Threats Without Borders - Issue 245
Cybercrime Investigation Newsletter, Week ending July 27, 2025
The Privacy Policy and Terms of Use for any web resource or app are valuable sources for additional information when conducting your investigation.
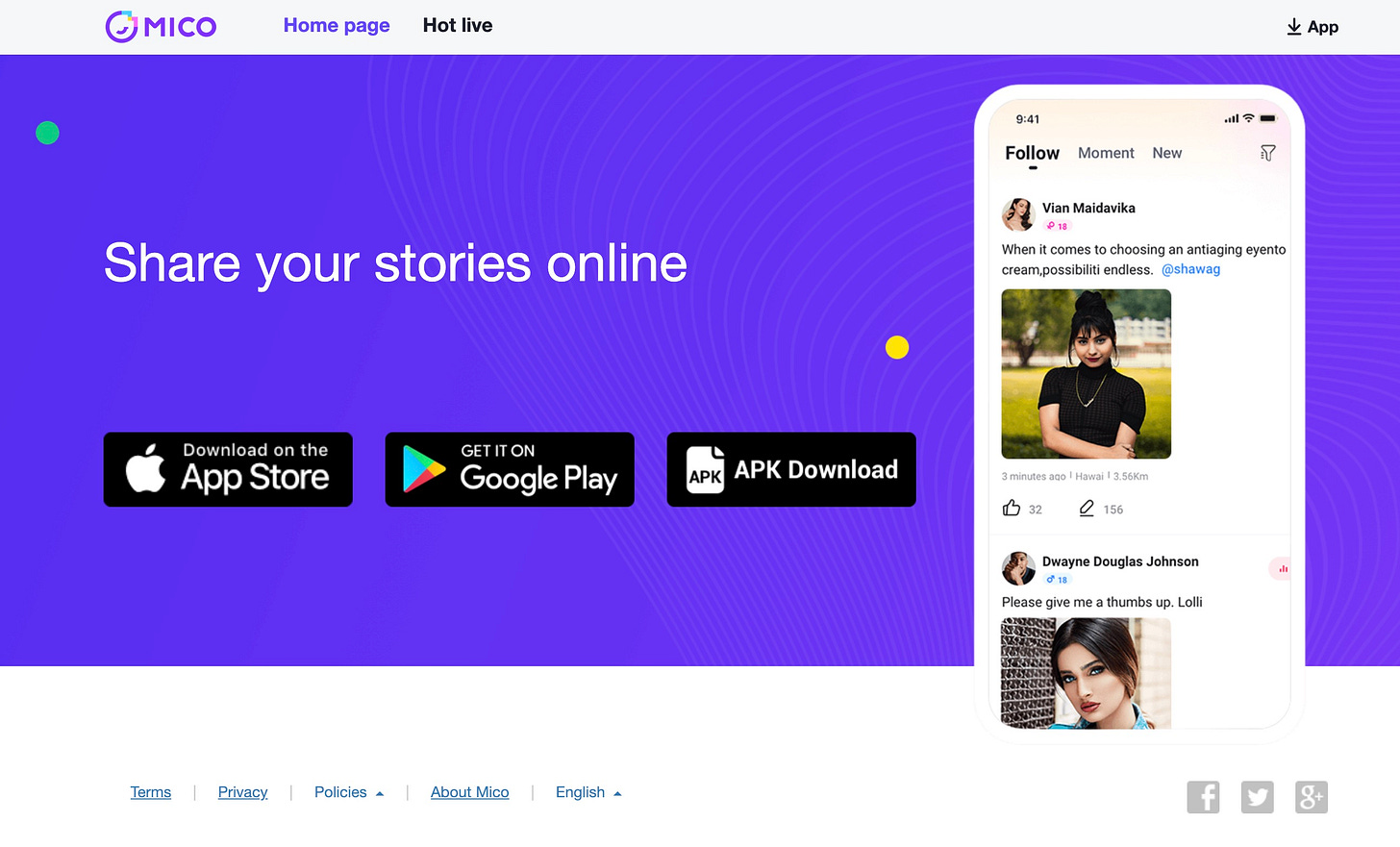
I recently assisted an investigator with an exploitation case linked to the streaming and chat app MICO. He couldn't find contact details for the organization and asked if I had any knowledge of it.
