Threats Without Borders - Issue 234
Cybercrime Investigation Newsletter, week ending May 11, 2025
As much as I cling to gift cards, I acknowledge that cryptocurrency has rapidly become the preferred method for cybercriminals to monetize fraud and move money across borders, thanks to its unique blend of speed, anonymity, and decentralization. Although gift cards make it so easy to move funds, cryptocurrency transfers much larger amounts of money. And unlike traditional financial systems that rely on regulated banks and centralized oversight, cryptocurrency transactions occur peer-to-peer on public blockchains, where wallet addresses are not tied to real-world identities. This pseudonymity enables criminals to send and receive funds with far less risk of detection. Additionally, cryptocurrencies like Bitcoin and Monero can be transferred globally in minutes, bypassing financial institutions, sanctions, and anti-money laundering controls.
The growing ecosystem of crypto-based laundering tools further facilitates cybercrime. Services like mixers, tumblers, and decentralized exchanges obscure the origin of funds by blending transactions or avoiding KYC requirements altogether. Privacy-focused coins add another layer of concealment, making forensic tracing exceptionally difficult. Criminals leverage these tools to cash out profits from ransomware attacks, phishing scams, online fraud, and the sale of stolen data on dark web markets.
In many regions of the world, jurisdictional issues and lax regulations facilitate the exploitation of crypto by threat actors. The absence of consistent global enforcement allows criminals to transfer illicit funds via unregulated exchanges with minimal risk of detection or asset confiscation. Additionally, reversing the transaction is almost impossible once cryptocurrency is moved, unlike with wire transfers or bank payments.
