Threats Without Borders - Issue 256
Cybersecurity Investigation Newsletter, week ending October 12, 2025
A recent UC San Diego study claims that cybersecurity training programs don’t prevent employees from falling for phishing scams. But the study’s scope and the way it’s being interpreted deserve a closer look.
In fact, the title of the article is horribly misleading, not only of the research but also of the security awareness effort as a whole.
The research only examined one narrow form of phishing training: short, automated “embedded” lessons delivered immediately after a simulated phishing email. These are the one-click, pop-up modules that many employees close in seconds. The study found that this specific style of training had little measurable impact, which isn’t surprising.
However, this does not represent the full range of cybersecurity awareness programs in practice today.
Effective security awareness training goes far beyond canned email exercises. It includes:
Live instruction, discussion, and feedback
Scenario-based learning
Regular reinforcement through multiple channels (email, video, posters, team briefings)
Real-world context addressing phone, text, and social engineering threats
Training fails when it’s treated as a checkbox exercise. But when it’s relevant, engaging, and repeated, and when it’s supported by technical controls like MFA and domain protection, it significantly improves vigilance and reporting behavior.
The UCSD findings highlight the weakness of passive micro-trainings, not the futility of cybersecurity education as a whole.
https://today.ucsd.edu/story/cybersecurity-training-programs-dont-prevent-employees-from-falling-for-phishing-scams
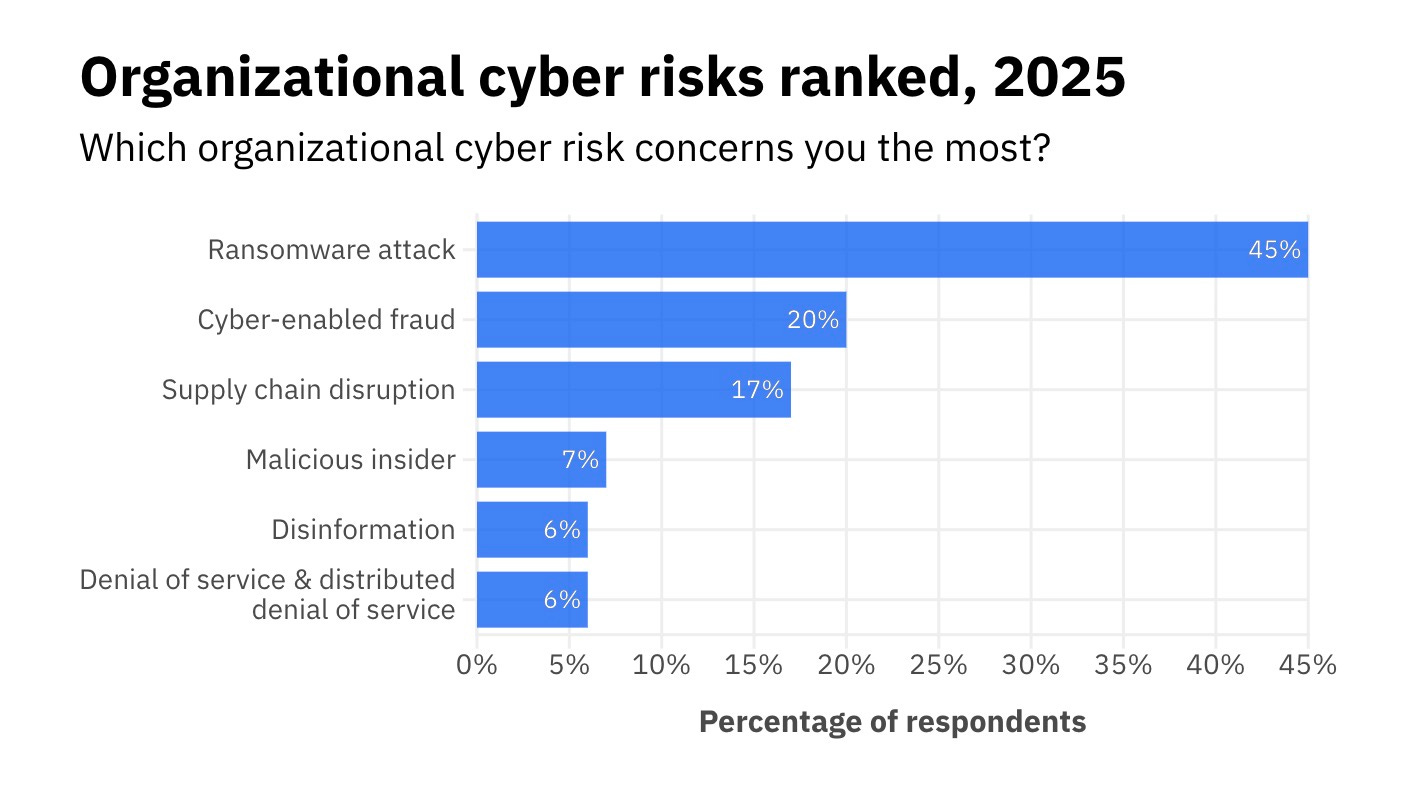
Source: World Economic Forum
The News…
I’ll hold the Pirate Jokes. Microsoft Threat Intelligence has identified a financially motivated threat actor conducting “payroll pirate” attacks by compromising employee accounts to redirect salary payments to attacker-controlled accounts. The attacks mainly target US universities and use social engineering tactics, often through phishing emails, to bypass weak or missing multifactor authentication (MFA) protections. Once inside, the attacker modifies HR profiles in platforms like Workday, deletes warning emails to hide changes, and establishes persistence by adding their own MFA devices. In this blog post, Microsoft offers detection methods, hunting queries, and mitigation guidance, emphasizing the importance of adopting phishing-resistant MFA to prevent such attacks. https://www.microsoft.com/en-us/security/blog/2025/10/09/investigating-targeted-payroll-pirate-attacks-affecting-us-universities/
This group, calling itself “the coalition of cyber investigators,” discusses the current issues within the field of Open-Source Intelligence (OSINT), highlighting problems such as platform bias, insecure tools, and a lack of standards. They call for real change, including certification programs, tool security audits, and the adoption of digital forensics standards to improve the reliability and ethical practices of OSINT. https://coalitioncyber.com/osints-broken-state
Moving quickly, the FBI and French authorities seized the BreachForums site hours before the Scattered Spider group was set to leak data stolen from Salesforce. Despite the takedown, the group claims the site’s Tor version remains active and their plans to expose data from 39 high-profile Salesforce customers are unaffected. Salesforce has refused to negotiate or pay any ransom, linking the extortion to a past security incident involving a third-party app called Salesloft. The FBI has previously shut down BreachForums multiple times, arresting its administrator in 2023. https://therecord.media/breachforums-fbi-france-takedown-banner-scattered-spider-salesforce-leak
