Threats Without Borders - Issue 272
Cybercrime Investigation Newsletter, week ending February 1, 2026
When so many organizations hide their reports behind information-collection barriers that require you to give away your professional contact information and then endure relentless sales calls… TRM Labs continues to share its knowledge freely and openly. And they don’t publish a vanilla product that simply rehashes common industry knowledge.
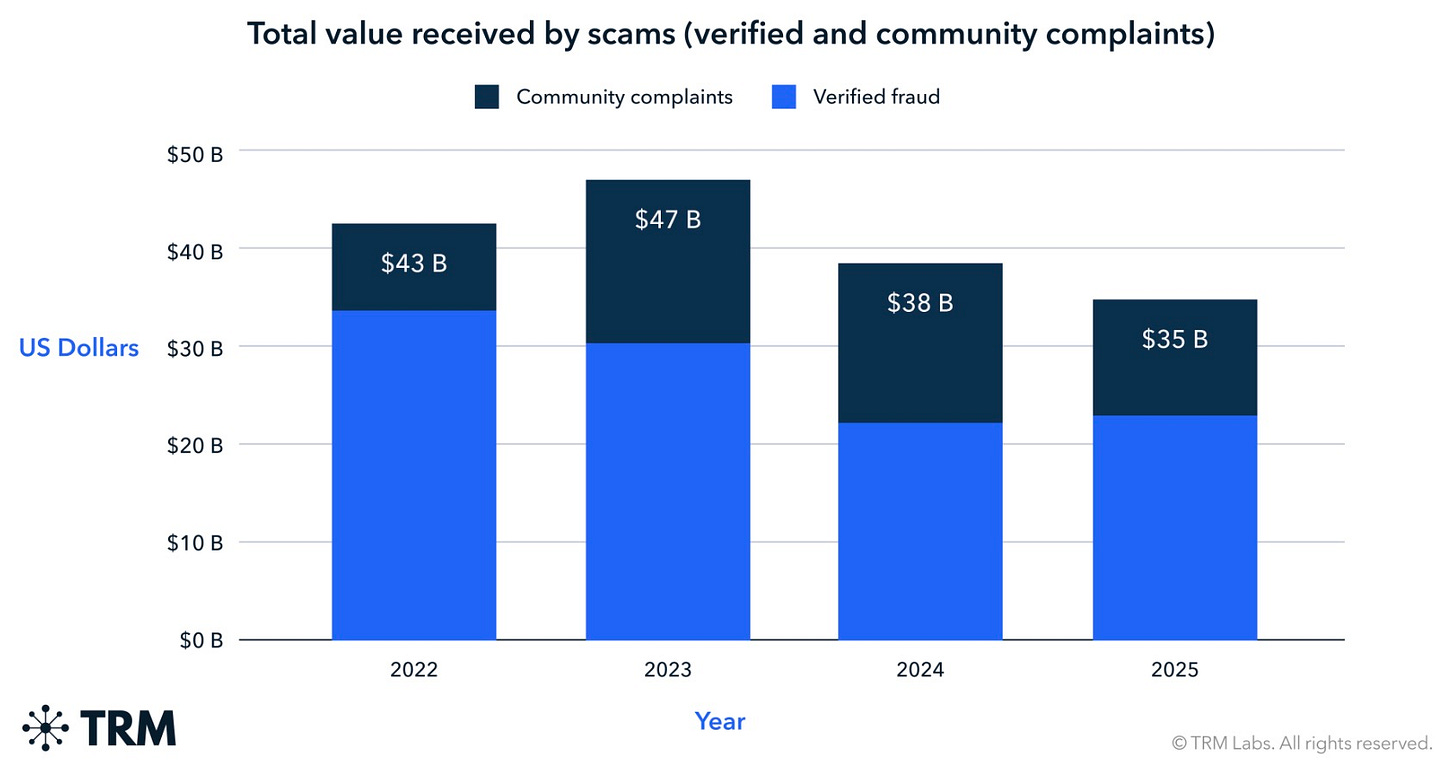
TRM Labs' 2026 Crypto Crime Report shows illicit crypto flows hit a record $158 billion in 2025, ending a multi-year decline. This rise was mainly due to three factors: new sanctions designations, better detection tools, and large hacks like the $1.46 billion Bybit breach. Despite the overall increase, illicit activity as a share of total crypto activity fell to 1.2%, suggesting that legitimate crypto use expanded faster than criminal activity.