He had checked the SEARCH ISP database, and it didn’t have any records for the app.
The information provided on the app page in the Google Play store was sparse.
The publisher’s website offered less and directed you back to the Google Play or Apple App Store.
The “About Mico” page didn’t offer much information about the company. There was a “Sexual Abuse Support” page under the Policies tab, but it simply directed users to report suspected abuse through the app or to the National Center for Missing and Exploited Children.
So we went to my favorite resources - the Terms of Use and the Privacy Policy.
These were also written generically and appeared to be templated. All terms of service will list which country has jurisdiction over disputes and this one was no different.
Hong Kong. Now, we know that it will take a Mutual Legal Assistance Treaty (MLAT) obtained through the U.S. Department of Justice to obtain any information about the suspected user of the application.
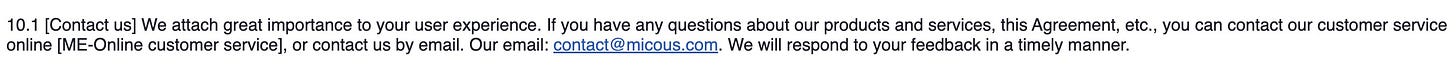
And we also found the contact email, which wasn’t published anywhere else on the website.
The Privacy Policy is also a great resource for finding information about the data the organization collects from users while they use the application. This is a sample from Snapchat’s privacy policy:
That's a goldmine of information during a digital investigation. Seriously, they are collecting the motion and movements of your device during use!
If a company claims they are collecting data, trust them. When requesting a court order, ask for detailed information. These companies prefer not to disclose more about their activities than necessary, so if their privacy policy states they are collecting certain data, it means that data is definitely being gathered and stored. If you have legal grounds to obtain it, get it!
Organizations based in the United States or Europe typically have clear Terms of Use and robust Privacy Policies, as they are required by legislation such as the GDPR and the California Consumer Privacy Act (CCPA).
It’s often best to just start your investigation with these declarations when dealing with a web service or mobile device application. Not only will you gather investigative leads, but you will also gather language for search warrants and court orders.