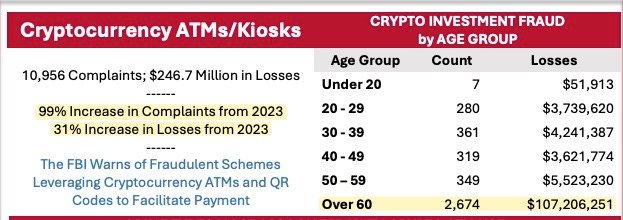
The most recent Internet Crime Report from the FBI’s Internet Crime Complaint Center (IC3) highlights the reality of the situation. Additionally, it correctly correlates the rise in cryptocurrency as a fraud tool with the increased availability of cryptocurrency ATMs. This particularly affects fraud victims over the age of 60.
The crypto-ATM eliminates all the friction of educating future fraud victims about the use of cryptocurrency. No more explaining how to create an account with a cryptocurrency exchange, no more frustrating communications demonstrating how to install and set up apps on a smartphone, and no more interference from friends and family members who can derail the process when consulted for help on using the technology. Nope, download the app, create an account, give them a QR Code for a wallet address and directions to the closest Bitcoin ATM. It’s that easy.
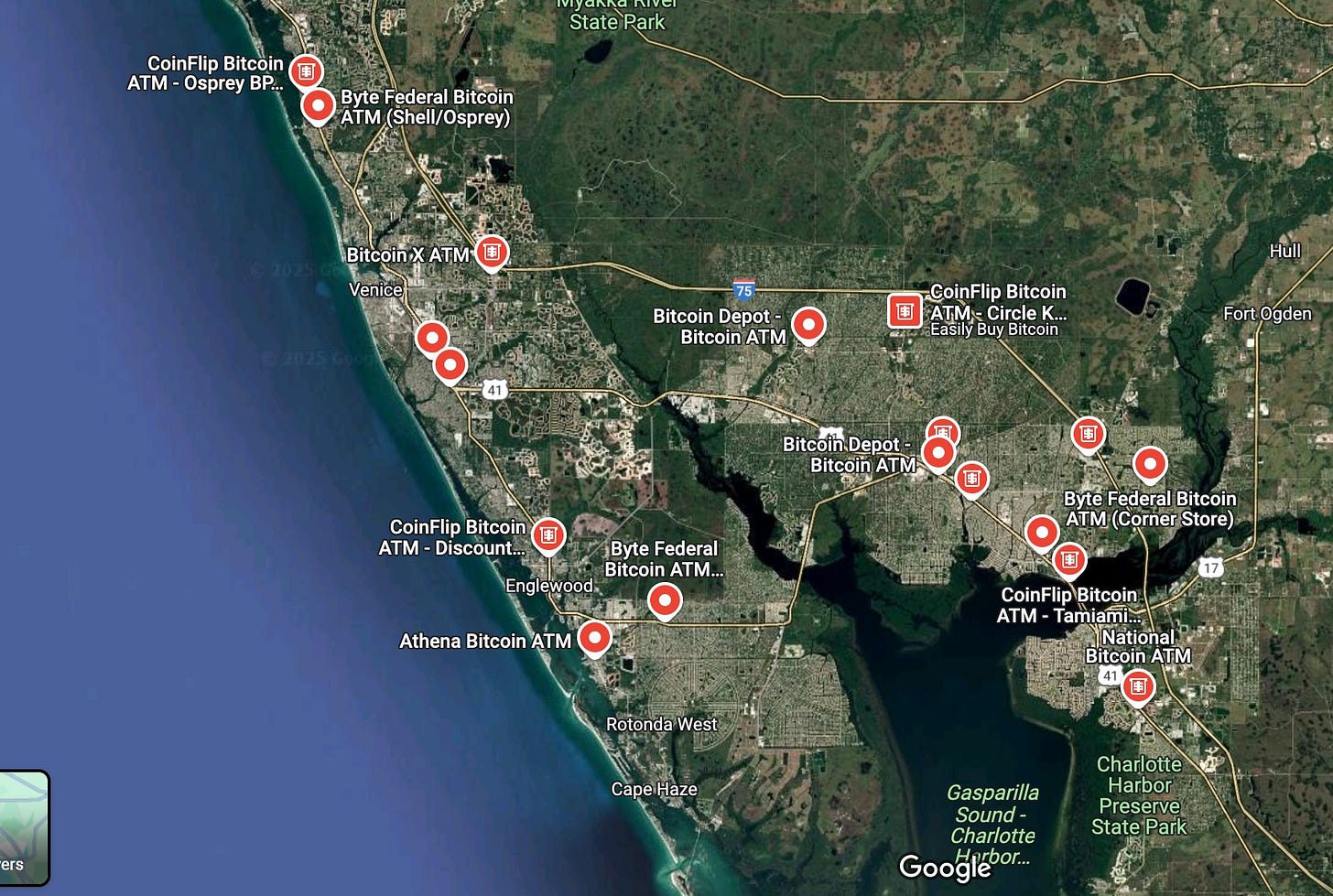
Speaking of local crypto-ATMs, they are springing up everywhere, which undoubtedly facilitates their use in fraud.
A quick search of Google Maps shows their prevalence in the Harrisburg, PA area.
And to provide perspective, here is a map of the Venice/Port Charlotte area of Florida (Gulf Coast), which certainly has an abundance of residents aged over 60.
Seriously, how many legitimate transactions are being run through all of these terminals?
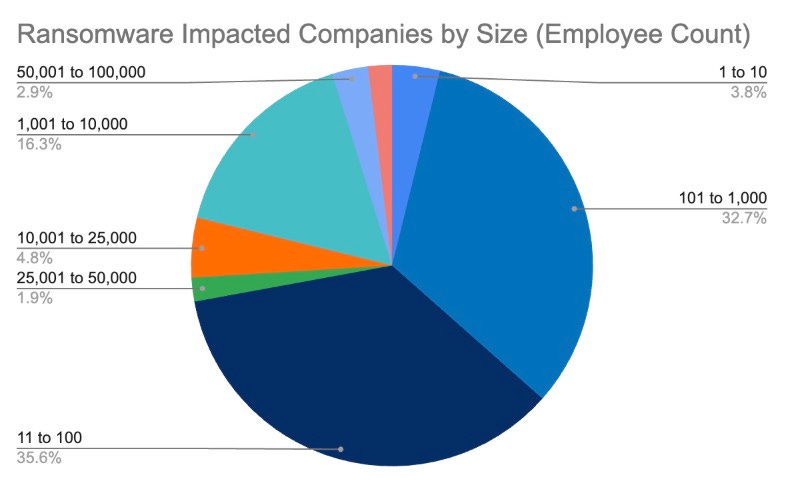
According to new data published by Coveware, in Q1 2025, ransomware attacks primarily impacted small and mid-sized businesses. The average targeted organization employed 228 people, highlighting that ransomware groups often focus on these firms due to their limited cybersecurity capabilities, especially awareness training. Companies with 11 to 100 employees represented 35.6% of the attacks, while those with 101 to 1,000 employees accounted for 32.7%.
