Threats Without Borders - Issue 265
Cybercrime Investigation Newsletter, week ending December 14, 2025
Last week, I began a series about the use of cryptocurrency in cybercrime and concluded with an introduction to tools that hinder blockchain investigators. As often occurs, another publication published a timely article that supports exactly what I was explaining and likely did so more effectively. But first, let’s examine two tools employed by those trying to obscure their cryptocurrency activities.
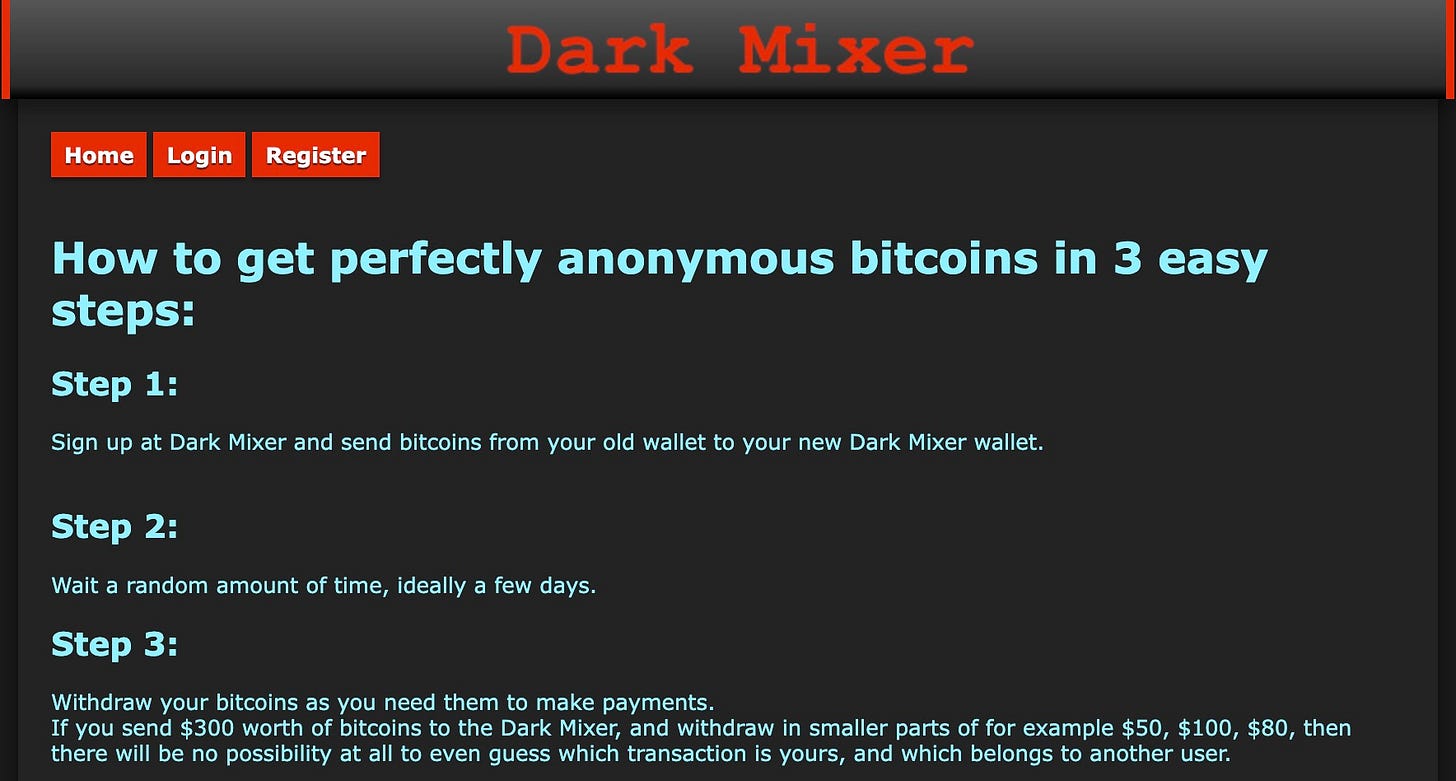
A cryptocurrency mixer is typically a decentralized protocol, meaning no single company or operator controls it. Instead, multiple users participate in one large shared transaction. Each participant deposits cryptocurrency simultaneously, and the pool combines all the funds. The user then receives the same amount back from a different output, making it impossible to link the incoming wallet to the outgoing one.
Conversely, a tumbler is usually a centralized service operated by a single entity. Criminals send their funds to the tumbler’s wallet, which holds the funds, breaks them into smaller parts, delays them, and then gradually returns the funds using new addresses. Tumblers act as intermediaries, while mixers resemble a group activity that anonymizes all participants.