Will they hold the cardholders accountable
You lost your card? Well, I’m looking at the video and I see the person enter the PIN. How did they know your PIN? Silence. “Ahhh, ummm, I guess I had it written on the back of the card”.
How many times have you had that conversation?
A system vulnerability led to a $17 million ATM scam in New York City, where scammers used debit cards intended for participants in a summer youth job program to withdraw large sums from ATMs across the city. The scam, which took place from July 11 to 13, enabled scammers to access payments of up to $40,000 per ATM. Reports indicate that some program employees sold their cards to hackers for $1000. The attack appears to have been coordinated and facilitated through social media.
The News…
Kudos to investigators with Synchony Bank who initiated this investigation and pushed it to law enforcement. Eight people have been arrested in a bank fraud investigation targeting elderly individuals, resulting in the recovery of over $8 million in stolen funds. The suspects, who worked at a bank in Maryland and lived in various states, allegedly transferred money into accounts and disbursed it among themselves or made purchases. The investigation began after investigators with Synchrony examined a $250,000 transfer into a newly created account. https://www.abcactionnews.com/news/region-polk/8-people-arrested-over-8m-recovered-in-bank-fraud-investigation-targeting-elderly-sheriff-grady-judd
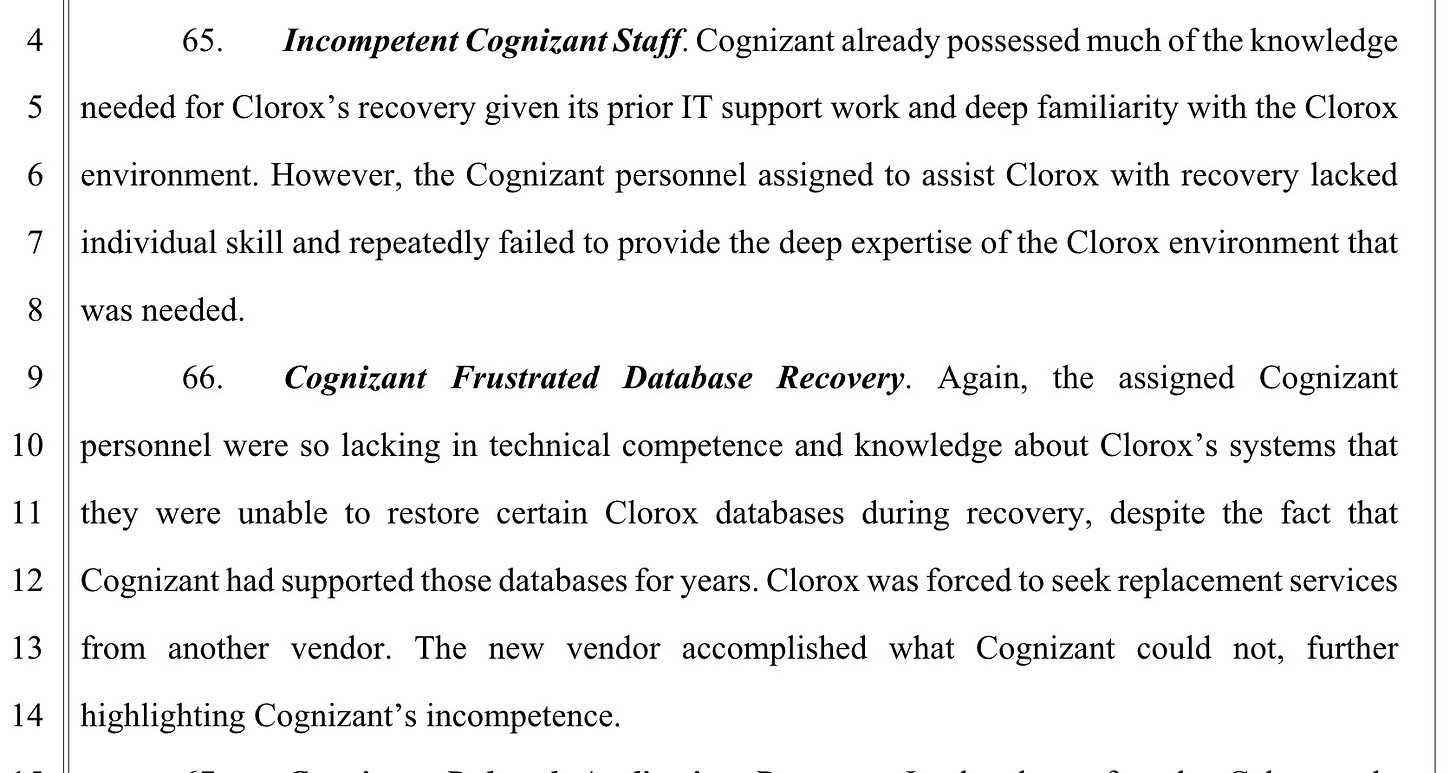
Clorox is suing IT services provider Cognizant for gross negligence, alleging that they enabled a massive cyberattack in August 2023 by resetting an employee's password without proper verification. The problem was that the actual employee wasn’t the one making the request. Ouch. The lawsuit alleges that Cognizant's failure to follow security protocols enabled hackers to gain unauthorized access to Clorox's IT network, resulting in widespread disruption and financial losses. Clorox is seeking $380 million in damages, citing breach of contract, gross negligence, and intentional misrepresentation of staff training.
