Threats Without Borders - Issue 271
Cybersecurity Investigation Newsletter, week ending January 25, 2026
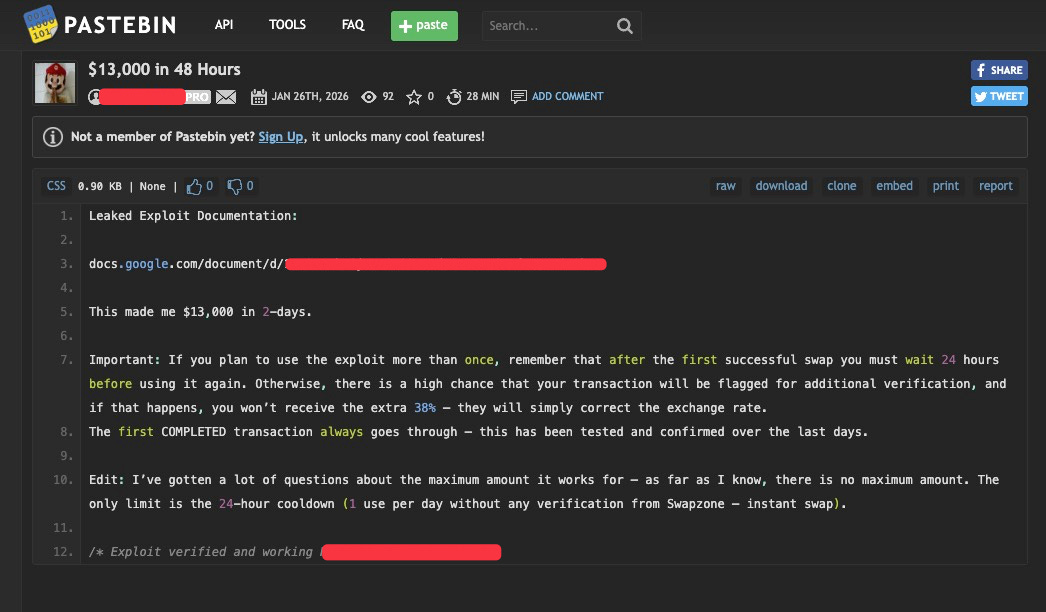
I found myself chasing some information on a Paste site this week.
A pastebin is a web service that allows users to store and share plain text via unique URLs. Originally designed as collaboration tools for developers and IT professionals, these platforms let anyone post code snippets, log files, configuration data, or notes without creating an account. Popular examples include Pastebin.com, Ghostbin, and JustPaste.it.
There are dozens of legitimate use cases for these sites, from sharing error logs for troubleshooting, collaborating on code across teams, and distributing configuration files. However, paste bins have become valuable infrastructure for threat actors precisely because of their legitimate popularity.
Several factors make them attractive for criminal activity:
Blending with legitimate traffic: Security tools and web filters rarely block paste sites since they’re widely used by legitimate users. Malicious communications to these platforms can hide in plain sight among normal developer traffic.
Low-friction anonymity: Most paste sites require no authentication or allow throwaway accounts. Content moderation is often minimal, allowing malicious pastes to remain accessible for extended periods.
Zero infrastructure costs: By leveraging existing platforms, attackers avoid maintaining their own servers or domains, reducing both operational costs and the risk of takedowns. The paste site handles hosting, uptime, and global accessibility.
The bad guys regularly upload stolen credentials, database dumps, and personal data (doxing) as pastes. These serve various purposes: showing evidence of a breach, promoting data sales, or blackmailing. Ransomware groups have turned paste sites into public boards, posting ransom demands, doxing threats, and attack updates before sharing links on underground forums or directly with targets victims.
In more advanced scenarios, malware often uses a two-phase process where the initial infection involves only a small loader. This loader connects to a pastebin URL to access encoded content, which it then decodes and runs as the main payload. Similarly, malware configuration details like command-and-control links, encryption keys, and operational settings are stored as text and fetched at runtime. This approach gives attackers considerable flexibility, enabling them to update payloads or change configurations just by editing a paste. Such modifications are applied instantly across all infected systems without needing to redeploy the malware binaries.
Beyond direct malware operations, paste sites facilitate information sharing among threat actors. Exploit code, attack tutorials, and operational guides are posted as pastes with links shared through encrypted messaging apps, forums, or social media. Buyers and sellers of stolen data exchange samples, or “teasers,” via disposable paste links, avoiding more traceable communication methods.
For cybercrime investigators, paste bins represent both a challenge and an intelligence goldmine. Here’s how investigators can leverage these platforms:
Indicator of Compromise extraction: Parse pastes for IOC’s including IP addresses, domain names, file hashes, email addresses, and cryptocurrency wallets. These can feed into threat intelligence platforms or be cross-referenced with ongoing investigations.
Breach notification: When investigating a suspected data breach, search paste sites for your organization’s information. Stolen data often appears publicly before victims are aware of the compromise.
Timeline reconstruction: Paste timestamps can help establish attack timelines. When malware samples are discovered, investigators can check if associated paste bin URLs still contain payloads or configurations, potentially revealing the attack sequence.
