Threats Without Borders - Issue 274
Cybersecurity Investigations Newsletter, week ending February 15, 2026
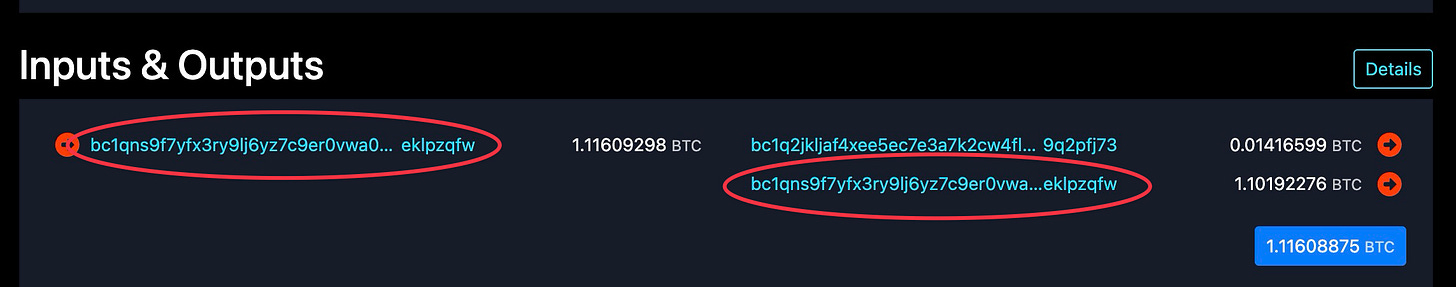
I am often asked why, when looking at a Bitcoin transaction where one address sends funds to another, there are sometimes two addresses on the output side - and sometimes it even looks like the sending address sent funds back to itself. It seems strange at first glance. Is something going wrong? Is it some kind of error?
One of the best analogies I’ve heard for explaining cryptocurrency transactions is doing business with gold bars.
Imagine you own a single 10 oz gold bar. You want to buy something from a merchant that costs 3 ounces of gold. Here is the problem: you physically cannot chip a 3-oz piece off a gold bar. You cannot hand over exactly 3 ounces from a 10-ounce bar. The whole bar has to go somewhere.
So what happens? The gold bar goes to the smelter. The smelter melts the gold bar down and pours the molten gold into new, smaller bars. Out come three new bars:
A 3-ounce bar that goes to the merchant -- this is your payment.
A 6.9-ounce bar that comes back to you -- this is your change.
A 0.1 ounce nugget is the fee paid to the smelter for their work.
The original 10-ounce bar no longer exists. It has been consumed, and three brand new bars have been created in its place.
In Bitcoin, your funds are not stored as a simple running balance like a bank account. Instead, they exist as individual chunks called UTXOs, which stand for Unspent Transaction Outputs. Think of each UTXO as one of those gold bars. You might have several of them of different sizes sitting in your digital wallet.
When you want to send Bitcoin to someone, your wallet picks one (or more) of those UTXOs to spend. Just like the gold bar, the entire UTXO must be consumed. You cannot spend just part of it. So the transaction does exactly what the smelter did:
The UTXO is fully spent as an input to the transaction.
A new output is created, sending the correct amount to the recipient.
A second new output is created, sending the leftover amount back to you -- this is your change.
A small amount is claimed by the miners (the people who process Bitcoin transactions) as their fee.
When you look at a Bitcoin transaction on a block explorer and see two output addresses, you are almost always looking at the recipient and the change going back to the sender.
So why does the change sometimes go back to the same address, but sometimes a new one? The answer is simple: it depends entirely on which wallet software is being used.
Older, less technical wallets, and some exchange platforms will send your change right back to the address you sent from. It is the equivalent of the smelter handing your change bar back to you in exactly the same labeled pouch you gave them. Easy to track, easy to understand.
You will also see this with some business accounts and exchange-managed wallets, where the platform keeps things neat by always cycling funds back to a known address.
More modern (secure) wallets automatically generate a brand new, never-before-used address to receive your change. This address still belongs entirely to you and is controlled by the same wallet and the same seed phrase. You do not need to do anything special to access those funds. Your wallet knows about it automatically.
