Threats Without Borders Newsletter - Issue 260
Talking about cybersecurity and cybercrime investigations for five years
What have you done for 260 consecutive weeks? Five years.
I’ve published an issue of Threats Without Borders every week for 260 weeks. Consecutive weeks. So, not only is this the five-year anniversary of the newsletter, but it also marks a milestone: I haven’t missed a Tuesday in five years.
I’ve gone back and forth on how much space to give this and decided, not much. However, I would like to take a moment to humble brag. Over that time, a lot of cool kids, the industry darlings, the good lookers, have tried to start a newsletter. And they work for a while. But none have been able to sustain consistently over a year, let alone five.
I recognize that consistency doesn’t always mean quality. Wells Fargo has been operating for 173 years. However, for a free newsletter, this one, written by a goofy kid with a cantankerous personality and poor hearing, does quite well.
What’s next?
I don’t know. I’ve met all my goals. But for now, as long as you all keep reading, I’ll keep writing. How about sharing the newsletter with a friend or two, and we’ll see if we can hit the six-year mark?
Over the past few weeks, my organization has been actively targeted by email bomb attacks. While the attack isn’t new, it’s something we haven’t seen in a while, and this time it’s back with a twist... social engineering through a direct message.
The attack begins when a victim’s email inbox suddenly fills with hundreds or even thousands of messages — sometimes from random websites or newsletters the person never signed up for. It happens so fast that the mailbox becomes almost impossible to use.
While the victim is busy trying to deal with the flood of messages, the attacker reaches out by phone, Microsoft Teams, or another chat platform, pretending to be from the company’s IT help desk. In our case, it’s been Teams.
If the target accepts the DM request, the attack moves to the next stage.
The fake “help desk” representative is convincing. They might say something like, “We see your email account is overloaded, and we’re helping fix it.” They may offer to help clear the inbox, verify your identity, or reset your login. In some cases, they’ll ask you to share your password or approve a security code to “confirm your account.” Unfortunately, once you do, they’ve got what they need to break in.
The goal of this scam is to steal account credentials or multi-factor authentication (MFA) codes. Once attackers have access, they can read emails, join internal chats, and even impersonate employees to request money transfers or sensitive information. With many companies, this type of attack is used to start a business email compromise (BEC) scam or other forms of fraud.
You can think of it as a two-part con:
1. The email bomb causes chaos and distraction.
2. The fake help desk support takes advantage of that chaos to trick the target into handing over access.
Wait, Matt! How do they send Teams messages from outside of your organization? Yeah, that’s what we also questioned. But like everything with Microsoft, if there is a will, there is a way. And in this case, it doesn’t take much will as the functionality is set by default, and while you disable the feature, it creates all sorts of downstream problems. For instance, not allowing Teams to interact with external accounts prohibits your employees from accepting invites to external meetings.
The best defense against this type of attack is awareness. Educate your employees about the attack. We created and distributed an internal memo detailing the mechanics of the attack and how employees should respond when they recognize the red flags.
Our email security system eventually detects the attack, but multiple emails slip through before it starts quarantining the sudden influx of messages. In fact, enough emails get through for the mailbox owner to notice that their email is not behaving normally. The confusion and concern perfectly set the stage for the social engineering attack.
These email bomb + social engineering attacks are becoming more common because they work. By flooding inboxes, attackers create real-world stress that makes their scams more believable. Training your employees to recognize the attack and then quickly responding to shut it down is the key to prevention.
Unsubed and you don’t even know it
I pressed the publish button for the special edition (Stylometry Part 3) at 8:47 am on last Friday morning. By 8:49, I received seven “likes” and four “email disabled” notifications. That’s just two minutes—no one could have read the post and reacted so quickly, and no one could have completed the unsubscribe process that fast. All these events came from corporate email accounts. This reflects the behavior of security tools installed on corporate email systems. They are set to recognize newsletters and attempt to unsubscribe from them. Sometimes they succeed and hit the right button; other times, they mistakenly click “like” instead of “unsubscribe.” Eventually, they get it right. It’s common for me to meet people who say, “I loved your newsletter” or “I miss your newsletter.” Ah, it still exists—you just may not realize you’ve been unsubscribed. If you want to keep receiving the newsletter, you should subscribe from an email account you control.
