grounds that the search was overbroad, in violation of the Fourth Amendment.
The 10th Circuit Court of Appeals agrees.
The court ruled:
Santiago’s case is a classic example of the kind of general search the Fourth Amendment is intended to prevent. It lists a variety of specific places within the iPhone that should be searched but then says, “as well as any other information within said phone that may be deemed evidence that a crime has been or is about to be committed.” Rec., vol. I at 42–43. The state search warrant does not attempt to narrow this instruction by mentioning the crimes with which Mr. Santiago has been charged.
https://www.ca10.uscourts.gov/sites/ca10/files/opinions/010111227629.pdf
feedback: matt[@]threatswithoutborders[.]com
Cool Job
Senior Director of Governance, Risk, and Compliance - Major League Baseball. https://www.mlb.com/careers/opportunities?gh_jid=6643135
Cool Tool
Tool designed to help find subdomains that are vulnerable to takeover. https://github.com/dub-flow/subsnipe
An AI tool that assesses a Reddit user and forms opinions about them. https://rrc.fyi/
DFIR
Close to the entirety of USB drive forensics knowledge condensed into a single blog post. https://hackmd.io/@M4shl3/USB-Forensics
Irrelevant
Good-Bye, Skype. You changed the world. https://techcrunch.com/2025/05/05/skype-is-shutting-down-today-these-are-the-best-alternatives/
credit: u/oranke_dino
Sign Off
I’m considering a new section, “Who did I tick off last week?”. Unsubscribers are normal, but I know peoples feelings got hurt when I receive a few within a short time after publishing the newsletter on Tuesday morning. Judging from last week, I assume a few of my former subscribers like to ensure everyone knows they passed a test.
For the rest of you, thank you for staying with me. See you next Tuesday!
Matt
“THE TRUTH IS NOT ALWAYS BEAUTIFUL, NOR BEAUTIFUL WORDS TRUTHFUL.”
Published every Tuesday, Threats Without Borders offers original commentary and educational pieces related to cybercrime investigations and information security topics. We also summarize and comment on news articles concerning active threat intelligence for the financial industry. The newsletter interests everyone tasked with cybersecurity or involved in preventing or investigating technology-enabled fraud, theft, or money laundering.
Legal: I am not compensated by any entity for writing this newsletter. Obviously, anything written in this space is my own nonsensical opinions and doesn’t represent the official viewpoint of my employer or any associated organization. Blame me, not them.
cybersecurity cybercrime cyficrime osint aml fraud investigation financial crime