Anthropic’s own study found that as few as 250 malicious documents can create a backdoor vulnerability in large language models, regardless of size or training data volume. This challenges the assumption that attackers need a percentage of training data, highlighting the practicality of data-poisoning attacks. https://www.anthropic.com/research/small-samples-poison
Cisco Talos has confirmed that ransomware operators are using Velociraptor, an open-source digital forensics and incident response (DFIR) tool that was not previously definitively linked to ransomware incidents. https://blog.talosintelligence.com/velociraptor-leveraged-in-ransomware-attacks/
Impact Solutions is a new phishing toolkit that makes advanced malware delivery easier for threat actors with little technical skill. It allows attackers to create weaponized files like convincing .lnk shortcuts, HTML pages, and SVG images that look legitimate, using social engineering to bypass user awareness and security filters. The toolkit also features evasion techniques such as icon spoofing, UAC bypasses, and anti-sandbox checks, which make it more difficult for traditional security solutions to detect. https://abnormal.ai/blog/impact-solutions-democratizing-malware-delivery
FinCEN clarified common misunderstandings about Suspicious Activity Reports (SARS) with a FAQ document. For a government publication, it’s unexpectedly educational. https://www.fincen.gov/system/files/2025-10/SAR-FAQs-October-2025.pdf
Cool Tool
BGP View (Border Gateway Protocol) describes itself as “BGPView is a web-based project that provides both, a web-browsing tool and an API that lets you gather information about the current state and structure of the internet, including ASNs, IP addresses, IXs, BGP Downstream & Upstream Peers, and much more.” And it’s currently free. https://bgpview.io/
Cool Job
Fraud Support Analyst - Jack Henry. https://careers.jackhenry.com/job/springfield/fraud-support-analyst-credit-debit-card/42859/87065682496
Feedback
“Matt, you’re right about the Instagram app listening. I was at a party, and at the appetizer table, a guy asked me if I had ever tried Namako. What? Never heard of it. He told me it’s sea cucumber and a delicacy in Japan. Later that night, I get Instagram posts about preparing sea cucumber. Nope…that’s not a coincidence.” - TK
Send feedback to matt at threatswithoutborders.com
Irrelevant
Apple Graveyard - all the products Apple created and eventually killed. https://lost-apple-gems.lovable.app/
Training
The National Association of Bunco Investigators (NABI) will hold its annual training convention November 5-6 in Paramus, NJ. They are still accepting registrations.
BUNCO is the term used for confidence scams perpetrated by transnational organized crime groups, AKA Travelers. You know, the people who spray your driveway used motor oil and trick teenage cashiers out of 100 bucks.
https://www.nabihq.org/training-and-conferences.html
Sign Off
Thanks for reading another issue. I lost a bunch of subscribers last week. I guess they didn’t like hearing my voice. Or they are marketers who sell our private information to social media companies. I truly appreciate those of you who stick with me week after week.
I hope you can somehow download the PNG file below. I enjoy making these and sharing them. Feel free to share it with others in your community. I’ll start including more in the newsletter if it works.
Matt
Published every Tuesday, Threats Without Borders offers original commentary and educational pieces related to cybercrime investigations and information security topics. We also summarize and comment on news articles concerning active threat intelligence for the financial industry. The newsletter interests everyone tasked with cybersecurity or involved in preventing or investigating technology-enabled fraud, theft, or money laundering.
Legal: I am not compensated by any entity for writing this newsletter. Obviously, anything written in this space is my own nonsensical opinions and doesn’t represent the official viewpoint of my employer or any associated organization. Blame me, not them.