Threats Without Borders - Issue 259
Cybercrime Investigation Newsletter, week ending November 2, 2025
I recently listened to a cybersecurity personality repeatedly conflate the Internet with the World Wide Web. Although these terms are often used interchangeably, they actually refer to two different concepts. I’m sure the speaker knows the technical difference, and the confusion was (somewhat) harmless, but it’s still important to understand the distinction.
To be cliché, the Internet is a network of networks. Think of it as a massive highway system connecting billions of computers worldwide. It is the actual network infrastructure composed of cables, wireless signals, routers, and servers that enables devices to communicate with each other.
Here’s the key point: the Internet is the delivery system. It moves data from one place to another, but it doesn’t care what that data is or what it looks like.
The World Wide Web, on the other hand, is one specific service that uses the Internet to function. It’s the collection of websites, web pages, images, videos, and links that you access through a browser like Chrome, Safari, or Firefox.
The Internet can be compared to a highway system, with roads, bridges, and infrastructure that facilitate traffic flow from one location to another. The World Wide Web is just one type of vehicle that uses these highways; it’s a way to navigate the Internet, but not the only method available.
What Else Uses the Internet:
Email travels over the Internet but doesn’t use the Web (though you might access email through a web browser)
Streaming services like Netflix and Spotify send video and music over the Internet using their own systems
Online gaming connects players through the Internet
Video calls on Zoom or FaceTime use the Internet to transmit audio and video
File sharing and cloud storage move files across the Internet
Text messaging apps send messages using Internet connections
All of these services depend on the Internet to function, but they’re separate from the World Wide Web.
Understanding the difference helps you realize that the Internet is much bigger than just browsing websites. When your Internet connection goes down, you lose access to everything: websites, email, streaming, gaming, and more. However, if there were a problem specifically with a web server or segment of networks, you might still be able to send emails or make video calls.
It also helps when discussing technology issues. Saying “the Internet is down” means the entire network connection is unavailable. Saying “I can’t access a website” is a more specific problem with the Web portion of your Internet service.
For investigative and cybersecurity professionals, using accurate terminology is crucial not only for technical correctness but also for effective investigations and clear communication. Saying they’re “investigating activity on the Web” refers specifically to website traffic, browsers, and web-based apps. In contrast, “investigating Internet activity” covers a wider scope, including email exchanges, file sharing, gaming platforms, peer-to-peer networks, and any other services that utilize Internet infrastructure.
This distinction is also necessary when preparing search warrants, subpoenas, and court documents. Vague terms like “Internet records” may not stand up legally or could lead to retrieving the wrong data from service providers. Asking for “web browsing history” differs significantly from requesting “Internet connection logs” or “email server records.” Investigators familiar with these terms can more accurately target the digital evidence they need, locate it, and ensure legal compliance. Using precise terminology in testimony also boosts credibility and aids judges and juries in understanding complex technical details. Conversely, mixing up these terms can cause miscommunication with technical teams, incomplete evidence collection, and jeopardize cases.
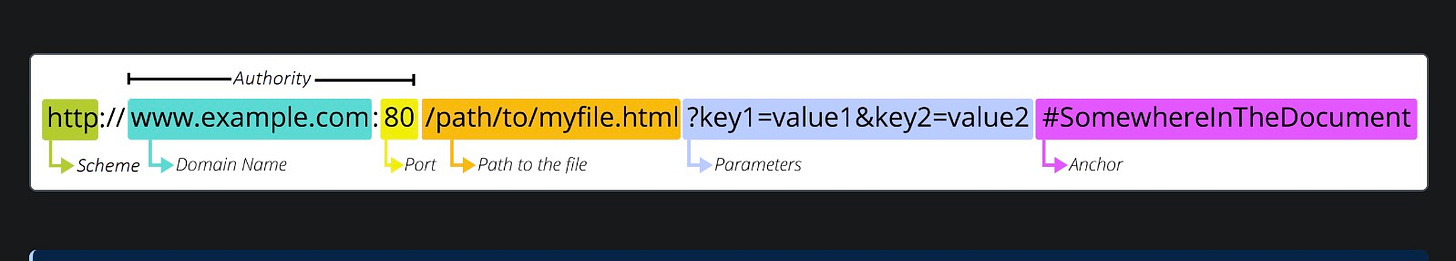
Investigators should understand the URL, or Uniform Resource Locator, which enables a resource to be identified by a web location. We have previously discussed this on Tw/oB.
When you enter something like “https://www.example.com/page.html” into your browser, you’re using a URL (Uniform Resource Locator). URLs are a Web-specific invention, not a general Internet tool. They are crafted as Web artifacts, intended solely for navigating web resources through browsers.
Different Internet services use their own addressing systems suited to their specific functions and protocols. For example, email uses addresses like “user@domain.com" with SMTP, IMAP, and POP3, while gaming platforms rely on proprietary connection methods. Video calling apps connect users without URLs, and file sharing often employs FTP addresses that resemble URLs but work differently. Each service has distinct ways to locate and connect to resources, with URLs being exclusive to the World Wide Web. When investigators review URLs in browser history or server logs, they focus on Web activity specifically, not the broader range of Internet activities a person might perform.