The News…
During the government shutdown in October, there was a surge in scams where criminals impersonated government agencies, according to an Axios analysis. The Better Business Bureau reported 211 complaints about such scams, with scammers targeting services like passport renewals and government-backed loans. Experts warn that criminals are adapting their tactics to take advantage of the confusion caused by the shutdown, and some are now targeting SNAP recipients ahead of a funding freeze. https://www.axios.com/2025/11/02/government-imposter-scams-shutdown
International authorities have dismantled three major credit card fraud and money laundering networks under “Operation Chargeback,” affecting over 4.3 million cardholders across 193 countries. The operation resulted in the arrest of 18 individuals, including executives from major German payment service providers. The fraud involved creating 19 million fake subscriptions on online services and using shell companies to launder money; suspects from multiple countries were charged for their roles. https://www.bleepingcomputer.com/news/security/europol-credit-card-fraud-rings-stole-eur-300-million-from-43-million-cardholders/
Although written from a European perspective, this analysis is highly relevant to the United States as well. Russia is conducting "gray-zone aggression” against Western nations, employing tactics such as cyberattacks, drone incursions, and sabotage to deplete resources and raise the cost of operating in the West. These actions target infrastructure like undersea cables, airports, and shopping malls, resulting in notable financial losses for businesses and governments. https://www.politico.eu/article/russia-kremlin-donald-tusk-atm-poland-financial-losses/
Are you down with MCP? Yeah, you know me. https://www.akamai.com/blog/trends/2025/nov/ai-explainer-what-is-model-context-protocol
Bugcrowd purchased by Mayhem Security. https://www.prnewswire.com/news-releases/bugcrowd-acquires-mayhem-security-to-bring-human-augmented-ai-automation-to-security-testing-302603363.html
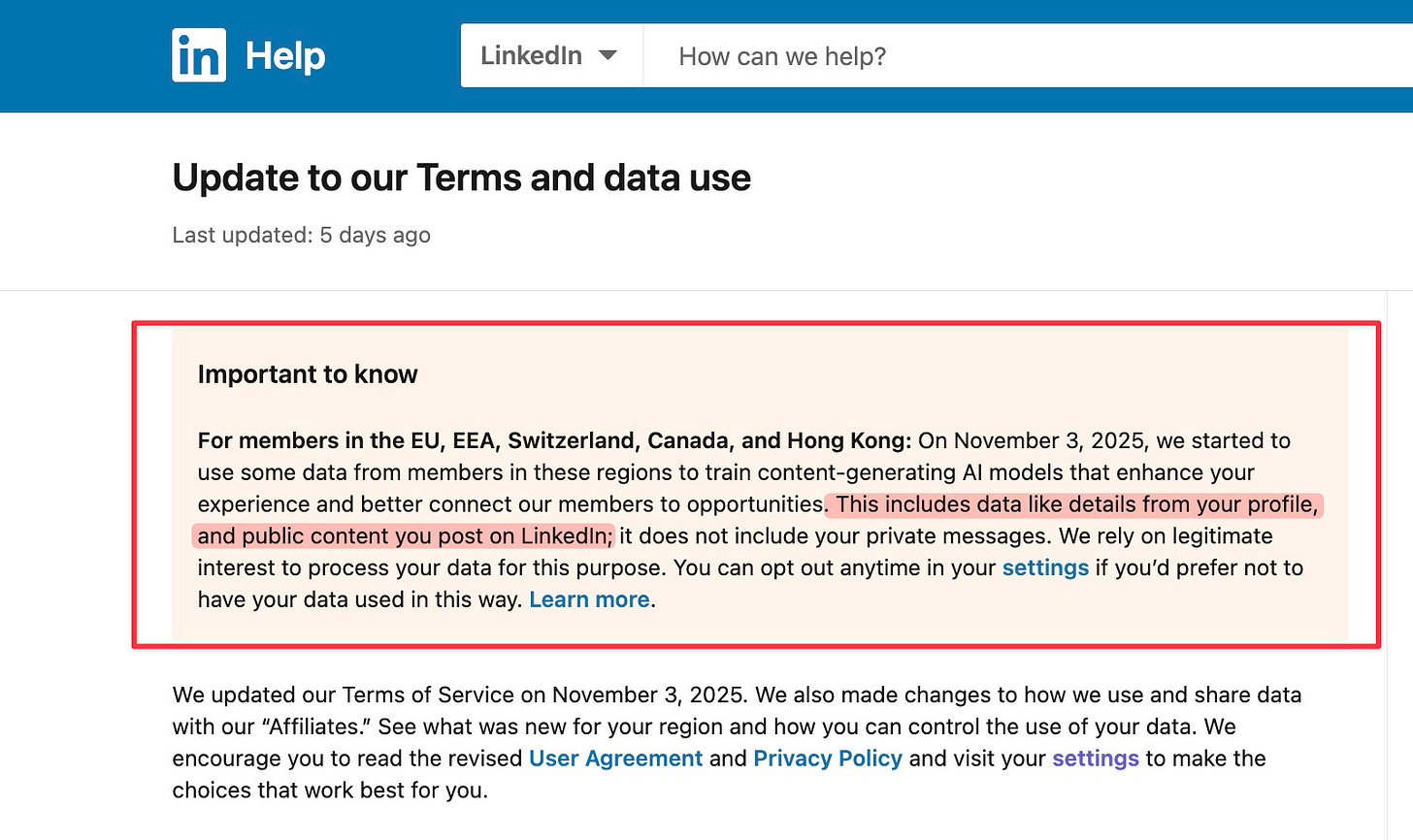
For all of you LinkedIn warriors… as of November 3, the company is using your profile information and written content to train AI models. They do give you the option to opt out.
Feedback: matt (at) threatswithoutborders.com
Cool Tool