In both cases, their purpose is to erase the clear investigative trail showing the source and destination of illicit cryptocurrency. The aim isn’t to halt the money but to obscure the record.
Criminals send illegal funds into these systems to hide their original source. After mixing or tumbling, they receive “clean” funds that seem to come from a random place on the blockchain, rather than a criminal wallet.
Fortunately for investigators, these services often leave prominent digital footprints. A typical wallet shows predictable activity—money occasionally goes in and out. But a mixer or tumbler wallet resembles chaos: it receives numerous deposits from unrelated users and makes many rapid payments in various amounts. It also charges a small fee, which provides another clue.
Using blockchain analytics tools, investigators can identify these patterns and connect wallets to mixing or tumbling services. These tools cluster addresses, spot unusual money flows, and flag transactions that seem artificially engineered.
Even when criminals use these services, they eventually want to convert their funds into real-world value. This is where investigations often succeed.
A key weak point is the off-ramp. Eventually, mixed funds land in a cryptocurrency exchange, where they’re converted into dollars, euros, or stablecoins. Regulated exchanges collect customer information through Know Your Customer rules. Tracking the funds from the mixer to an exchange allows investigators to subpoena the platform and reveal the true identity behind the wallet.
Statistical de-mixing also helps, where analysis of timing, transfer amounts, delays, and routing patterns can link outputs back to inputs. Although mixers try to break direct links, advanced analysis can often reconstruct likely connections with high confidence.
While mixers and tumblers make tracking individual transactions more difficult, they don’t make the money invisible. Instead, they create a chaotic pattern—one that investigators can recognize. By analyzing these patterns and focusing on how criminals eventually use their “cleaned” coins, investigators can trace the wallet back to a real person. Cryptocurrency isn’t an escape hatch for criminals; it’s a trail they inevitably leave behind.
Yohan Yun published an article in Cointelegraph just in time for this week’s issue, profiling cryptocurrency security experts who act as “onchain detectives”. These investigators trace stolen funds across blockchain networks, often working under pseudonyms like ZachXBT and 0xSaiyanGod. They utilize open-source tools and informal networks to track hackers and draining operations. Operating in “war rooms” formed immediately after breaches, they combine blockchain forensics with human intelligence to follow the money trail before it vanishes through mixers and bridges.
The article is titled “Meet the Onchain Crypto Detectives Fighting Crime Better than Cops.”
Yes, they do.
https://cointelegraph.com/magazine/meet-crypto-sleuths-fighting-crime-better-than-the-cops/
The News…
FinCEN issued a report revealing that companies paid over $2.1 billion to ransomware groups across 4,194 incidents from January 2022 to December 2024, nearly matching the total for the previous nine years combined. Ransom payments peaked in 2023 at $1.1 billion—a 77% increase from 2022—with a median of $174,000, and then fell to $734 million in 2024 following law enforcement actions against major gangs such as ALPHV and LockBit. ALPHV/BlackCat was the most profitable, earning nearly $400 million, with LockBit at $252.4 million and Black Basta at $137.7 million. The top 10 ransomware variants accounted for $1.5 billion in payments. The 267 identified gangs mainly targeted financial, manufacturing, and healthcare sectors, with 97% of payments in Bitcoin, laundered through unregulated crypto exchanges. The report says the quiet part out loud, despite efforts like the Counter Ransomware Task Force, the threat remains high as most gangs operate from Russia and other countries that do not extradite their citizens, complicating enforcement. https://www.fincen.gov/system/files/2025-12/FTA-Ransomware.pdf
Malwarebytes describes a sophisticated phishing operation that uses free Cloudflare Pages hosting to create fake banking and insurance login portals, which steal not just passwords but also security question answers to bypass multi-factor authentication. The attackers combine these free hosting services with compromised legitimate websites as redirectors (making phishing links appear more trustworthy) and send all stolen credentials directly to Telegram bots for immediate use, avoiding traditional command-and-control servers. https://www.malwarebytes.com/blog/news/2025/12/how-phishers-hide-banking-scams-behind-free-cloudflare-pages
Are you prepared for the RAMpocalypse? https://taoofmac.com/space/links/2025/12/05/1330
The Financial Action Task Force released new guidance and best practices to enhance efforts in recovering criminal assets. The guidance, covering topics from financial investigations to victim compensation, aims to disrupt criminal organizations by removing their financial motivation. https://www.fatf-gafi.org/en/publications/Methodsandtrends/asset-recovery-guidance-best-practices-2025.html