One of the best resources for understanding URLs in the Mozilla Developer pages. https://developer.mozilla.org/en-US/docs/Learn_web_development/Howto/Web_mechanics/What_is_a_URL
The News…
This BBC article examines cybercrime in India and how many rural Indians find it easier and more profitable to run scams on the rest of the world than to do traditional work like farming. https://www.theguardian.com/technology/2025/oct/30/scamming-became-the-new-farming-inside-india-cybercrime-villages
Not a good week for the University of Pennsylvania, as someone hacked their email service and sent offensive emails to, well, just about everyone ever associated with the school. https://therecord.media/upenn-hacker-email-affirmative
Malwarebytes explains how scammers use personal data from your digital footprint, both what you actively share online and what is passively collected, to create highly personalized scams. It details methods like data scraping, breaches, and social engineering, and provides real-world examples of scams that exploit this information. https://www.malwarebytes.com/blog/inside-malwarebytes/2025/10/how-scammers-use-your-data-to-create-personalized-tricks-that-work
Browser wars - researchers with Brave identified a vulnerability in the Perplexity Comet browser. https://brave.com/blog/unseeable-prompt-injections/
Push Security highlights a new phishing attack that is delivered through a LinkedIn direct message. https://pushsecurity.com/blog/new-phishing-campaign-identified-targeting-linkedin-users/
Twenty members of a transnational organized crime ring were indicted, and 15 individuals were arrested during **Operation Silver Shores**. This operation targeted a transnational fraud scheme that defrauded over 372 elderly victims of more than $30 million by pretending to be attorneys and government officials. The scam involved false legal claims related to timeshares and complex financial transactions designed to launder the stolen money. The FBI, IRS Criminal Investigation, and local law enforcement led the investigation, which resulted in charges of wire fraud and conspiracy to commit money laundering. https://www.justice.gov/usao-edca/pr/arrests-aimed-dismantling-transnational-fraud-organization-operation-silver-shores
Employees are scamming their employers by submitted AI-generated receipts for reimbursement. https://www.foxbusiness.com/lifestyle/workers-using-ai-scam-employers-phony-expense-receipts-report
Google introduced Recovery Contacts, a new feature that allows users to designate trusted individuals to assist with account recovery if they are locked out. This provides an additional option for account recovery when other methods are unavailable. https://blog.google/technology/safety-security/recovery-contacts-verify-google-account/
Feedback: matt @ threatswithoutborders.com
Cool Tool
This is one of the coolest tools I’ve discovered in a long time. Enter your PTO time, and it calculates how to maximize your time off by combining weekends and holidays. It extended my PTO to a total of 56 days off in 2026. https://holiday-optimizer.com/
Tor Browser 15.0 has been released. https://blog.torproject.org/new-release-tor-browser-150/
Cool Job
Deputy CISO, Commonwealth of Pennsylvania. https://www.governmentjobs.com/careers/pabureau/jobs/5121572/deputy-chief-information-security-officer
DFIR
Someone sneaked into a Cellebrite law enforcement-only webcast and shared the information in the GrapheneOS forums. The leaker, known as rogueFed, revealed that Cellebrite can extract data from most Google Pixel phones, except those running GrapheneOS, a more secure alternative OS. The information was obtained from a Cellebrite briefing and includes details on Pixel 6, 7, 8, and 9 models.
Credit to 404 Media for breaking the story, but their article is paywalled. Here is the actual forum post, which is the source of the story. https://discuss.grapheneos.org/d/27698-new-cellebrite-capability-obtained-in-teams-meeting/7
Irrelevant
Take your damn Vitamin D supplement. https://ijmpr.in/article/the-role-of-vitamin-d-supplementation-in-the-prevention-of-acute-respiratory-infections-a-double-blind-randomized-controlled-trial-1327/
Listening to others is hard. You should learn how to do it. https://togetherlondon.com/insights/active-listening-swiss-army-knife
Training
There is still time to register for the IAFCI - Carolina’s Chapter 2-day financial crime and fraud training event in Myrtle Beach, SC. https://www.iafci.org/Public/Public/Training_Events/2025/IAFCI_Carolinas_Chapter_Seminar_November_19__21.aspx
Sign Off
Next week will be issue 260. 260/12=5.
Come back to see how it goes. Or doesn’t.
Have a great week.
Matt
“YOU LEARN NOTHING FROM LIFE IF YOU THINK YOU’RE RIGHT ALL THE TIME.” - probably why I’m such a low achiever.
Published every Tuesday, Threats Without Borders offers original commentary and educational pieces related to cybercrime investigations and information security topics. We also summarize and comment on news articles concerning active threat intelligence for the financial industry. The newsletter interests everyone tasked with cybersecurity or involved in preventing or investigating technology-enabled fraud, theft, or money laundering.
Legal: I am not compensated by any entity for writing this newsletter. Obviously, anything written in this space is my own nonsensical opinions and doesn’t represent the official viewpoint of my employer or any associated organization. Blame me, not them.
cybercrime cybersecurity financial fraud investigations aml osint