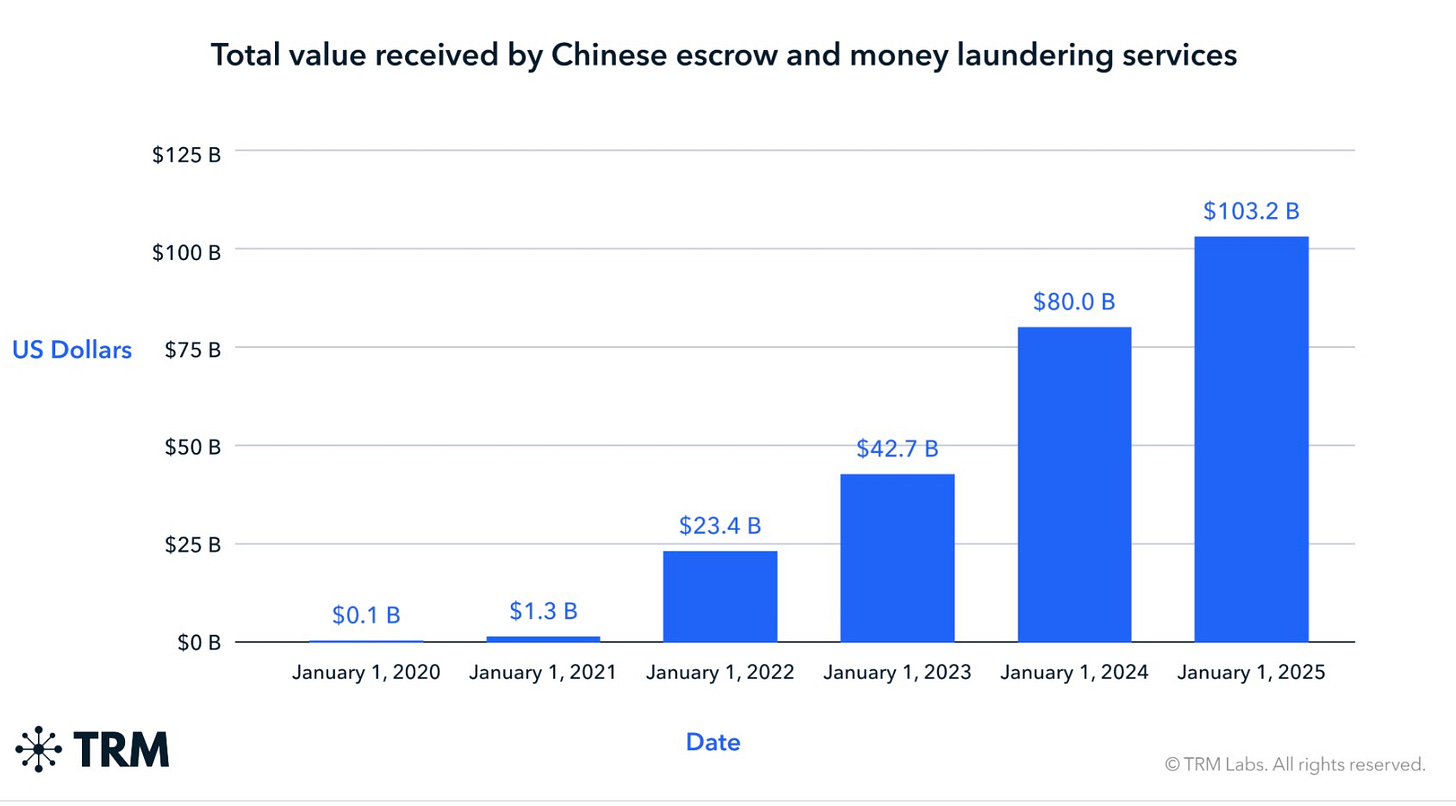
The report highlights how state-aligned actors are institutionalizing crypto infrastructure for sanctions evasion, how ransomware and scam operations have become more sophisticated and organized, and how Chinese money-laundering networks have evolved into massive settlement layers that process over $103 billion.