WebRecon describes itself as an advanced Open Source Intelligence (OSINT) web reconnaissance tool designed for cybersecurity professionals, penetration testers, and security researchers. It automates the process of gathering intelligence from target websites through comprehensive crawling, data extraction, and analysis. (Python) https://github.com/techenthusiast167/WebRecon
Cool Job
Fraud Operations Manager, WSFS Bank. https://wsfsbank.wd1.myworkdayjobs.com/en-US/wsfscareers/job/Wilmington-DE/Fraud-Operations-Manager_R-103257-2
Financial Crime Manager (AML focus), Fanduel. https://www.fanduel.careers/jobs/fanduel/financial-crimes-manager/
DFIR
The Scientific Working Group on Digital Evidence (SWGDE) has recently published new draft documents and is seeking comments before releasing them in their final form. Two are of interest to the Tw/oB community. The first concerns Timing Advance Records for cellular providers, and the second concerns Best Practices for the Forensic Acquisition of Apple MacOS. https://www.swgde.org/documents/draft-released-for-comment/
Metadata Forensics perfectly explains why screenshots are not suitable evidence. https://metadataperspective.com/2025/11/04/metadata-matters-camera-original-photos-vs-screenshots-in-court/
Irrelevant
When kids put their phones down, they do something unimaginable: they talk. To each other no less. https://gothamist.com/news/ny-smartphone-ban-has-made-lunch-loud-again
This thesis was first proposed in 1987. Unsurprisingly, the Laws of Human Stupidity are still very applicable. https://gandalf.fee.urv.cat/professors/AntonioQuesada/Curs1920/Cipolla_laws.pdf
Sign Off
Thank you for reading. Seriously, I recognize the demand for your attention, and I appreciate that I get some of it each week. Make sure to read Friday’s special edition of the newsletter as we wrap up the Stylometry series. And I’ll see you all again next Tuesday.
Have a great week!
Matt
Published every Tuesday, Threats Without Borders offers original commentary and educational pieces related to cybercrime investigations and information security topics. We also summarize and comment on news articles concerning active threat intelligence for the financial industry. The newsletter interests everyone tasked with cybersecurity or involved in preventing or investigating technology-enabled fraud, theft, or money laundering.
Legal: I am not compensated by any entity for writing this newsletter. Obviously, anything written in this space is my own nonsensical opinions and doesn’t represent the official viewpoint of my employer or any associated organization. Blame me, not them.
cybersecurity cybercrime cyficrime osint financial fraud investigations aml