Attribution clues: Pastes may contain unintentional artifacts--usernames, language preferences, coding styles, timezone indicators in timestamps--that help link activities to known threat actors or narrow suspect pools.
Investigators should be aware that attackers can delete or alter content at any moment, and many pastes have automatic expiration features. Capture screenshots or archive suspicious pastes right away. Also, paste sites are operated worldwide, each with different policies on data retention, user privacy, and law enforcement cooperation. Since they are unlikely to respond to search warrants for data, seize what information you can whenever possible.
https://github.com/lorien/awesome-pastebins
Call back
In the last issue, we covered Synthetic Identity Fraud. Mr. Lenderman advises that the Federal Reserve has the most extensive documentation on this topic.
The News…
A TD Bank employee has pled guilty to federal charges related to bribery and money laundering. The bank insider facilitated a money laundering scheme, accepting bribes to open accounts for shell companies and issue debit cards. He then shipped the cards to Colombia, where they were used for over 120,000 ATM withdrawals. https://www.justice.gov/usao-nj/pr/td-bank-insider-pleads-guilty-facilitating-colombian-atm-money-laundering-scheme
The Tallahassee, Florida, government was targeted by a scam, resulting in a loss of one million dollars to the fraudsters. Ouch. The city police department states they are investigating the incident, but a watchdog group argues that the Chief of Police can not be impartial, as their superior is involved. Where is the FBI? They ask. https://www.tallahassee.com/story/news/local/2026/01/20/watchdog-group-calls-for-fbi-fdle-to-investigate-city-cybercrime/88267720007/
The Jamf Threat Labs has observed the North Korea-linked “Contagious Interview” campaign, where attackers use Microsoft Visual Studio Code to deliver malware. They lure victims by cloning fake Git repositories, often disguised as job tasks, from sites like GitHub or GitLab. When the repository is trusted in VS Code, a file automatically runs commands that download and execute a JavaScript backdoor, which communicates with control servers every five seconds. This allows hackers to take control, gather system details, and run commands on victims' computers. The campaign shows that DPRK-linked hackers continue to adapt to legitimate developer tools. Researchers advise developers to verify repositories before trusting them in VS Code and avoid running commands like “npm install” on untrusted projects. https://www.jamf.com/blog/threat-actors-expand-abuse-of-visual-studio-code/
Eight Amtrak employees have pleaded guilty to conspiracy to commit health care fraud. Between January 2019 and June 2022, they accepted kickbacks from healthcare providers in exchange for fraudulent billing of services, resulting in over $11 million in fraudulent claims. https://www.justice.gov/usao-nj/pr/amtrak-employees-admit-participating-11-million-health-care-fraud-scheme-0
Okta Threat Intelligence discusses the evolution of sophisticated phishing kits specifically designed for voice-based social engineering (vishing) attacks. These kits, available as-a-service, allow attackers to control what victims see in their browsers in real-time during phone calls, creating synchronized experiences that make fraudulent requests appear legitimate. The attackers typically impersonate IT support, guide victims to phishing sites, capture credentials, and then manipulate the browser display to match their verbal instructions for bypassing MFA challenges like push notifications or one-time passcodes. https://www.okta.com/blog/threat-intelligence/phishing-kits-adapt-to-the-script-of-callers/
Is this irony
Number one rule of OSINT - don’t end up on a database while doing OSINT
Cool Job
Manager of Investigations - Mattel (Hot Wheels) https://jobs.mattel.com/en/job/el-segundo/manager-of-investigations/2015/90587703168
Cool Tools
People finder. https://ufind.name/
Search for just about any artifact you have. https://intelx.io/
Conference Updates
Layer 8 Conference (OSINT focused) - Boston, June 5-6, 2026. https://layer8conference.com/
Keystone KConnection (IAFCI Delaware Valley and Pittsburgh Metro Chapters) - State College, PA, May 18-20, 2026. https://keystonekonnection.com/
Irrelevant
This guy is pretty smart for only being 34. https://elliot.my/im-34-heres-34-things-i-wish-i-knew-at-21/
Sign Off
I've gotten through the storm. It's all snow here, which makes it a pain to move, but it's not as damaging as ice. Sending my goodwill, hope, and prayers to those in the Southeast who were hit the hardest.
Thank you for taking the time to read this issue, and I’ll see you next Tuesday.
Email: matt (at) threatswithoutborders.com
Matt
“LIFE IS EASIER WHEN YOU LEARN TO ACCEPT THE APOLOGY YOU NEVER GOT.”
Published every Tuesday, Threats Without Borders offers original commentary and educational pieces related to cybercrime investigations and information security topics. We also summarize and comment on news articles concerning active threat intelligence for the financial industry. The newsletter interests everyone tasked with cybersecurity or involved in preventing or investigating technology-enabled fraud, theft, or money laundering.
Legal: I am not compensated by any entity for writing this newsletter. Obviously, anything written in this space is my own nonsensical opinions and doesn’t represent the official viewpoint of my employer or any associated organization. Blame me, not them.
cybercrime cybersecurity financial crime fraud investigations aml cyficrime