The findings highlight that crypto crime has become a core part of both legitimate and illicit financial systems, emphasizing the need for improved enforcement coordination and specialized crypto-investigation tools.
This is a great report and well worth your time to read and digest.
https://www.trmlabs.com/reports-and-whitepapers/2026-crypto-crime-report
Because like security, duh.
I debated how to title this: “Because we suck at security” or “This is why you respond to every alarm”.
A federal grand jury indicted 31 people for stealing millions from ATMs using Ploutus malware. The gang surveilled ATMs, opened them to test alarms, and replaced hard drives or connected thumb drives with malware to dispense cash.
Two key points: 1) The attackers forced open the ATMs and then retreated to safety. If police arrived, they fled the scene. They continued the attack if there was no police response. 2) Ploutus malware has been active since 2013. Yes, thirteen years ago. While it has evolved, technology and protections exist to prevent it.
And it isn’t a stealthy attack. It’s a physical intrusion into the machine. It’s noisy and makes a mess. Here is an article the Google Threat Intelligence Team published in 2017 that explains the effort required to attack an ATM with Ploutus.
These types of attacks are preventable. Of course, we suck at security.
Anyways, kudos to the law enforcement teams that coordinated to shut this group down.
Presenter Pro-Tip
When speaking to industry peers about a relevant topic, avoid wasting time explaining "how bad it is”. They already know. Being on the front lines, they recognize the problem; that's why they're listening to you.
Unless you’re speaking to beginners, a non-peer group, or presenting entirely new material based on your own research, avoid starting with five slides filled with numbers and statistics about the problem’s prevalence. By the time you finish outlining the industry landscape, most of your audience’s attention will have drifted. And honestly, it’s insulting.
I sat through a presentation this week in which the speaker spent the first ten minutes highlighting well-known fraud statistics from regularly cited sources like the Internet Crime Complaint Center. You're speaking to an audience of financial crime investigators. It’s ugly out there—we get it. That’s why we’re willing to give you thirty minutes of our time. Tell us something we don’t know!
The News…
$2.5 million has been secured for a new cybercrime training facility in Madisonville, Kentucky. The facility, the largest police training academy in the state, will focus on cybercrime investigations and expand training to include computers, drones, and vehicle data systems. The investment aims to address the growing threat of cybercrime and position Madisonville as a leader in prevention and response. Kudos to them. Hopefully, someone there will invite me for a visit! https://spectrumnews1.com/ky/louisville/news/2026/01/26/cyber-crime-training-center
Scammers are using a legitimate Microsoft email address (no-reply-powerbi@microsoft.com) associated with Power BI. They send fraudulent emails claiming fake $399 charges and direct victims to call a phone number, where they are instructed to install remote access software. This scam exploits Power BI’s feature that allows external email addresses to subscribe to reports, making the emails appear trustworthy without suspicious links or attachments that could trigger spam filters. Microsoft has temporarily disabled the scorecard email subscription feature while working on a permanent fix. This incident underscores how scammers can misuse legitimate business platforms to enhance the credibility of their social engineering schemes. https://arstechnica.com/information-technology/2026/01/theres-a-rash-of-scam-spam-coming-from-a-real-microsoft-address/
Research by Chainalysis reveals Chinese-language money laundering groups laundered an estimated $16.1 billion in illicit cryptocurrency daily in 2025, totaling $82 billion annually. These groups utilize guarantee platforms, money mules, and Black U services to launder funds, including those stolen in pig butchering financial grooming scams. https://www.chainalysis.com/blog/2026-crypto-money-laundering/
