Threats Without Borders - Issue 238
Cybercrime Investigation Newsletter, week ending June 8, 2025
During a recent meeting with a group of financial crime investigators, I shared my view that malicious insiders are more prevalent in banks and credit unions than security professionals typically acknowledge. I further asserted that our efforts to tackle this issue are inadequate horrible, both in prevention and investigation.
Many financial institutions are facing significant staff shortages, particularly in frontline customer service roles, such as teller positions. As a result, we tend to hire anyone who applies. The qualifications often boil down to questions like: Do you have a felony conviction? Have we previously fired you? Is your face covered with tattoos? If you can pass those, you're hired.
Then what happens? After just a week of training, these individuals gain access to sensitive customer accounts with very limited controls or monitoring in place. We hand them the keys to the kingdom before most of us even know their names.
Do we have a program in place to monitor new employees for unusual access patterns or for circumventing defined procedures? Are we using software tools to leverage user behavior analytics to provide visibility into the activities of new hires?
Even better, let’s start with the essentials: what does our background investigation process entail?
I plan to elaborate on this in my future writings; it may evolve into a conference talk. As security practitioners, we must improve in this area, as there is no doubt that attackers are strategically inserting assets into our organizations to steal business and customer data.
But for now, ask your HR department how they vet potential new hires. Ask your IT security staff if you have any data loss prevention tools in place. And ask your security department how they investigate suspicious incidents involving employees.
The News…
The FTC's 2024 data book reveals a staggering 129% rise in credit reporting system fraud from 2022 to 2024. This fraud utilizes synthetic identities, credit washing, and various other misleading tactics. Criminals are taking advantage of technological weaknesses, insufficient oversight, and the accessibility of social media to exploit the credit reporting system, leading to financial losses for lenders and damaging legitimate consumers. By the way, if you're not following David Maimon on his social media, go do it now. https://www.forbes.com/sites/davidmaimon/2025/06/02/the-hidden-fraud-machine-targeting-the-credit-reporting-system/
An employee at North Shore University Hospital's Sleep Disorders Center in New York has been charged with installing hidden cameras in restrooms to secretly record staff and patients. Between July 2023 and April 2024, the man placed the cameras in disguised smoke detectors, capturing footage of "hundreds of individuals," including a child. The hospital classified the incident as a HIPAA violation that affected 13,332 individuals and informed all patients who visited the facility during the alleged recording timeframe. He attached the fake cameras to the wall with Velcro, installing them at the start of his shift and removing them before leaving. https://www.healthcareinfosecurity.com/da-sleep-center-worker-installed-secret-camera-in-bathrooms-a-28611
International law enforcement dismantled AVCheck, a service utilized by cybercriminals to evaluate malware detection. Authorities seized the malware testing service, and connected its administrators to the crypting services Cryptor.biz and Crypt.guru. Investigators made purchases from the seized websites, confirming their involvement in cybercrime and linking them to ransomware groups targeting American entities. https://www.bleepingcomputer.com/news/security/police-takes-down-avcheck-antivirus-site-used-by-cybercriminals/
Wait, are we talking about Cozy Spider Bear or Speckled Spider Trout? Microsoft has announced a strategic collaboration with the Global Anti-Scam Alliance to combat cybercrime, aiming to bring clarity to the naming of threat actors and enhance efforts to fight cybercrime. https://www.microsoft.com/en-us/security/blog/2025/06/02/announcing-a-new-strategic-collaboration-to-bring-clarity-to-threat-actor-naming/
The Google Threat Intelligence Group exposes a financially motivated threat group that specializes in voice phishing campaigns to compromise organizations' Salesforce instances for data theft and extortion. The attackers use social engineering tactics to trick employees into authorizing malicious connected apps, granting them access to sensitive information. https://cloud.google.com/blog/topics/threat-intelligence/voice-phishing-data-extortion/
The U.S. Attorney’s Office seized 145 domains and cryptocurrency funds linked to the BidenCash marketplace, which facilitated the sale of stolen credit cards and personal information. The marketplace, operational since March 2022, generated over $17 million in revenue and had 117,000 customers. https://www.justice.gov/usao-edva/pr/us-government-seizes-approximately-145-criminal-marketplace-domains
This post explores how Business Email Compromise (BEC) attackers establish and sustain persistence within victims' email accounts. A prevalent method is the implementation of email forwarding rules, enabling attackers to discreetly observe communications and extract sensitive information without arousing immediate suspicion. https://osintteam.blog/bec-persistence-and-data-exfiltration-techniques-67e5926812a0
The CEO of Power Mobility Doctor Rx has been found guilty of orchestrating a fraud scheme that defrauded Medicare and other federal healthcare benefit programs out of more than $1 billion. This scheme involved targeting hundreds of thousands of Medicare recipients by creating false doctor orders for non-medically necessary items. Pharmacies, suppliers of durable medical equipment, and marketers received illegal bribes and kickbacks for these orders. https://www.justice.gov/opa/pr/ceo-health-care-software-company-convicted-1b-fraud-conspiracy
Cool Tool
Kali Linux + ChatGPT = KaliGPT https://chatgpt.com/g/g-uRhIB5ire-kali-gpt
What is your IP address telling the services you connect with? https://ipcheck.ing/
Cool Job
Security Awareness and Training Analyst - State Farm Insurance. https://jobs.statefarm.com/main/jobs/41431
Feedback: matt[@]threatswithoutborders[.]com
DFIR
Sumuri discusses how to image Macs with Apple silicon chips. https://sumuri.com/imaging-apple-silicon-macs-a-modern-forensic-guide/
This one hurts
The budget deficit is too damn high. Things need to be cut. Spending needs to be controlled.
But damn it hurts when it’s something you care about. I’m devastated to learn about the recent personnel reductions at the NW3C due to federal budget cuts.