Blow your whistle
The U.S. Treasury has introduced a new website for whistleblowers to report fraud, money laundering, and sanctions violations. Rewards will range from 10% to 30% of collected fines from successful enforcement actions. FinCEN will oversee the program, which includes violations of the Bank Secrecy Act, U.S. sanctions, and other financial laws, while the IRS will create a dedicated task force to investigate misuse of funds by tax-exempt organizations. https://www.fincen.gov/whistleblower/
Timely
Back in Issue 271, we looked at Pastebin sites and examined how criminals use them to facilitate cybercrime.
A new crypto scam exploits Pastebin comments to spread a ClickFix-style attack targeting crypto users. Scammers post comments with links to fake guides promising a profitable arbitrage opportunity. They trick victims into manually running malicious JavaScript code in their browser’s address bar. Once executed, the code hijacks the legitimate swap interface by replacing Bitcoin deposit addresses with wallets controlled by attackers and adjusting exchange rates to make the fake exploit seem real, leading to theft of victims’ cryptocurrencies. https://www.bleepingcomputer.com/news/security/pastebin-comments-push-clickfix-javascript-attack-to-hijack-crypto-swaps/
The News…
Chainalysis reports that cryptocurrency flows to suspected human trafficking services surged 85% in 2025, reaching hundreds of millions of dollars, primarily through Southeast Asian operations linked to Chinese-language money laundering networks on Telegram. https://www.chainalysis.com/blog/crypto-human-trafficking-2026/
It seems like only yesterday we were discussing Lockbit 2.0 and now we’re faced with Lockbit 5.0. What’s that saying, time flies when we’re… https://www.acronis.com/en/tru/posts/lockbit-strikes-with-new-50-version-targeting-windows-linux-and-esxi-systems/
A warning for all Mac “fanboys” (myself included): A thriving macOS infostealer economy is emerging, with attackers innovating specifically for Apple’s ecosystem. Flare explains that the assumption that Macs are immune to viruses is outdated and dangerous. https://flare.io/learn/resources/blog/the-macos-stealer-gold-rush-how-cybercriminals-are-racing-to-exploit-apples-ecosystem
To absolutely no one’s surprise, cybercriminals are using AI website builders to clone major brands, creating convincing fake sites to lure victims. These sites are used for credential harvesting, payment fraud, and malware delivery. The ease of use and lack of robust security measures in AI website builders enable attackers to create and deploy these scams rapidly. https://www.malwarebytes.com/blog/news/2026/02/criminals-are-using-ai-website-builders-to-clone-major-brands
Bitcoin exchange Paxful has been fined $4 million for transferring funds tied to money laundering, fraud, and sex trafficking. https://www.justice.gov/opa/pr/virtual-asset-trading-platform-sentenced-violating-travel-act-and-other-federal-criminal
There isn’t much left of CISA, but the remaining holdouts published the agency’s 2025 Year-In-Review report. https://www.cisa.gov/about/2025YIR
Posted without comment. https://techcrunch.com/2026/02/13/sex-toys-maker-tenga-says-hacker-stole-customer-information/
Cool Job
For those that like snow… Fraud Coordinator - Erie Federal Credit Union. https://eriefcu.acquiretm.com/job_details_clean.aspx?id=1676
Cool Tool
Reverse image search (you might get ads depending on your browser) https://picdetective.com/
DFIR
Jordan Mussman provides “a practical field guide to macOS security architecture and forensic artifacts for incident responders investigating compromised MacBooks in 2026”. https://jmussman.net/posts/mac_dfir/
Irrelevant
The best science I’ve read in a long time.
https://jamanetwork.com/journals/jama/fullarticle/2844764
Sign off
I was told twice last week that I should consider teaching technology investigations full-time. Maybe. But I fear people wouldn’t pay to listen to me run my mouth for a day or three. I expect to issue refunds around 2:30PM on the first day.
Besides, if I worked for myself, I wouldn’t get paid time off for bank holidays!
Have a great week.
Matt
matt @ threatswithoutborders.com
Published every Tuesday, Threats Without Borders offers original commentary and educational pieces related to cybercrime investigations and information security topics. We also summarize and comment on news articles concerning active threat intelligence for the financial industry. The newsletter interests everyone tasked with cybersecurity or involved in preventing or investigating technology-enabled fraud, theft, or money laundering.
Legal: I am not compensated by any entity for writing this newsletter. Obviously, anything written in this space is my own nonsensical opinions and doesn’t represent the official viewpoint of my employer or any associated organization. Blame me, not them.