The Google Threat Analysis Group (TAG) released its 4Q2025 Threat Report. https://blog.google/threat-analysis-group/tag-bulletin-q4-2025/
The FBI has seized the domains for the RAMP cybercrime forums. https://www.bleepingcomputer.com/news/security/fbi-seizes-ramp-cybercrime-forum-used-by-ransomware-gangs/
Trend Micro examines the maturation of criminal AI in 2025, revealing a shift from experimentation to industrialization. The criminal AI ecosystem has consolidated around established services offering “jailbreak-as-a-service” that exploit commercial AI models rather than building independent systems. While AI-generated malware remains limited by practical constraints, deepfake technology has become alarmingly accessible and weaponized across multiple fronts,from “nudifying” apps enabling image-based abuse to sophisticated corporate infiltration schemes where North Korean operatives use AI-enhanced identities to gain employment at tech companies, and banking fraud targeting KYC verification systems. https://www.trendmicro.com/vinfo/us/security/news/cybercrime-and-digital-threats/the-state-of-criminal-ai
The government seized over $400 million in assets from Larry Dean Harmon, operator of the darknet mixing service Helix. Harmon, who processed over $300 million in cryptocurrency transactions for Helix, pleaded guilty to money laundering and was sentenced to 36 months in prison. https://www.justice.gov/opa/pr/government-forfeits-over-400m-assets-tied-helix-darknet-cryptocurrency-mixer
Reader Mail
Matt, thanks for the piece on paste sites. It brought back memories of an insider threat (corporate espionage) case I had about ten years ago, in which the employee used a paste site to send information to his handler. Using a prepaid cell phone, he’d paste his info into the same note every Tuesday. The handler would then go to the same note to retrieve the information. This was way before encrypted chat apps. We could never build a link to those he was communicating with. - RussK
Send email: matt (at) threatswithoutborders.com
Cool Job
Fraud Program Manager - Vervent. https://recruiting.paylocity.com/recruiting/jobs/Details/3821568/Vervent-Inc/Fraud-Program-Manager
Cool Tool
Search for people, Fast. https://www.fastpeoplesearch.com/
If Wal-Mart is closed, you know the weather is bad. Someone created a Wal-Mart store status dashboard. https://www.arcgis.com/apps/dashboards/4e573c79e1224081805165d25b4f33c7
Someone I like
There are not many people writing or podcasting in the Cyber/Fraud/AML space who I like enough to recommend in the newsletter. Check that, there are very few people that I like.
But I like Sarah Beth Felix! She writes a great LinkedIn newsletter focused on BSA and AML, titled “Dirty Money”. Give her a follow.
https://www.linkedin.com/pulse/problem-streamline-act-sarah-beth-felix-uxt7e/
Irrelevant
Sunshine and Salmon. This study reveals that positive levels of Vitamin D and Omega-3 have a greater effect on a person than antidepressants. https://blog.ncase.me/on-depression/
Closing
I wake up every morning at 5am. The other day, at 5 am, I started a pot of coffee. It was 12 degrees outside, and I heard the fire siren go off. I thought, ‘I’m glad I don’t need to leave this warm house and hot coffee to handle that.’ But, of course, someone did have to go out and handle it. And in my area, these selfless souls don’t get paid for it.
My deepest thanks to all the local emergency services volunteers who leave the comfort and safety of their homes, and a freshly poured cup of hot coffee, every day to help others. Thank you!
Matt
Published every Tuesday, Threats Without Borders offers original commentary and educational pieces related to cybercrime investigations and information security topics. We also summarize and comment on news articles concerning active threat intelligence for the financial industry. The newsletter interests everyone tasked with cybersecurity or involved in preventing or investigating technology-enabled fraud, theft, or money laundering.
Legal: I am not compensated by any entity for writing this newsletter. Obviously, anything written in this space is my own nonsensical opinions and doesn’t represent the official viewpoint of my employer or any associated organization. Blame me, not them.
aml cybercrime cybersecurity financial fraud investigation osint cyficrime