The best training I’ve ever had. Seriously, not just in quality but in impact. That initial BDRA – Basic Data Recovery Analysis class (yes, I took it so long ago it was still called BDRA) made me fall in love with digital forensics and propelled me into advanced training, certificates, and a graduate degree. Honestly, I wouldn't be where I am today without the early training I received from the National White Collar Crime Center.
In fact, I always imagined working there as an instructor someday. I can’t think of a better way to give back than to share my knowledge through their programs.
The organization is still operational, and I hope it will continue to deliver high-quality courses taught by excellent, top-notch instructors. Please support them. Demand their classes in your area so they can justify their existence to those who control the purse strings. If you have benefited from NW3C training, please send a note to your congressman and senator to let them know. https://www.nw3c.org/UI/Index.html
Irrelevant
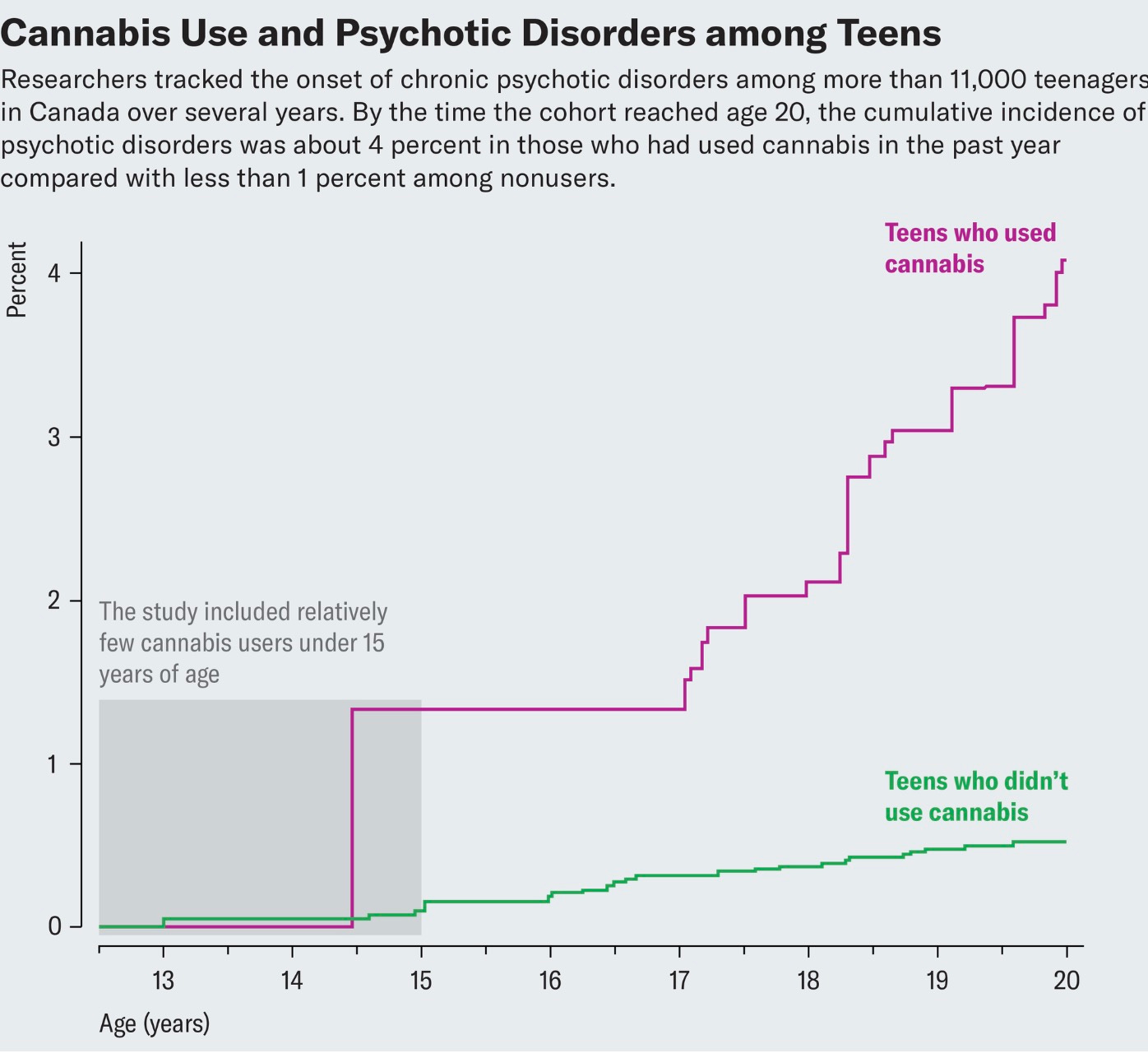
Hey kids, let’s stick with Busch Light stolen from the old man’s garage fridge.
https://www.scientificamerican.com/article/the-link-between-cannabis-and-psychosis-in-teens-is-real/
Sign Off
I met with lawyers last week; in fact, it was a whole room full. I spoke to them about cyber-fraud, and they asked polite questions in return. It was a cordial affair, so I believe I’m back in good graces with the law lobby. Maybe.
Thank you for taking a few minutes to read another issue of the newsletter. See you next week.
Matt
Published every Tuesday, Threats Without Borders offers original commentary and educational pieces related to cybercrime investigations and information security topics. We also summarize and comment on news articles concerning active threat intelligence for the financial industry. The newsletter interests everyone tasked with cybersecurity or involved in preventing or investigating technology-enabled fraud, theft, or money laundering.
Legal: I am not compensated by any entity for writing this newsletter. Obviously, anything written in this space is my own nonsensical opinions and doesn’t represent the official viewpoint of my employer or any associated organization. Blame me, not them.