feedback: matt [@] threatswithoutborders [.] com
The News…
Flashpoint analysts have identified several prominent threat actors targeting the financial sector. They employ various tactics such as phishing, exploiting vulnerabilities, and compromising remote services to gain initial access and exfiltrate sensitive data. The financial sector is particularly vulnerable to ransomware attacks, with 406 publicly disclosed victims falling prey to ransomware alone, representing seven percent of all ransomware victim listings during that period. https://flashpoint.io/blog/top-threat-actor-groups-targeting-financial-sector/
Google will embed AI process into Chrome to stop tech-support scams. https://security.googleblog.com/2025/05/using-ai-to-stop-tech-support-scams-in.html
Cyber insurance provider Coalition released its 2025 Cyber Claims Report. Their data indicates that in 2024, 29% of all business email compromise events resulted in a funds transfer fraud incident. They also indicate that in the second half of 2024, the average ransom demand fell below $1 million for the first time in two years. https://www.coalitioninc.com/blog/2025-cyber-claims-report
This Social Security Administration-themed phishing attack tricks recipients into downloading and launching the ScreenConnect remote desktop tool executable. Unfortunately, people concerned about their Social Security statements generally do not recognize the difference between a file with a .pdf extension and one with a .exe. https://www.malwarebytes.com/blog/news/2025/04/fake-social-security-statement-emails-trick-users-into-installing-remote-tool
The FBI warned that threat actors are deploying malware on end-of-life routers, converting them into proxies for malicious activities. These compromised routers are added to botnets and used to route malicious traffic. https://www.ic3.gov/CSA/2025/250507.pdf
The Google Threat Intelligence Group (GTIG) has uncovered a new malware named LOSTKEYS, linked to the Russian government-supported threat group COLDRIVER. This malware is capable of stealing files from a predefined list of extensions and directories while also transmitting system details and running processes back to the attacker. It spreads through a multi-step infection process that begins with a deceptive website featuring a fake CAPTCHA, specifically targeting high-profile individuals such as current and former advisors to Western governments and militaries, journalists, think tanks, and NGOs. https://cloud.google.com/blog/topics/threat-intelligence/coldriver-steal-documents-western-targets-ngos
Damn, am I actually agreeing with the Electronic Frontier Foundation? The Florida bill requiring social media companies to provide encryption backdoors for law enforcement access to user accounts and private messages has failed to pass. And yes, the EFF is correct; it is “dangerous and dumb.” Is that a flying pig? https://techcrunch.com/2025/05/09/florida-bill-requiring-encryption-backdoors-for-social-media-accounts-has-failed/
And now we have “Shrimp Fraud”. https://www.wect.com/2025/05/07/new-investigation-alleges-shrimp-fraud-wilmington-area/
Cool Job
Director of Fraud Operations - ID.me. https://job-boards.greenhouse.io/idme/jobs/6506848003
Cool Tool
IPInfo is offering its Lite version for free. https://ipinfo.io/lite
Python tool to search usernames across over 600 social media sites. https://github.com/p1ngul1n0/blackbird
DFIR
Huntress asks, “Do tigers really change their stripes?” Probably not. https://www.huntress.com/blog/do-tigers-really-change-their-stripes
Irrelevant
Ghost students are posing as real students in California community colleges, creating a growing problem for institutions. These bots are designed to steal millions of dollars in financial aid, and their numbers have more than doubled since the pandemic, with over $10 million stolen in 2024 alone. Colleges are struggling to detect and eliminate these fake students. The college system has implemented verification tools, yet the perpetrators are becoming increasingly sophisticated as AI technology advances, making it a challenging and agonizing problem for colleges to combat. https://www.sfgate.com/bayarea/article/ghost-students-creating-problem-calif-colleges-20311708.php
Sign Off
Some audiences are better than others, and I always enjoy speaking at Association of Certified Fraud Examiners (ACFE) events. I covered the after-lunch slot at the Lehigh Valley ACFE chapter this week, and the group remained engaged, well, at least awake. Thanks for hosting me, and welcome new subscribers to the newsletter!
See you all next Tuesday!
Thanks, Matt
Published every Tuesday, Threats Without Borders offers original commentary and educational pieces related to cybercrime investigations and information security topics. We also summarize and comment on news articles concerning active threat intelligence for the financial industry. The newsletter interests everyone tasked with cybersecurity or involved in preventing or investigating technology-enabled fraud, theft, or money laundering.
Legal: I am not compensated by any entity for writing this newsletter. Obviously, anything written in this space is my own nonsensical opinions and doesn’t represent the official viewpoint of my employer or any associated organization. Blame me, not them.