A data breach at 700Credit is expected to affect 5.6 million people, exposing names, addresses, dates of birth, and Social Security numbers. The breach, yet to be attributed, involved data collected from dealers between May and October 2025. https://techcrunch.com/2025/12/12/data-breach-at-credit-check-giant-700credit-affects-at-least-5-6-million/
FalconFeeds is quickly becoming one of my favorite threat intelligence blogs. In this article, they describe how cybercrime localization has developed into a sophisticated, high-precision strategy where threat actors craft phishing and social engineering campaigns tailored to regional cultures, languages, and time zones, greatly increasing their chances of success. By utilizing AI and large language models, cybercriminals can achieve linguistic accuracy and cultural relevance, helping them bypass conventional security measures and build human trust. This trend is fueled by clear ROI, with financially driven groups and state-sponsored entities deploying localized tactics to target key sectors, manipulate regional financial systems, and exploit holidays and political events. https://falconfeeds.io/blogs/cybercrime-localization-regional-targeting-evolution
Be cautious when purchasing a subscription to an AI service. Cybercriminals are increasingly exploiting AI platforms such as ChatGPT, Perplexity, and Gemini by offering premium account access at heavily discounted prices on the Dark Web. These prices range from $6.99 to $59.99 for shared or upgraded accounts. They often use stolen credit cards or credentials from infostealer logs, frequently sold on Underground markets, to acquire and resell these accounts for profit, with some offering a one-year Perplexity AI Pro subscription for as little as $9.99. The danger is not limited to financial loss; compromised AI accounts can also be exploited for phishing, malware creation, and data theft, particularly when linked with corporate systems. https://www.esentire.com/blog/hackers-are-celebrating-holidays-big-this-year
Google is shutting down its “Dark Web Report” service. https://support.google.com/websearch/answer/16767242
Send mail
matt[@]threatswithoutborders[.]com
What could go wrong
A privacy advocate, after 11 years fighting the FBI over National Security Letters demanding customer data from internet service providers, has introduced Phreeli. This new mobile carrier aims to provide anonymous cellular service accessible to all. Operating as an MVNO on T-Mobile’s infrastructure, Phreeli only requires a ZIP code for sign-up—the minimum personal info needed legally for taxes—while employing an advanced encryption called “Double-Blind Armadillo”“ based on zero-knowledge proofs to verify payments without linking credit cards or identities to phone numbers. Users can pay via cryptocurrency or credit cards and select their privacy level, with options like eSIMs or Tor-hosted sites for maximum anonymity.
This is fine. Everything is fine.
https://www.wired.com/story/new-anonymous-phone-carrier-sign-up-with-nothing-but-a-zip-code/
Cool Tools
Ethereum storage analyzer https://slotscan.info/
The Beta version of ParrotSec 7 has been released. https://www.parrotsec.org/blog/2025-12-09-parrot-7.0-beta-release-notes/
Cool Job
Director of Fraud Escalations - Q2. https://q2ebanking.wd5.myworkdayjobs.com/en-US/Q2/job/Austin-TX/Director--Product-Security_REQ-11071
Intelligence Analysts - MLB. https://www.mlb.com/careers/opportunities?gh_jid=7362278
Irrelevant
Cloudflare released its “2025 Year in Review” report. It’s always one of the best of the yearly reports, and this one is no exception. No, it’s exceptionally well done. https://radar.cloudflare.com/year-in-review/2025
Sign Off
I spent time in Nashville last week. First time. I saw a show at the Grand Ole Opry, visited the Country Music Hall of Fame, saw the Predators beat up the St. Louis Blues, ate some BBQ, and had authentic Nashville hot chicken. But what’s up with all the homeless people? Or “unsheltered”, as I was told they should be called. And the kids on every street corner banging on buckets? At first, it was impressive, but after a while, like 15 minutes, it just became noise pollution. Otherwise, it was a fantastic trip, and I plan to return sooner rather than later.
Thanks for reading another issue. See you all next Tuesday!
Matt
“START EVEN IF YOU DON’T KNOW HOW.”
Published every Tuesday for over five years, Threats Without Borders offers original commentary and educational pieces related to cybercrime investigations and information security topics. We also summarize and comment on news articles concerning active threat intelligence for the financial industry. The newsletter interests everyone tasked with cybersecurity or involved in preventing or investigating technology-enabled fraud, theft, or money laundering.
Legal: I am not compensated by any entity for writing this newsletter. Obviously, anything written in this space is my own nonsensical opinions and doesn’t represent the official viewpoint of my employer or any associated organization. Blame me, not them.
cybersecurity cyficrime AML osint financial crime fraud investigations