The lawsuit is required reading. Obviously, there are three sides to this story - Clorox, Cognizant, and the truth. But the lawsuit presents a pretty damning account against Cognizant. https://www.documentcloud.org/documents/26025981-07-22-redacted-clorox-complaint/
Recall is a service built into the Microsoft Windows OS, it saves full-screen screenshots every few seconds and stores them in a local database, which hopefully stays local. Brave claims to block this feature by default so your web browsing isn’t documented with screenshots that can potentially be exploited if your computer is compromised. https://brave.com/privacy-updates/35-block-recall/
This complex phishing attack involved spoofing a Google email through a DKIM Replay Attack. The attacker initially received a genuine email from Google, extracted its content, and then sent it from an Outlook account, making it appear as if it originated from a legitimate Google no-reply address. The email was convincing enough to cause concern, claiming a subpoena had been issued to extract the victim's Google Account data. The attacker also used Google Sites to simulate an official Google support page, increasing the deception. The success of the attack was due in part to passing SPF, DKIM, and DMARC authentication checks, which made detection difficult. Later analysis and reproduction of the attack revealed that the attacker used a Google OAuth app to insert malicious content into the email. Google addressed the vulnerability by restricting app name options, preventing similar attacks in the future. https://easydmarc.com/blog/google-spoofed-via-dkim-replay-attack-a-technical-breakdown/
Allianze Insurance confirms the “majority” of their customers have been affected by a data breach. https://techcrunch.com/2025/07/26/allianz-life-says-majority-of-customers-personal-data-stolen-in-cyberattack/
The United States Secret Service in the Memphis, TN area, along with local and state law enforcement partners, conducted a regional skimmer sweep. The group inspected over 3,300 ATMs, gas pumps, and point-of-sale terminals, recovering four skimming devices. They claim to have prevented an estimated $4.2 million in losses. I question that number, but excellent work nontheless. https://www.secretservice.gov/newsroom/releases/2025/07/law-enforcement-agencies-conduct-ebt-fraud-and-card-skimming-outreach
Here’s a business idea for someone: teach art dealers how to complete SARs. Several U.S. senators have proposed the “Art Market Integrity Act" to bring the U.S. art market into line with the stricter anti-money laundering (AML) regulations of Europe and the UK. The bipartisan legislation would require art market businesses operating in the US to comply with measures to prevent money laundering and the financing of terrorism. Key requirements would apply to dealers, collectors, galleries, auction houses, advisers, and museums, with exemptions for artists selling their own works and businesses with limited transactions. https://www.theartnewspaper.com/2025/07/25/anti-money-laundering-legislation-us-senate-proposal
Email: matt @ threatswithoutborders.com
Blue Alert Network
The National Blue Alert Network supports the use and integration of Blue Alert plans throughout the United States in order to rapidly disseminate information to law enforcement agencies, the media and the public to aid in the apprehension of violent criminals who have killed, or seriously injured an officer in the line of duty. Blue Alerts can also be issued when a suspect poses an imminent and credible threat to law enforcement, or when an officer is missing in the line of duty.
https://cops.usdoj.gov/bluealert
Cool Job
Director of Security, LA Clippers https://www.nba.com/clippers/company/careers/openpositionlaclippers?gh_jid=4585893006&gh_src=ljzj9y1f6us
Director of Security, Baltimore Orioles https://www.teamworkonline.com/baseball-jobs/orioles-jobs/baltimore-orioles-jobs/director-security-2124873
Cool Tool
BugPic - Insect and Bug identifier. Take a pic and get an identification. https://apps.apple.com/us/app/insect-bug-identifier-bugpic/id6744052801
Reverse image search tool - https://www.labnol.org/reverse
Irrelevant
Which is more expensive: daycare for a child or daycare for a pet? Both. https://marginalrevolution.com/marginalrevolution/2025/07/the-rising-cost-of-child-and-pet-day-care.html
Sign Off
I was reviewing an older journal, and on a page dated April 21, 2021, I found a scribbled side note that reads, “Post/Talk idea- Law enforcement leadership fail: Why do so many terrible cops end up in leadership positions?”
There is no additional notation to explain what happened that day or why I was triggered to consider the topic. The rest of the page contains some notes about Windows LNK files.
I’m out of the game now, but the problem persists. Or so I’m told.
Thank you for reading another issue. Have a great week, and I’ll see you next Tuesday.
Matt
Published every Tuesday, Threats Without Borders offers original commentary and educational pieces related to cybercrime investigations and information security topics. We also summarize and comment on news articles concerning active threat intelligence for the financial industry. The newsletter interests everyone tasked with cybersecurity or involved in preventing or investigating technology-enabled fraud, theft, or money laundering.
Legal: I am not compensated by any entity for writing this newsletter. Obviously, anything written in this space is my own nonsensical opinions and doesn’t represent the official viewpoint of my employer or any associated organization. Blame me, not them.
cybercrime cybersecurity osint aml fraud investigations